Data Protection Made a Breeze: MDA integration in Edge for Business
Microsoft Defender for Cloud Apps is one of the many puzzle pieces of the Microsoft XDR solution that helps you to secure your corporate environment. While Defender for Endpoint and Defender for Office 365 may be the more prominent names in this puzzle, Defender for Cloud Apps has a few aces up it’s sleeve that help you to protect access to corporate data on a complete other level.
Many of you might already know the cloud discovery capabilities, which help you to get a deep insight into your companies usage of Software as a Service solutions.
But the hidden champion is the Conditional Access App Control feature.
Conditional Access App Control
Using this feature you can, depending on conditions you can define in a Conditional Access policy, steer users not directly to the regular endpoint of the application, but to a service that functions like a reverse proxy. This way every interaction sent from the user to the SaaS will be first terminated there and you can add additional protections, logging and controls, that otherwise would not be possible.
Session policies
Supported controls that can be configured through these session policies include blocking the user to upload/download files or prevent copy/paste of website data.
This way you can keep your companies data from being extracted on an unmanaged device or from a unknown location while still allowing read only access for the user.
Reverse proxy
As with every reverse proxy based solution the traffic must route through an additional hop before it can terminate at the final service. This can introduce additional latency and some controls, that solely rely on the uncontrolled web browser, might not always work as expected. The user might still be able to open the developer tools and inspect the source code of the website, the network traffic and more.
Therefore Microsoft introduced, in public preview, a new way to provide fast and secure access:
The integration of those features in Edge for Business.
This solved the dilemma of the reverse proxy and since Microsoft now controls the browser as well as the session policies, it’s possible to enforce them directly on the endpoint. This extends the protection by disabling the developer tools when accessing corporate data. As mentioned before, if not disabled, the developer tools can be a security issue if essential data like session or access token are exposed in the network data.
Removing the reverse proxy also reduces the latency and therefor your users will have a much better experience, while you are still in full control. And neither the admin nor the user has to think about it. As long as the users uses Edge they benefit and if the user switches browsers they are still secure, behind the reverse proxy.
Enable Edge for Business integration
Enabling the new experience is as easy as the switch of a button. Head over to security.microsot.com → System Settings → Cloud apps → Edge for Business integration and enable the feature.
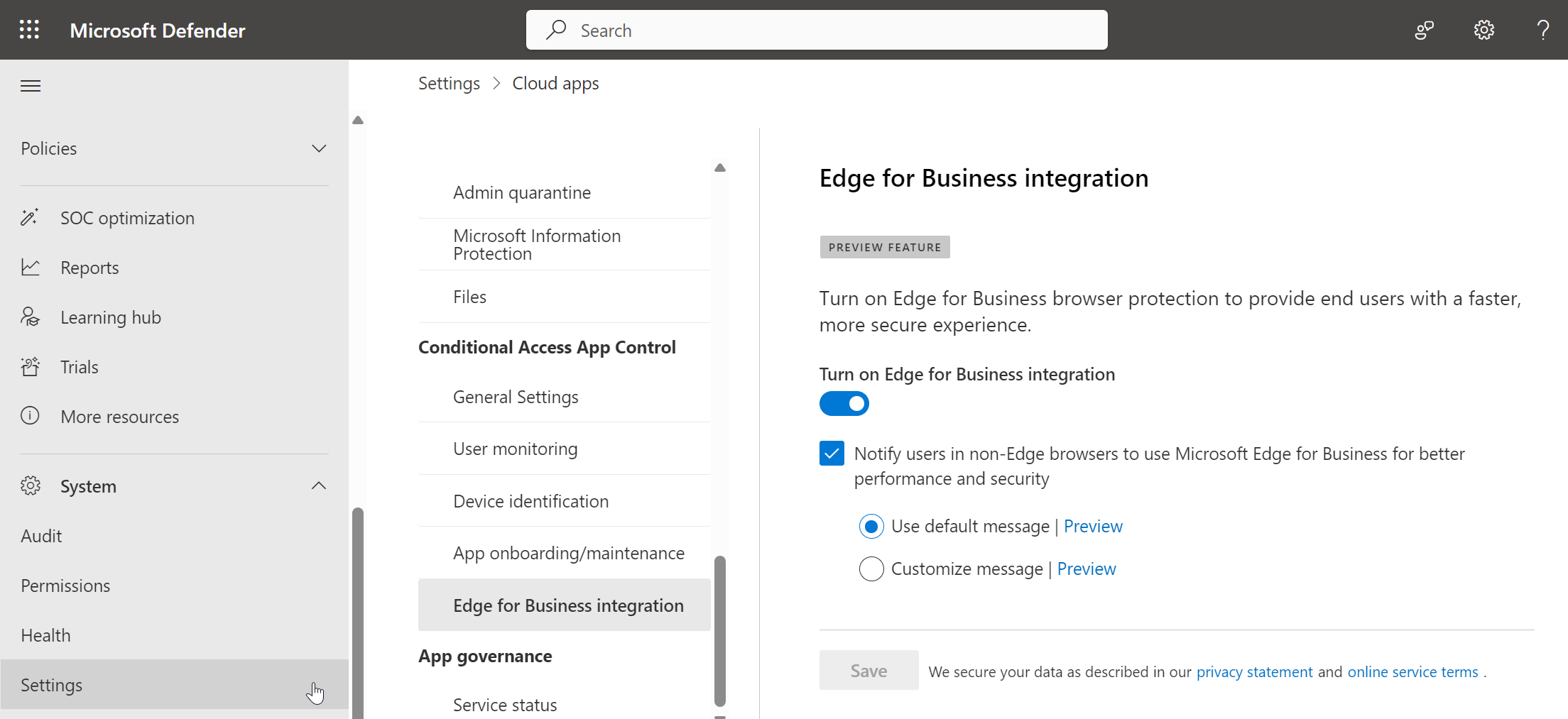
By default the user will receive a customizable message if the don’t access the published app through Microsoft Edge, acting like a nudge. Since you are able to change the message text this could be a more appropriate text for your users.
Supported controls
In public preview the following block methods are supported.
- Block\Monitor of file download (all files\sensitive files)
- Block\Monitor file upload
- Block\Monitor copy\cut
- Block\Monitor print
Setup sessions controls and conditional access
Let’s explore a sample use case to show the capabilities of this feature in action:
First you need to create a session policy. For this head over to the Cloud apps policy management and switch to the “Conditional access” tab.
Create a new session policy and select of the templates. In this case I will use the “Block cut/copy and paste based on real-time content inspection” template.
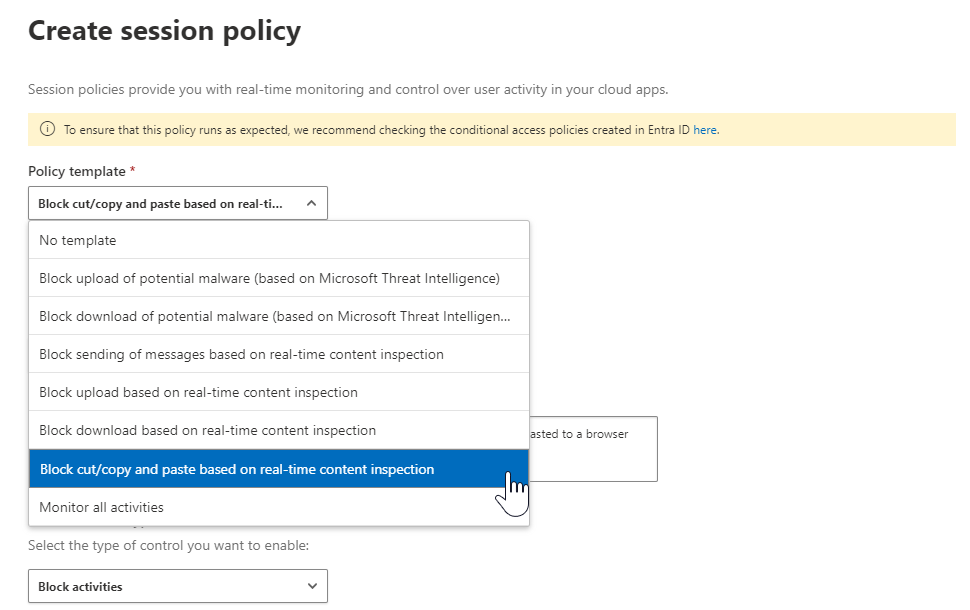
I modified the template to only prevent print, cut and copy for all Microsoft Online Services. This category includes the Azure portal, so be careful. Also I used the default to exclude hybrid joined or Intune compliant devices.

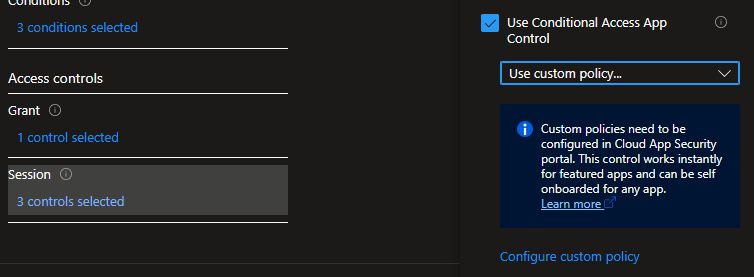
Then I headed over to the Conditional Access policies and created a policy targeting my test user, for all cloud apps, but only when using a browser from a non mobile device. As a precaution I also excluded hybrid joined and compliant devices using device filter.
But the most important setting is in the session controls. Enable “Use Conditional Access App Control” and set it to “Use custom policy…”
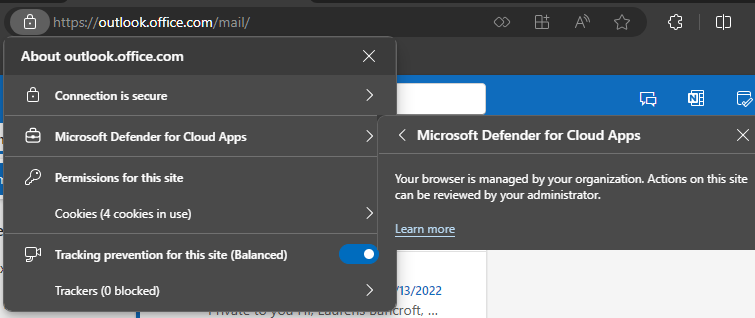
Next use the Microsoft Edge browser an sign-in to e.g. Outlook using the defined test user from a non-corporate device. You should be able to access the website but, depending on your configuration, you might first have to register your work profile. After this you have access to work data without going through the reverse proxy solution.
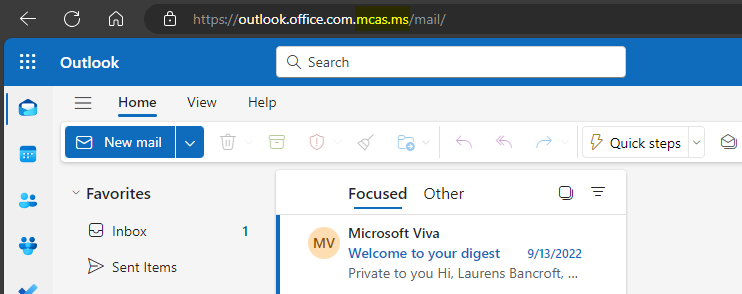
As you can see the URL is not rewritten to mcas[.]ms and in the advanced website information the Microsoft Defender for Cloud Apps indicator is shown. If you click on it you will see that this session is managed and also that actions are logged and can be reviewed.
And if you want to enable the developer tools, you can’t anymore. They are disabled and greyed out.
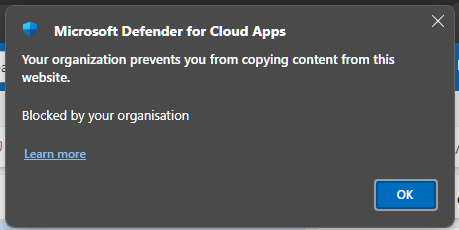
When you attempt to perform an action that is blocked, the browser will warn you about this and prevent the action from happening.
If you would use a different browser the session policy is not not working, but it will fallback to the reverse proxy experience as you see in this screenshot.
Troubleshooting
If a user is not getting the new integrated experience, this might be because there are other policies that are incompatible with the current feature scope. Based on the docs this could be anything from the following use cases.
- Google Chrome users
- Microsoft Edge users who are scoped to a block paste policy
- Microsoft Edge users on Android devices
- Users in apps that use the OKTA authentication method
- Microsoft Edge users in InPrivate mode
- Microsoft Edge users with older browser versions
- B2B guest users
To check which policies were applied check out the activity logs and select the policy that you expect to be applied. Search for the user and check of there are any other policies applied that might contain a method not supported. Depending on your needs adjust the policy or wait until further use cases get added to this experience.
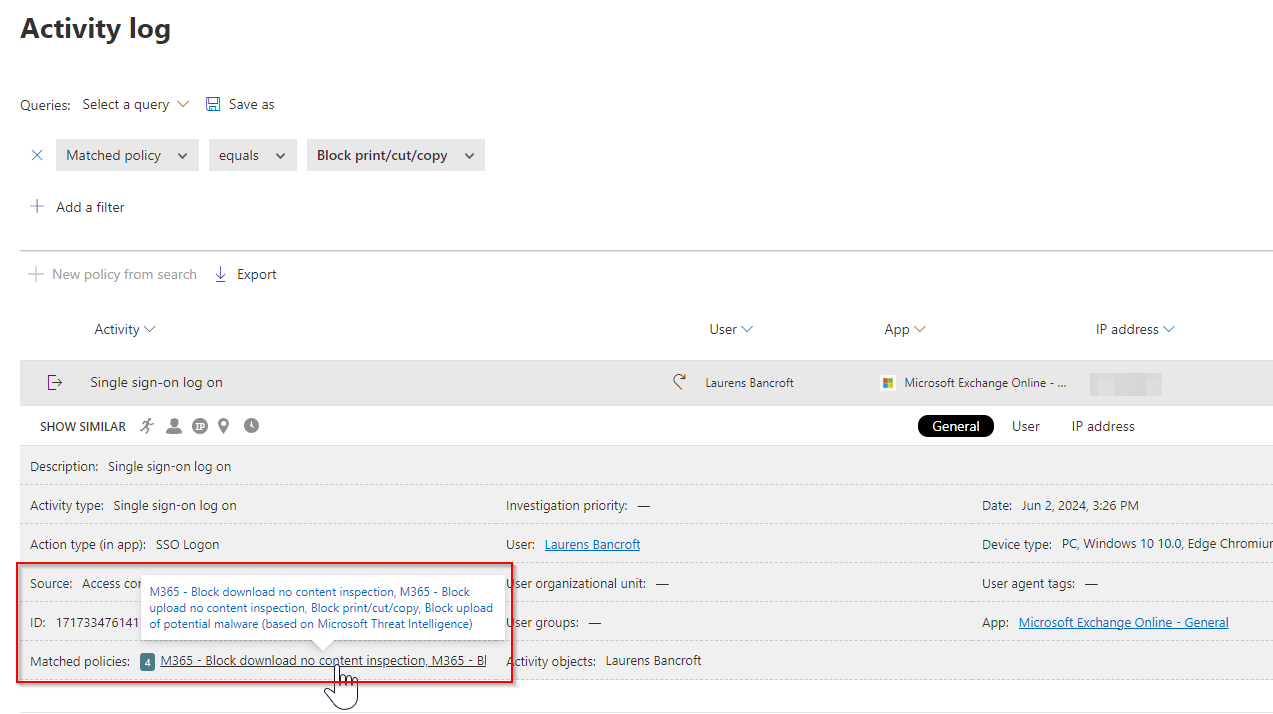
Logging and hunting
While you can navigate using the Activity logs in the web UI and see actions that were blocked, or if the user was redirected, you can do yourself a favor and use Advanced Hunting. While this blog post goes not into the depth of the log source itself, I added a few interesting hunting queries to get you started.
Copy to clipboard events
CloudAppEvents
| where ActivityType == @"Clipboard"
| where ActionType == @"Cut/Copy item"
Disable of Cloud App Session Policy
CloudAppEvents
| where ActionType == @"Set-ConditionalAccessPolicy"
| where ActivityObjects has "Disabled"
| extend ActivityObjects = todynamic(ActivityObjects)
| mv-apply PolicyDetails = ActivityObjects to typeof(dynamic) on ( where ActivityObjects has "PolicyDetails")
| where PolicyDetails.Name == 'PolicyDetails'
| extend PolicyDetails = todynamic(PolicyDetails).Value
Conclusion
In-browser protection with Microsoft Edge for Business is a great addition to the toolbelt of any Defender and helps with data loss prevention. I hope this feature get’s more attention from customers and that Microsoft is extending the supported use cases. E.g. support for B2B users and additional actions like paste would be a welcome addition in the future. Also the ability to block access if it’s not coming from a browser supporting in-browser protection would be something that could help in certain edge scenarios.