Gradual rollout process for Microsoft Defender
One of the features of Microsoft Defender Antivirus that, in my opinion, is overlooked by most, is the ability to control the rollout of all components of Microsoft Defender Antivirus by selecting different release channels. This allows for a more gradual rollout of security intelligence updates, the engine as well as the AV platform.
Different update types
But let’s take a step back and get a common understanding whats the difference between those different updates is and how they are deployed.
| Update type | Description | Release cadence | Deployment |
|---|---|---|---|
| Security intelligence updates | Contains new and updated malware detections. | Multiple times a day | Deployed using KB2267602 through the Microsoft update channels. You can find the related release notes here |
| Engine updates | Contains update to the core detection engine | Monthly | Deployed as part of the security intelligence updates |
| Platform updates | Updates to the product itself. It can contain new features as well as fixes for existing ones. | Monthly | Deployed using KB4052623 through the Microsoft update channels. Check this website for release notes. |
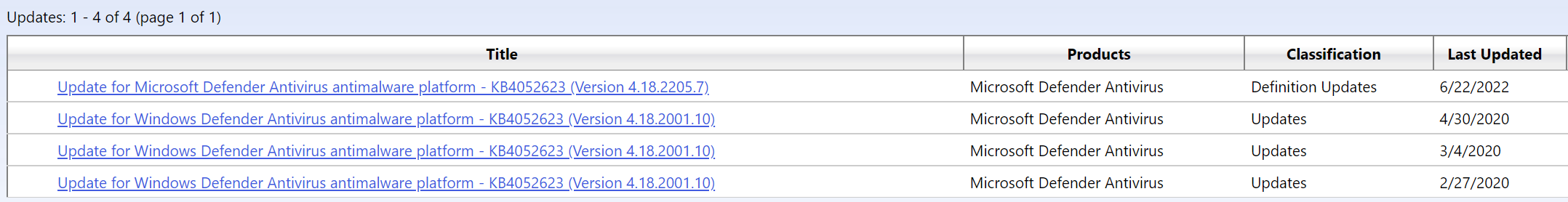
You can check which are the current versions on this website or, if you need the information inside of a script, use this snippet.
Invoke-RestMethod -Uri "https://www.microsoft.com/security/encyclopedia/adlpackages.aspx?action=info" | Select -ExpandProperty versions

Be aware that the Microsoft Update Catalog contains more than one version of the platform update. Version 4.18.2001.10 is a important update for Windows Server 2016 because it is needed before you can install any newer platform version.
%OSDrive%\ProgramData\Microsoft\Windows Defender\Platform\. The previous version is kept in case a rollback is necessary.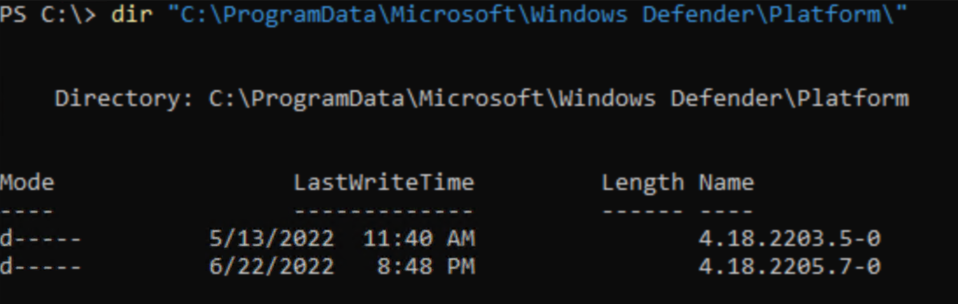
Attribution
A big thanks goes out to Paul @Threatzman Huijbregts (Senior PM at Microsoft) who double checked my info graphic below. If you want a look behind the curtain of Microsoft Defender for Endpoint and it’s history inside of Microsoft, you should follow him on Twitter and wait for the release of #thebookofmde he and Joe @trk_rdy are currently writing.
Gradual rollout process
Many companies don’t want to update all their devices at the same time to the most current version of a product. Especially when talking about signature updates a staged rollout can minimize the impact of the detection of false positives.
But also a new engine update or platform update could introduce unwanted side effects on your devices and testing is therefore important.
If you want a bit more control over at which stage of the global rollout the updates hit your devices you are in luck. Microsoft has made the process of gradually rolling out those updates super easy in June of 2021, when they introduced the ability to choose update channels in the Microsoft Defender Antivirus settings.
Using either Intune, Group Policies or PowerShell you can set an update channel for each of your devices or better device groups and even differentiate between channels for the different update types.
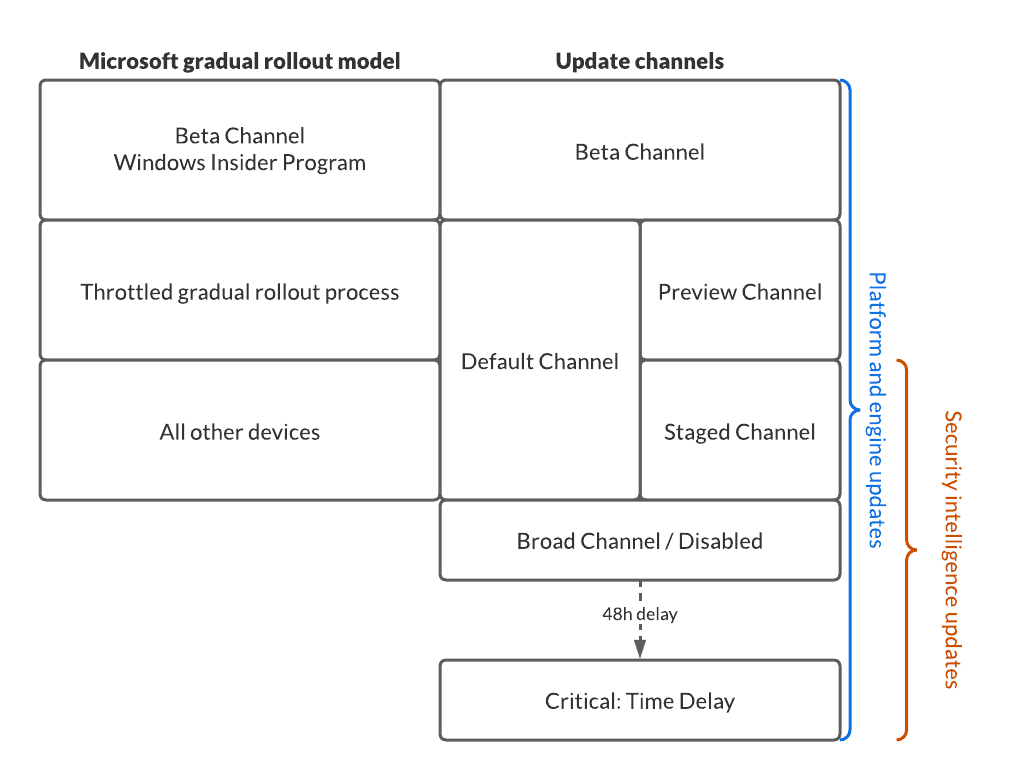
If you choose to completely disable gradual rollout (which you shouldn’t), the device will be set in the broad channel. This is not a good option if you do not have any devices in other channels, because it limits your ability to detect any problems before they hit all devices.
If you don’t want to configure a gradual rollout, just let the configuration untouched and you will use the Microsoft gradual rollout model (MGRM).
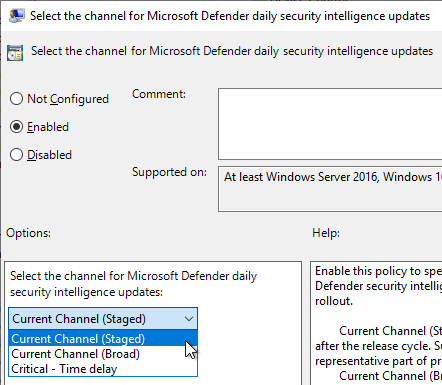
Security intelligence updates
Setting name: SecurityIntelligenceUpdatesChannel
| Channel | Description | Value |
|---|---|---|
| Staged | The devices in this channel will receive the updates at the end of the MGRM. This should be the default for most client devices. |
4 |
| Broad / Disabled | Updates are offered after the MGRM has completed. Use this only on datacenter servers. |
5 |
| Critical: Time Delay | Security intelligence updates are delivered with a 48 hour delay to the clients. Try to avoid this if there is not a really good reason. Your protection capabilities will be 48 hours late. |
6 |
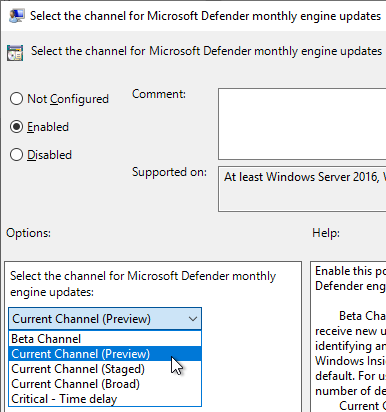
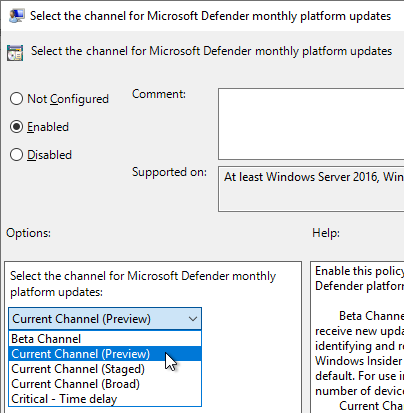
Platform and engine updates
Setting name: PlatformUpdatesChannel + EngineUpdatesChannel
| Channel | Description | Value |
|---|---|---|
| Beta | Receive updates as soon the they are released. This is also what Windows Insiders are testing. Use it only on a small, handpicked set of IT savvy users. |
2 |
| Preview | Updates are installed very early in the MGRM and therefore are suited for pre-production environments to verify any impact. | 3 |
| Staged | Updates are installed later in the MGRM. This should be the default for a majority of devices. |
4 |
| Default | By default all devices will receive updates wither during the Preview or Staged phase. | |
| Broad / Disabled | After the MGRM has completed those devices will receive updates. Use this only if there is a good reason to delay the rollout and only use it on datacenter servers. |
5 |
| Critical: Time Delay | Devices in this channel will receive updates with a 48 hour delay. Only on critical datacenter servers with no HA capability. |
6 |
Since I like to visualize stuff for a better understanding, I created this overview of how the different channels and settings align with the Microsoft gradual rollout
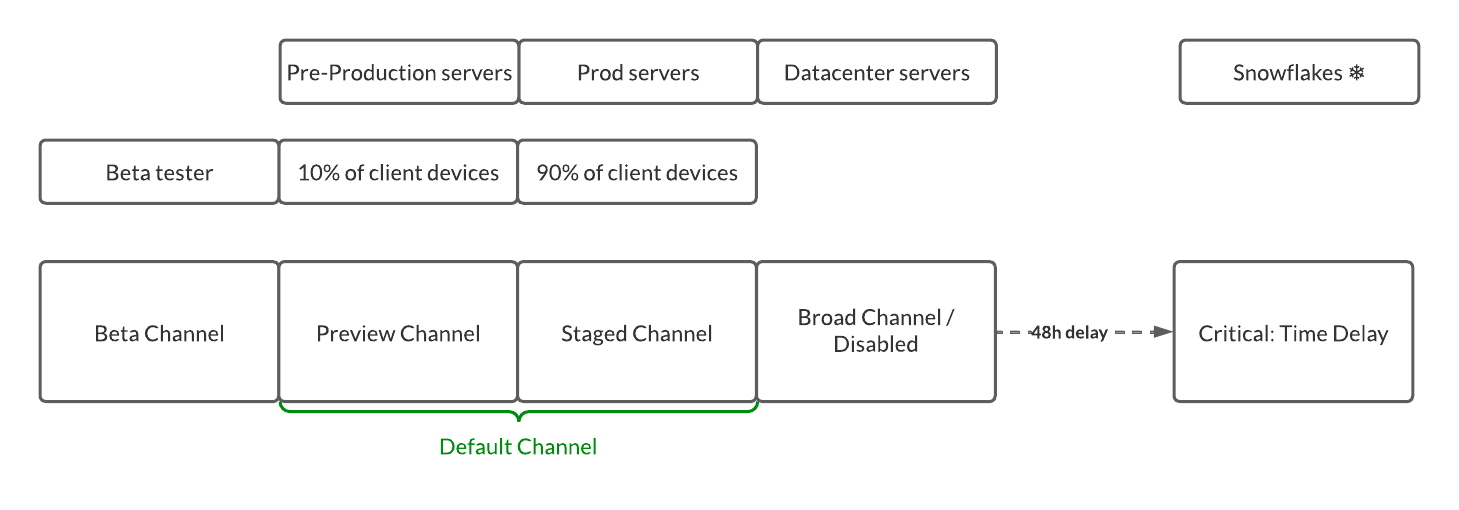
Assign devices to channels
The following diagram display a sample option on how you could assign your devices to specific channels. This is just a rough guidance and you will have to check your requirements to see if this fits your needs, you do you.
Group Policy
Download the most current ADMX/ADML files and put them into your PolicyStore folder. To my knowledge this would be the files in the Device Control GitHub repository.
Create a new group policy and select the appropriate settings and assign the GPO to the device group of you choise.

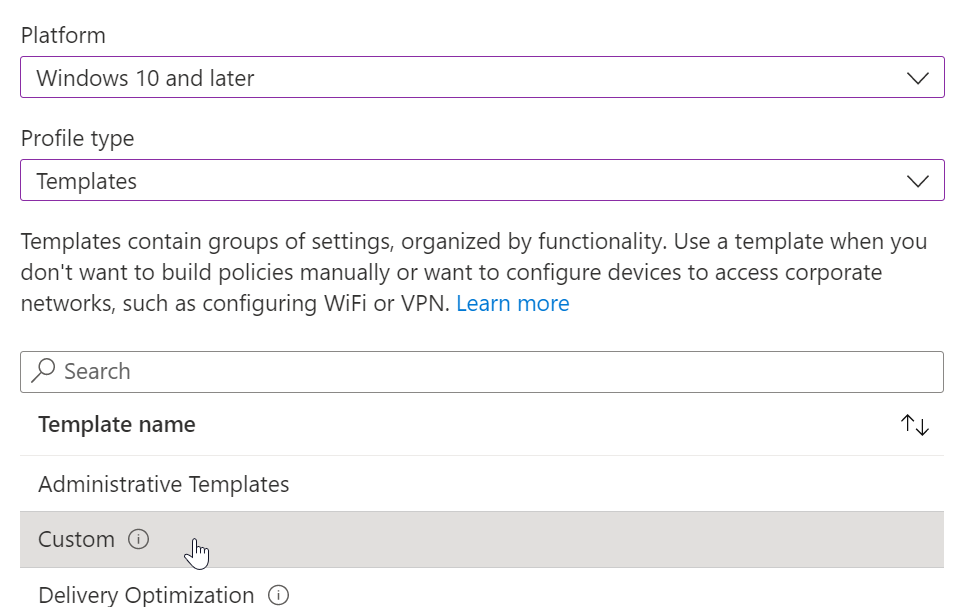
Intune configuration
At the time of writing this blog post the settings are only available using a custom template. They are not part of the settings catalog nor Endpoint security. To check available values head over to the Defender CSP definition.
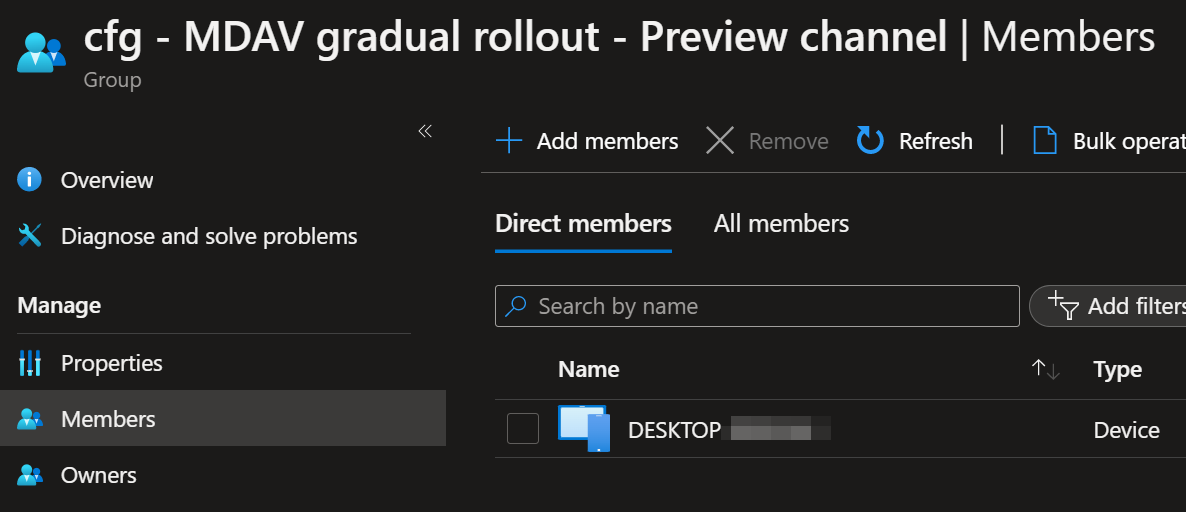
First create a new Entra ID (Azure AD) security group for the respective channel and assign the computers to it.
Head over to Intune and create a new custom template.
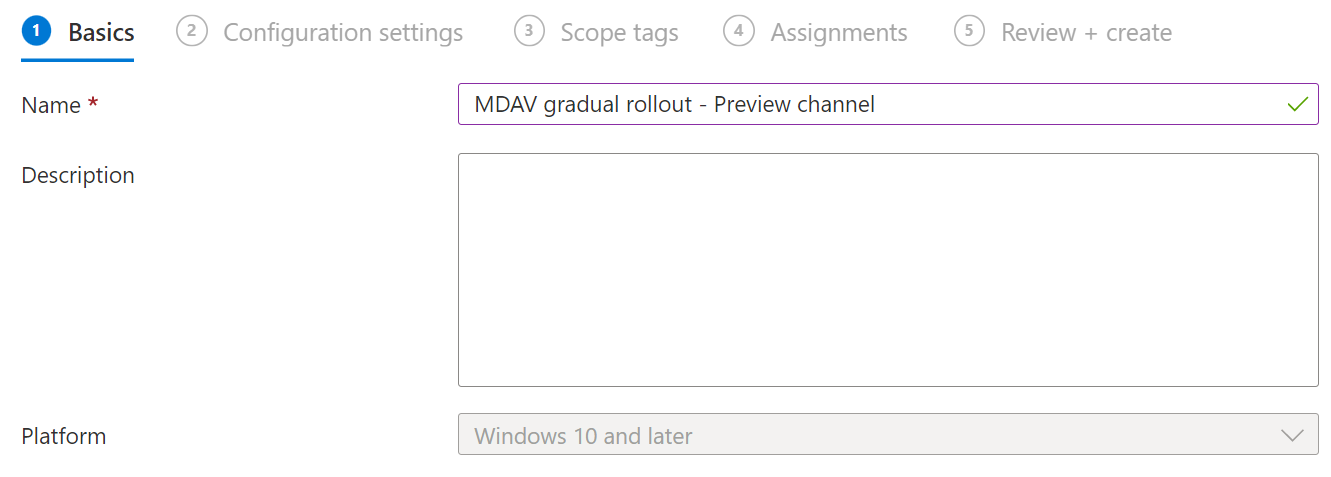
Assign a name to the configuration profile
Create the respective entries for each OMI-URI.
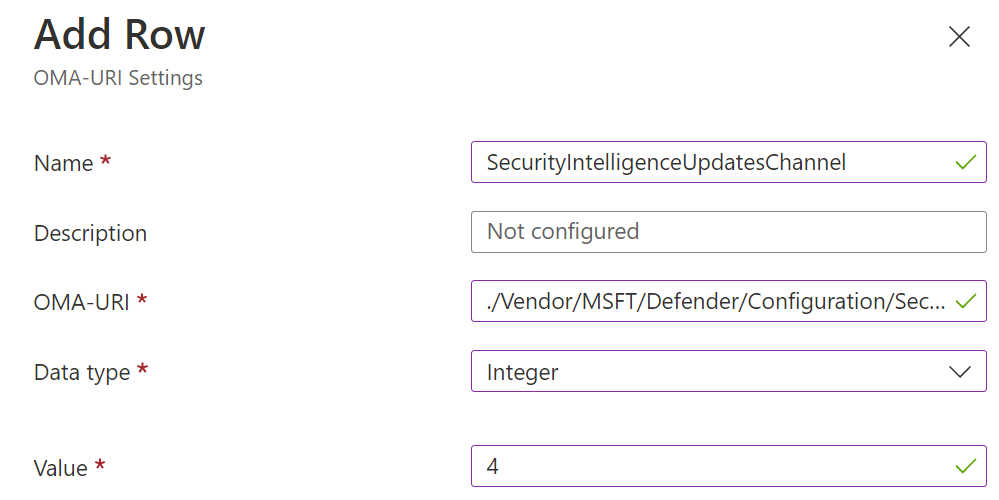
| OMI-URI | Data type | Value |
|---|---|---|
| ./Vendor/MSFT/Defender/Configuration/SecurityIntelligenceUpdatesChannel | Integer | 3 (Preview) |
| ./Vendor/MSFT/Defender/Configuration/PlatformUpdatesChannel | Integer | 3 (Preview) |
| ./Vendor/MSFT/Defender/Configuration/SecurityIntelligenceUpdatesChannel | Integer | 4 (Staged) |
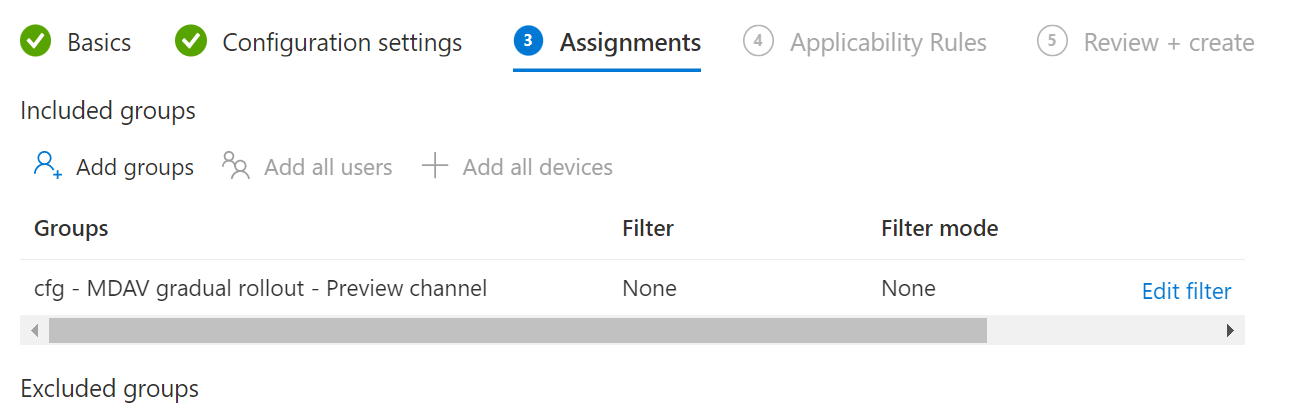
Assign the earlier created device group and finish the creation of the configuration profile.
Check your settings
Client side
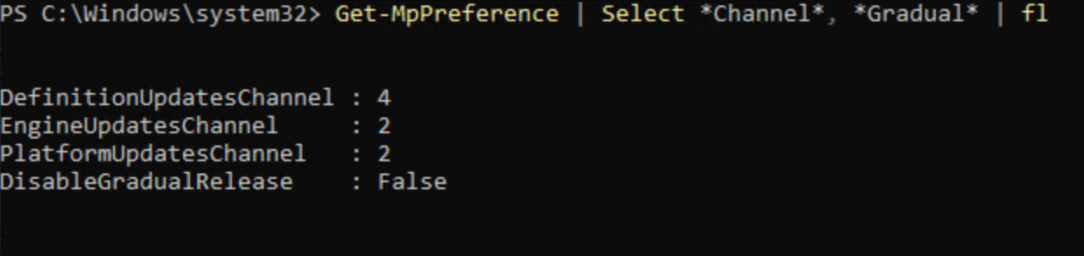
Use Get-MpPreference to verify that your new settings are correctly applied. Currently the cmdlet will return the integer values that you used in the custom Intune OMI configuration.
Get-MpPreference | Select *Channel*, *Gradual* | Format-List
Advanced hunting
let AvModeDescription = dynamic({"0":"Normal", "1":"Passive", "4":"EDR Block"});
let RingDescription = dynamic({ "2":"Beta", "3":"Preview", "4":"Staged", "5":"Default-Manual", "6":"Critical: Time Delay"});
DeviceTvmInfoGathering
| extend AdditionalFields = parse_json(AdditionalFields)
| extend AvEngineVersion = tostring(AdditionalFields.["AvEngineVersion"])
| extend AvPlatformVersion = tostring(AdditionalFields.["AvPlatformVersion"])
| extend AvMode = tostring(AvModeDescription[tostring(AdditionalFields.["AvMode"])])
| where isnotempty( AvMode )
| extend AvEngineRing = tostring(RingDescription[tostring(AdditionalFields.["AvEngineRing"])])
| extend AvEngineRing = iff(isempty(AvEngineRing),"Default",AvEngineRing)
| extend AvSignatureRing = tostring(RingDescription[tostring(AdditionalFields.["AvSignatureRing"])])
| extend AvSignatureRing = iff(isempty(AvSignatureRing),"Default",AvSignatureRing)
| extend AvPlatformRing = tostring(RingDescription[tostring(AdditionalFields.["AvPlatformRing"])])
| extend AvPlatformRing = iff(isempty(AvPlatformRing),"Default",AvPlatformRing)
| project-away AdditionalFields, Timestamp, LastSeenTime, DeviceId