Defender for Identity, Npcap on Windows Server 2022
Microsoft Defender for Identity is a very useful tool for gaining deep insight into an Active Directory environment. The agents installed on each domain controller collect information directly from the server’s network traffic and forward it to Microsoft Defender.
For this analysis, the agent uses the WinPcap driver by default. This leads to the following error message on a Windows Server 2022 even under moderate load:
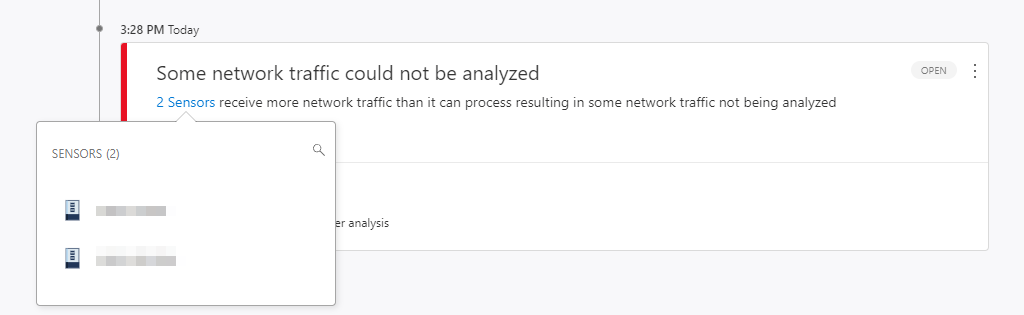
However, the CPU, RAM and network load of the affected domain controller is not particularly high.
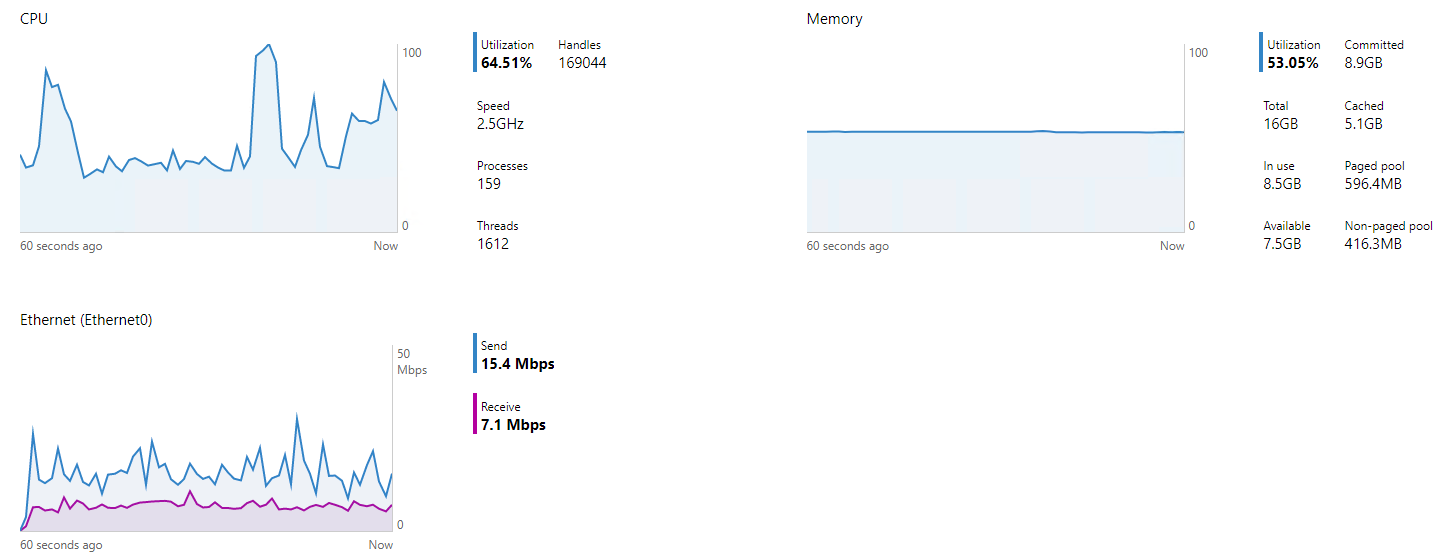
The cause here is the outdated WinPcap driver. It has not been updated since 2013 and official development has been discontinued. The last officially supported operating system version was Windows Server 2012.
With Agent version 2.156, Microsoft now offers the Npcap driver as a replacement for WinPcap.
This driver is under active development and based on a libpcap version from 2021 and not 2008.
For this purpose, Microsoft has signed a license agreement that allows the use of the OEM version and thus the limit of 5 installations does not apply. Another advantage of the OEM version is that it can be silently installed via script.
Using Npcap with Defender for Identity
For Defender for Identity to use the new driver, it must be installed before installing the agent. Otherwise the agent will install the old WinPcap driver automatically.
Download
The first step is to download the new agent package.
The new Azure ATP Sensor Setup.zip file contains two seperate setup files. Azure ATP Sensor Setup.exe and Npcap-1.00-oem.exe.

Uninstall
If the agent is already installed, the new version including the new driver can be installed without restarting the server. However, the current agent must be uninstalled first.
# Remove Current sensor version
$RemoveATPSensor = Get-ChildItem "HKLM:\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\" | Get-ItemProperty | Where-Object { $_.DisplayName -eq "Azure Advanced Threat Protection Sensor" } | Select-Object -ExpandProperty BundleCachePath
Start-Process -Wait -NoNewWindow -FilePath $RemoveATPSensor -ArgumentList "/uninstall /quiet"
It is important that the agent and WinPcap are removed after the uninstallation. If WinPcap is still installed, it must be uninstalled manually.
Installation
During the installation, the Npcap driver must be installed first. We enable the WinPcap compatible mode and disable loopback support.
After that, Defender for Identity Agent can be installed as usual.
# Install Npcap with WinPcap Mode activated and loopback support disabled
Start-Process -Wait -NoNewWindow -FilePath ".\Npcap\npcap-1.00-oem.exe" -ArgumentList "/S /winpcap_mode=yes /loopback_support=no"
# Install Microsoft Defender for Identity Agent
Start-Process -Wait -NoNewWindow -FilePath ".\Azure ATP Sensor Setup.exe" -ArgumentList '/quiet NetFrameworkCommandLineArguments="/q" AccessKey="YOURACCESSKEYHERE" ProxyUrl="http://PROXYURL"'
After switching to the Npcap driver, the error message shown above no longer occurred. The performance improvements promised by Microsoft are therefore really present.