Featured posts
Since Microsoft Defender for Endpoint is a suite of products, rather than just one single piece of software, there are various places where you can create exclusions for different features. Also, there are integrations in other products, that result in possible side effects when enabling certain settings.
Most of these products have separate documentations, there is no single documentation page that contains all the information about exclusions available in Microsoft Defender for Endpoint.
Creating and maintaining a secure environment is hard. And with every technology or product added to your environment it gets more complicated. Microsoft Azure as a cloud environment is no exception to this rule and with the many services and features that get added every year it just gets more complicated even if you did not change a thing. Because keeping your IT assets secure is important as you move to the cloud, it is important to know which bad practices to avoid and which attack scenarios are out there.
Latest posts
Ho, ho, ho… In Germany on the 6th of December we celebrate “Nikolaus”. Kids put out one shoe the night before in the hopes that, in the morning, it is filled with nuts, mandarin oranges, chocolate or even small gifts. Lucky for you, it seems that you also put out your shoe last night, because I have a gift for you as well. But please don’t confuse me with Nikolaus ;)
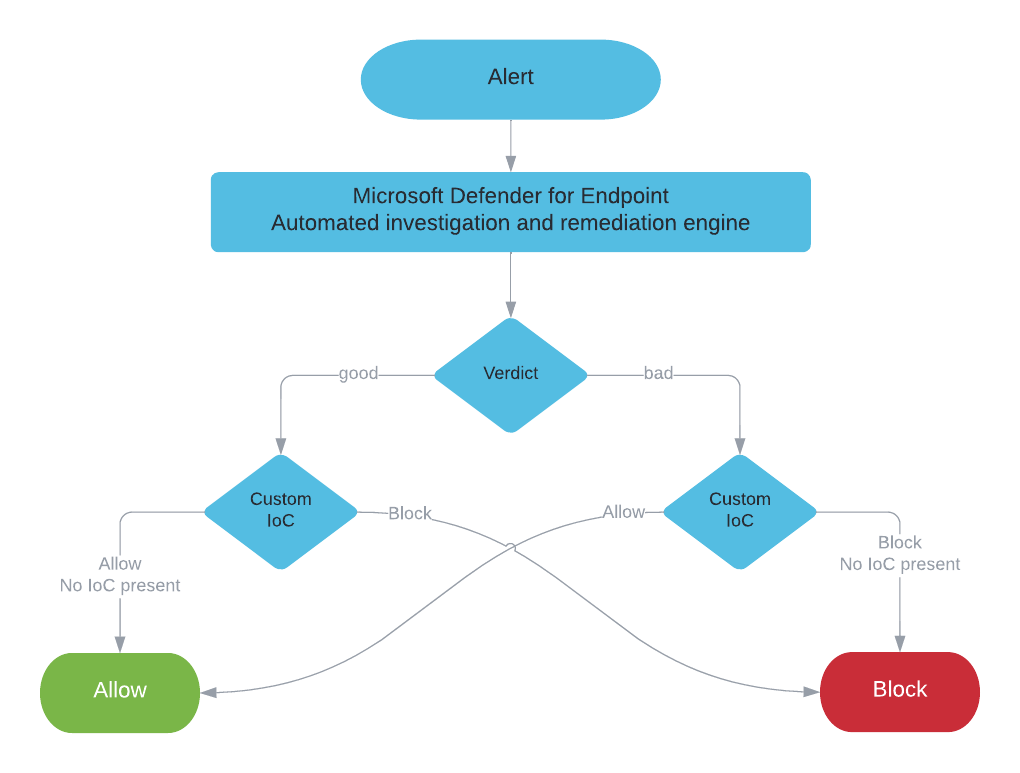
For red teams and adversary alike it’s important to stay hidden. As many companies nowadays have EDR agents deployed those agents are always in focus and tools like EDRSilencer or EDRSandblast use different techniques to prevent further communications of the EDR agent with the log ingestion endpoint.
A few weeks ago Mehmet Ergene and I were discussing other ways to prevent agent communications and ways to detect such tampering. The idea for a a two part blog post was born.
Entra ID Multifactor Authentication is on everyone’s mind, as Microsoft will enforce the usage of MFA for most of the Admin portals starting October 2024. But many in the industry are a step ahead and had MFA enforced already and are thinking about how to make MFA more convenient for everybody involved.
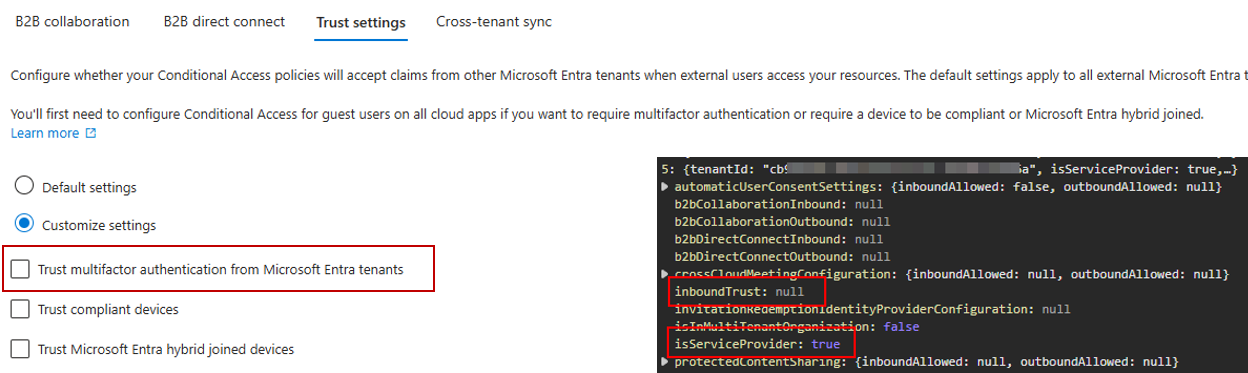
Let me introduce you to cross-tenant access settings for B2B collaboration and especially inbound trust settings for MFA. With this you can configure if you trust another tenants MFA configuration and don’t require the users from this tenant to setup a second set of MFA in your tenant.
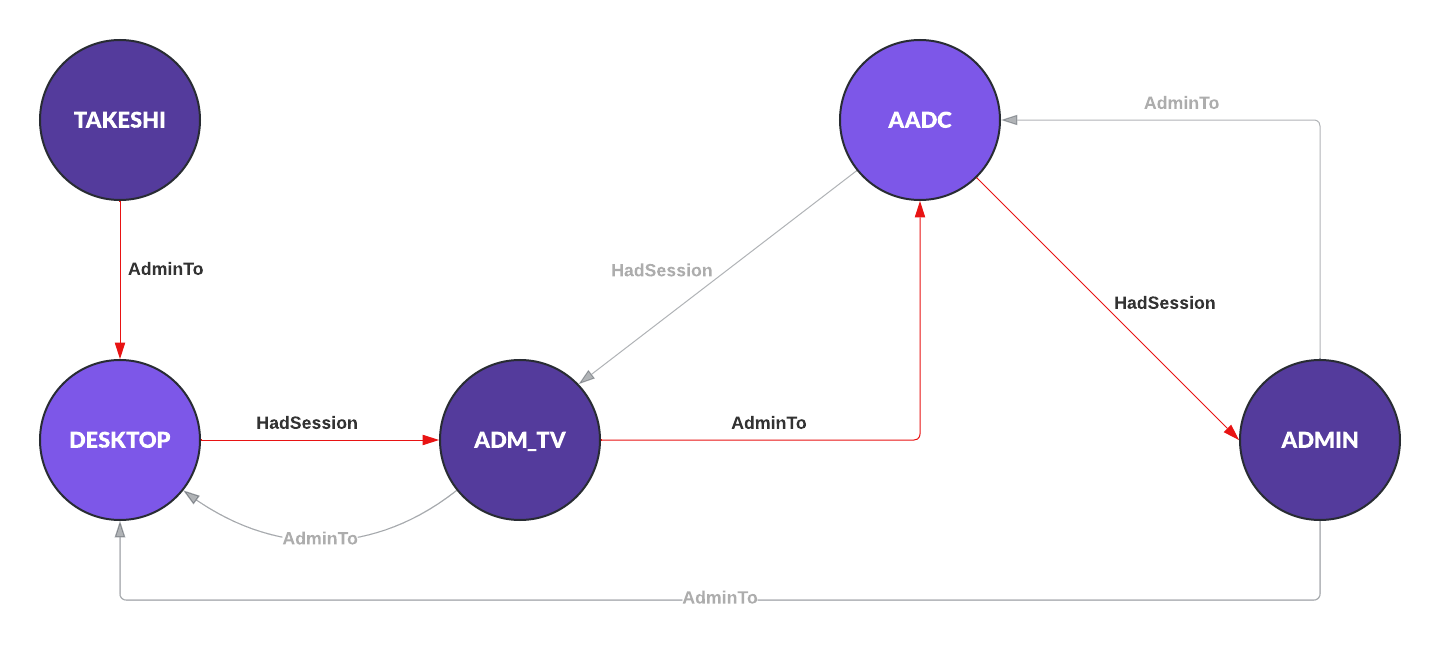
Graph databases offer great insights into existing data, that relational databases cannot or can only solve with more resources. Tools that leverage this ability to find lateral movement paths (edges) between user, computers and other entities (nodes) like Bloodhound offer an amazing data source for red teams and blue teams alike. But still the use in the defender world is yet limited. This might be because blue teams don’t like to use red teamers toolkit (really?
Microsoft Defender for Cloud Apps is one of the many puzzle pieces of the Microsoft XDR solution that helps you to secure your corporate environment. While Defender for Endpoint and Defender for Office 365 may be the more prominent names in this puzzle, Defender for Cloud Apps has a few aces up it’s sleeve that help you to protect access to corporate data on a complete other level.
Many of you might already know the cloud discovery capabilities, which help you to get a deep insight into your companies usage of Software as a Service solutions.
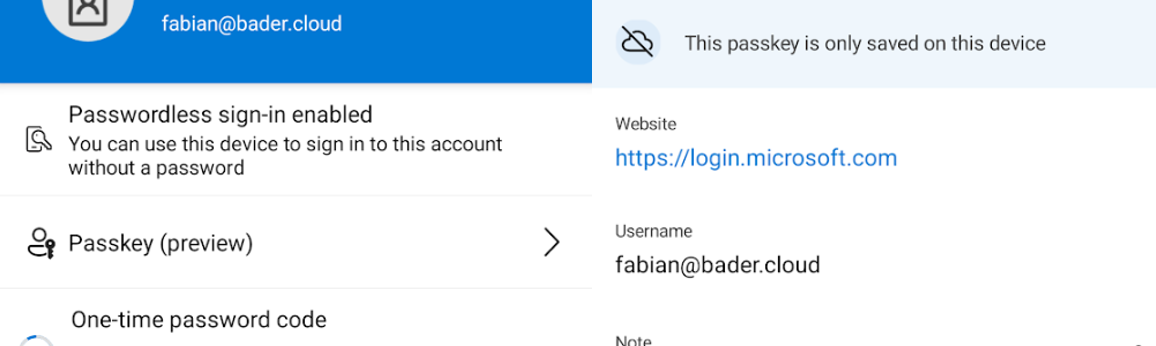
With the release of the public preview for Passkey in Entra ID, I think, the broad adoption of passwordless and phishing resistant authentication adoption in the enterprise is coming close. Of course we had phishing resistant, passwordless methods available before. FIDO2 security keys are already a supported way to sign-in to Entra ID. But realistically this was always just for the technical savvy, the admins and power users and there were still limitations on mobile platforms.