Create a Network Trace Without Wireshark
Wireshark is a powerful tool to analyze network data. However, it is another tool that needs to be regularly updated and that relies on additional software (Npcap) to capture network data.
But Windows has a built-in tool to create a network trace. And with a small additional tool the created etl file becomes a pcap file which can be analyzed without any problems. An installation of Wireshark and Npcap is therefore not necessary to capture the data.
netsh
netsh is a very old tool in Windows and the command netsh trace is exactly what we are looking for. With this command you can control the trace provider ndiscap.
trace start
netsh trace start report=disabled capture=yes tracefile=C:\NetworkTraceFull.etl
The individual parameter have the following effect:
trace start- Starts the actual trace and is further configured with the following parameters.report=disabled- Prevents that the data are summarized into a cab file.capture=yes- Declares that the network data should be recorded.tracefile=C:\NetworkTrace.etl- If not specified the default path “%LOCALAPPDATA%\Temp\NetTraces\NetTrace.etl” is used.
trace stop
After the desired data has been collected, the trace can be stopped.
netsh trace stop
The resulting etl file now needs to be prepared for further analysis.
Advanced capture filter
If network traffic is to be further restricted, to analyze only the connection to and from a specific machine, capture filters can be used.
Only traffic between two servers
netsh trace start report=disabled capture=yes tracefile=C:\NetworkTraceIPAddress.etl IPv4.Address=161.97.153.201 Ethernet.Type=IPv4
Ignore one IP address
netsh trace start report=disabled capture=yes tracefile=C:\NetworkTraceNotIPAddress.etl IPv4.Address=!(161.97.153.201)
Additional filter
A complete list with all filters is provided by the following command
netsh trace show CaptureFilterHelp
etl2pcapng
For the conversion to pcapng format we use the tool etl2pcapng. The installation of the Microsoft Message Analyzer is thus no longer required.
You can download the binaries here.
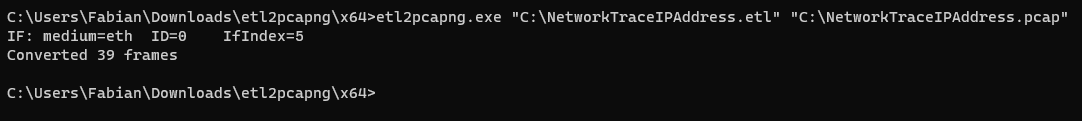
Only two values need to be specified. The file path of the ETL file and the output location of the PCAP file.
etl2pcapng.exe "C:\NetworkTraceIPAddress.etl" "C:\NetworkTraceIPAddress.pcap"
Analyse
For further analysis, any tool that can handle pcap files can be used, e.g. Wireshark Portable in a virtual machine.
The warning message that no capture drivers are available can be safely ignored.