Featured Posts
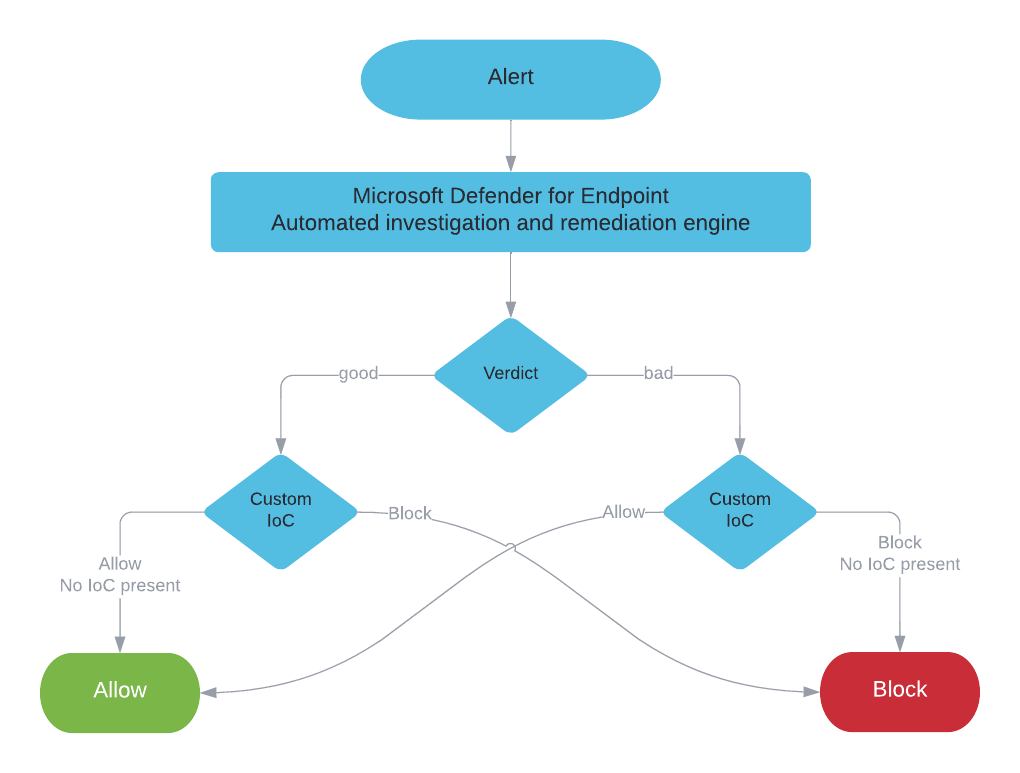
Since Microsoft Defender for Endpoint is a suite of products, rather than just one single piece of software, there are various places where you can create exclusions for different features. Also, there are integrations in other products, that result in possible side effects when enabling certain settings.
Most of these products have separate documentations, there is no single documentation page that contains all the information about exclusions available in Microsoft Defender for Endpoint.
Creating and maintaining a secure environment is hard. And with every technology or product added to your environment it gets more complicated. Microsoft Azure as a cloud environment is no exception to this rule and with the many services and features that get added every year it just gets more complicated even if you did not change a thing. Because keeping your IT assets secure is important as you move to the cloud, it is important to know which bad practices to avoid and which attack scenarios are out there.
Neuste Posts
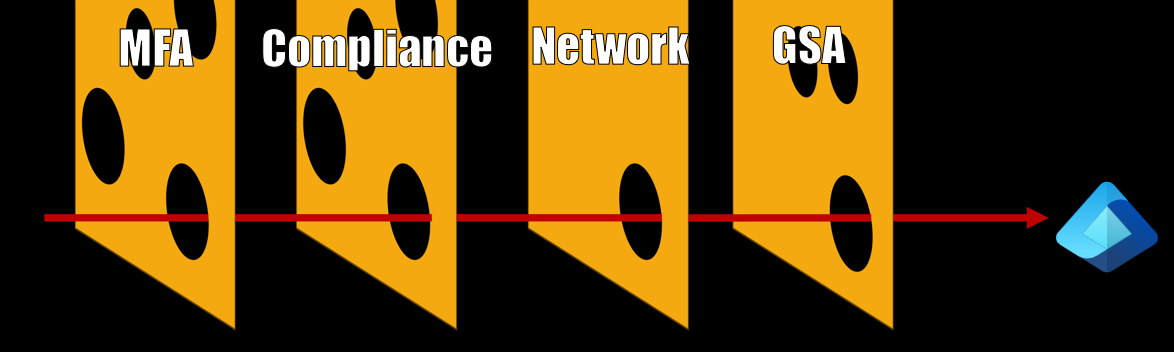
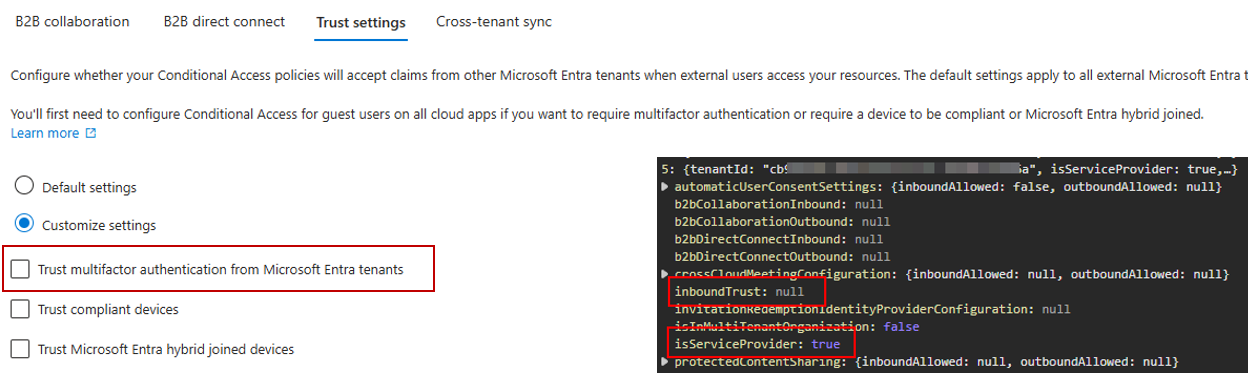
In Microsoft Entra, Conditional Access is, after the Authentication itself, the most crucial part of defense against attackers. It’s referenced as “zero trust policy engine” and the idea behind is, that in addition to your username and password you can also enforce additional requirements when you access a specific resource.
This could be any combination of
a second factor (2FA), a specific authentication method (e.g. passkey) a device that is in a “compliant” state a trusted or compliant network and a lot more, depending on your specific use case.
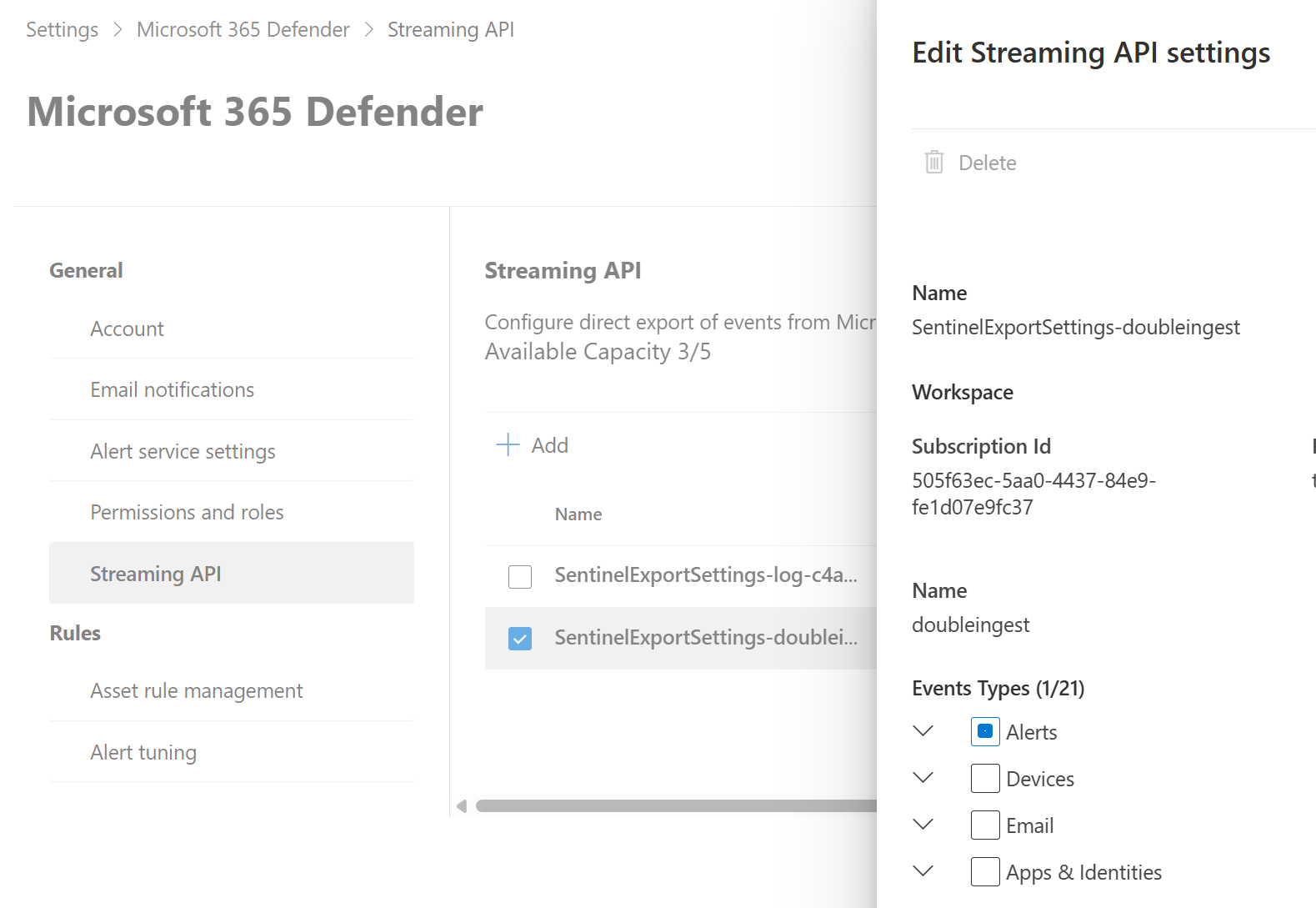
This blog post is a sleeper. I documented it in 2023 and never came around to publish it. The post was always too short in my opinion, too niche. But today Jonathan Bourke reached out on Twitter and asked why he was getting this strange error message when trying to connect a new Sentinel workspace to his XDR instance.
Warnung The limit of 5 diagnostic settings was reached. To create new setting ‘SentinelExportSettings-log-sentinel’, delete an existing one.
For a long time now, defenders had the ability to monitor behavior of human- and workload identities in Entra tenants not only through AuditLogs but with high level of insight with the MicrosoftGraphActivityLogs logs. The last two articles of this series gave you detection ideas and hunting queries for this logs source and were meant as a kick starter for detection engineers. But in the end the high cost of this log prevented many companies from putting it into operation.
Ho, ho, ho… In Germany on the 6th of December we celebrate “Nikolaus”. Kids put out one shoe the night before in the hopes that, in the morning, it is filled with nuts, mandarin oranges, chocolate or even small gifts. Lucky for you, it seems that you also put out your shoe last night, because I have a gift for you as well. But please don’t confuse me with Nikolaus ;)
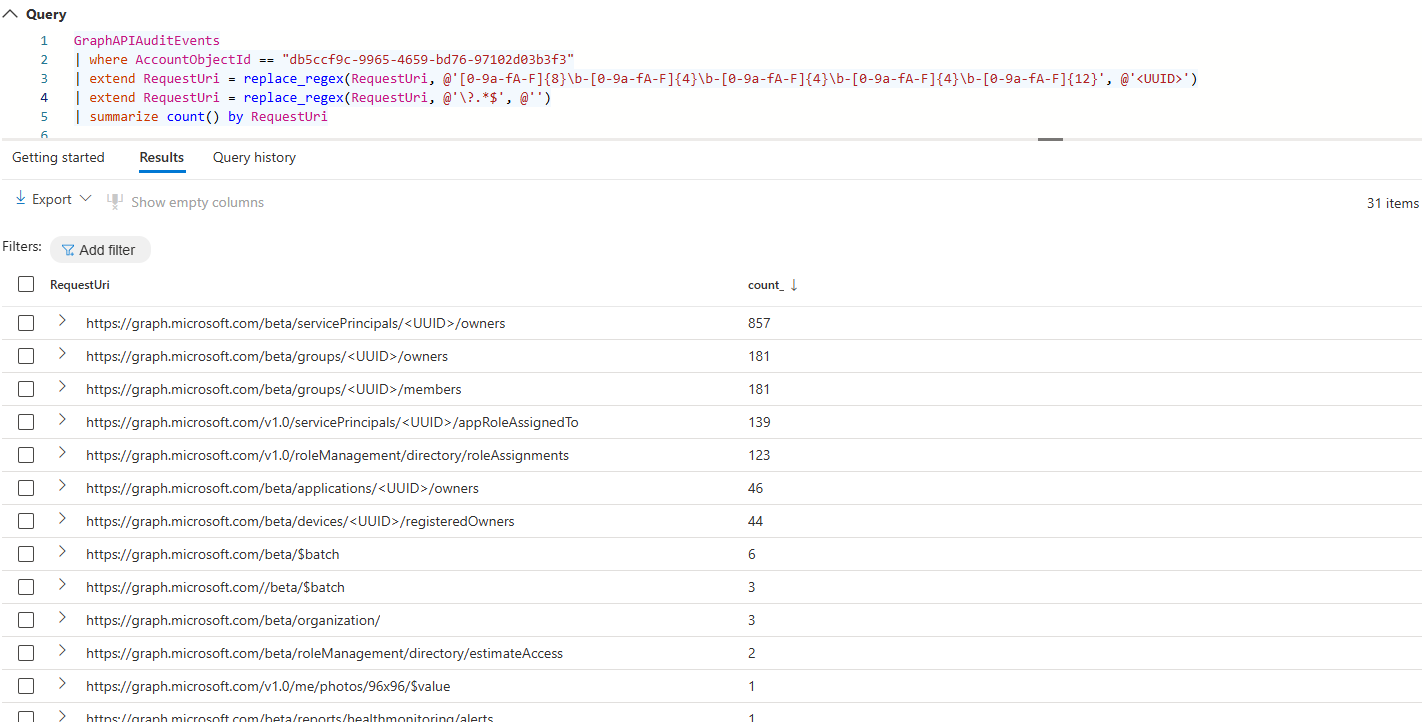
For red teams and adversary alike it’s important to stay hidden. As many companies nowadays have EDR agents deployed those agents are always in focus and tools like EDRSilencer or EDRSandblast use different techniques to prevent further communications of the EDR agent with the log ingestion endpoint.
A few weeks ago Mehmet Ergene and I were discussing other ways to prevent agent communications and ways to detect such tampering. The idea for a a two part blog post was born.
Entra ID Multifactor Authentication is on everyone’s mind, as Microsoft will enforce the usage of MFA for most of the Admin portals starting October 2024. But many in the industry are a step ahead and had MFA enforced already and are thinking about how to make MFA more convenient for everybody involved.
Let me introduce you to cross-tenant access settings for B2B collaboration and especially inbound trust settings for MFA. With this you can configure if you trust another tenants MFA configuration and don’t require the users from this tenant to setup a second set of MFA in your tenant.