The case of the... Intune SCEP Profil hangs in pending state
In this category I publish blog post explaining a problem and the solution but more important the analysis that lead to the root cause.
The name is a homage to “The Case of the Unexplained” from Mark Russinovich.
The error
These two sentences in the Intune documentation are very important when you want to deploy a SCEP profile.
If you do not follow them exactly, the following phenomenon will occur.
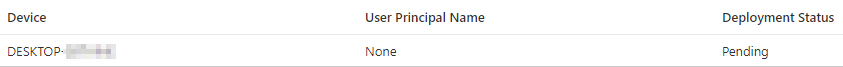
The SCEP profile in Intune is not applied to the device, even after a long wait and successful synchronization of the client.
My pull request was not merged, but Lu Chen incorporated the provieded supportmatrix in the offical troubleshooting guide.
The analysis
Windows 10 client
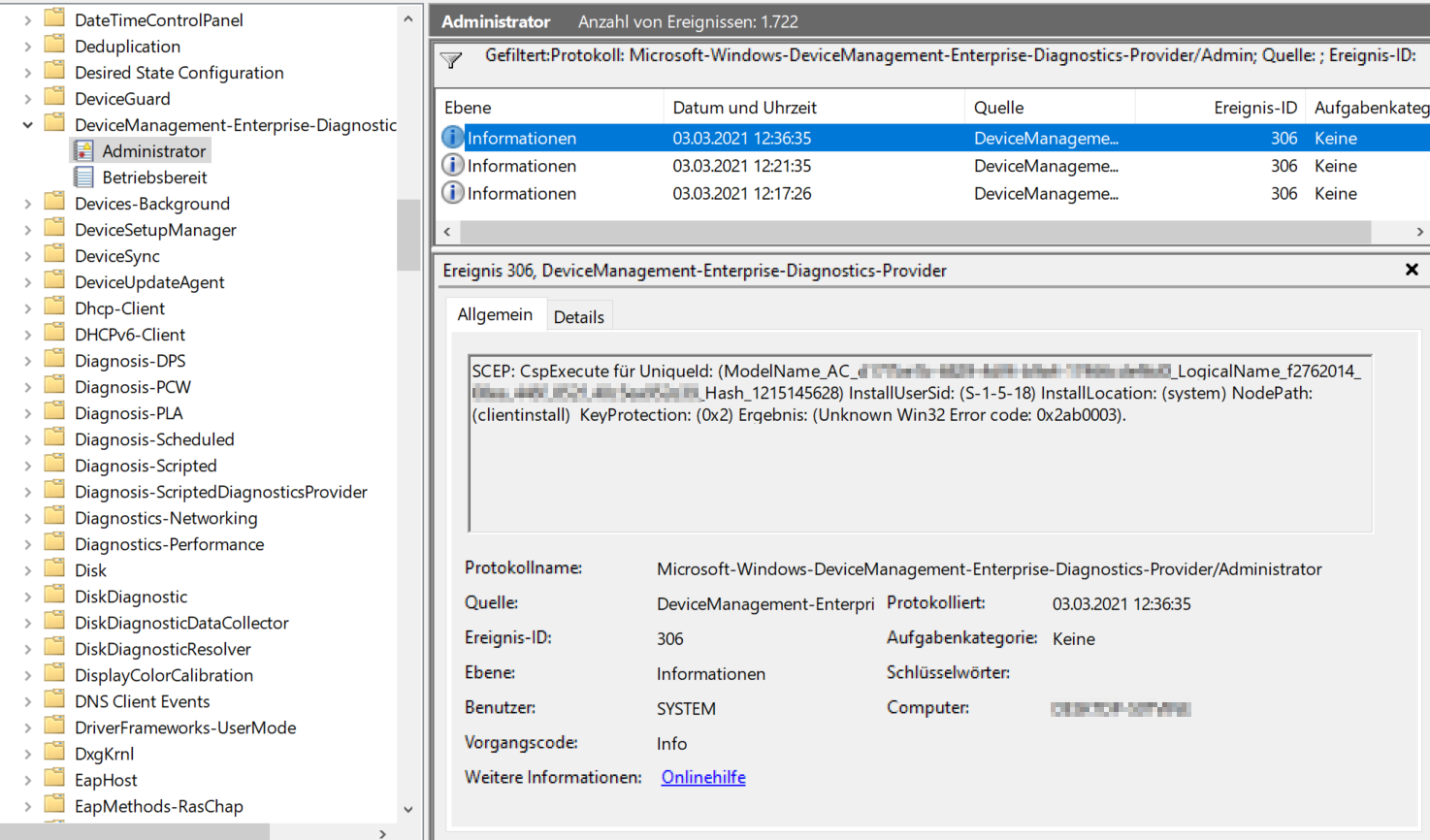
On the Windows 10 device, event ID 306 was not logged in the event log.
Get-WinEvent -ProviderName "Microsoft-Windows-DeviceManagement-Enterprise-Diagnostics-Provider" | ? Id -eq 306
If this is not the case, it can be assumed that the policy has not reached the device.
This can be checked in more detail in the Intune log file MDMDiagHtmlReport.html.
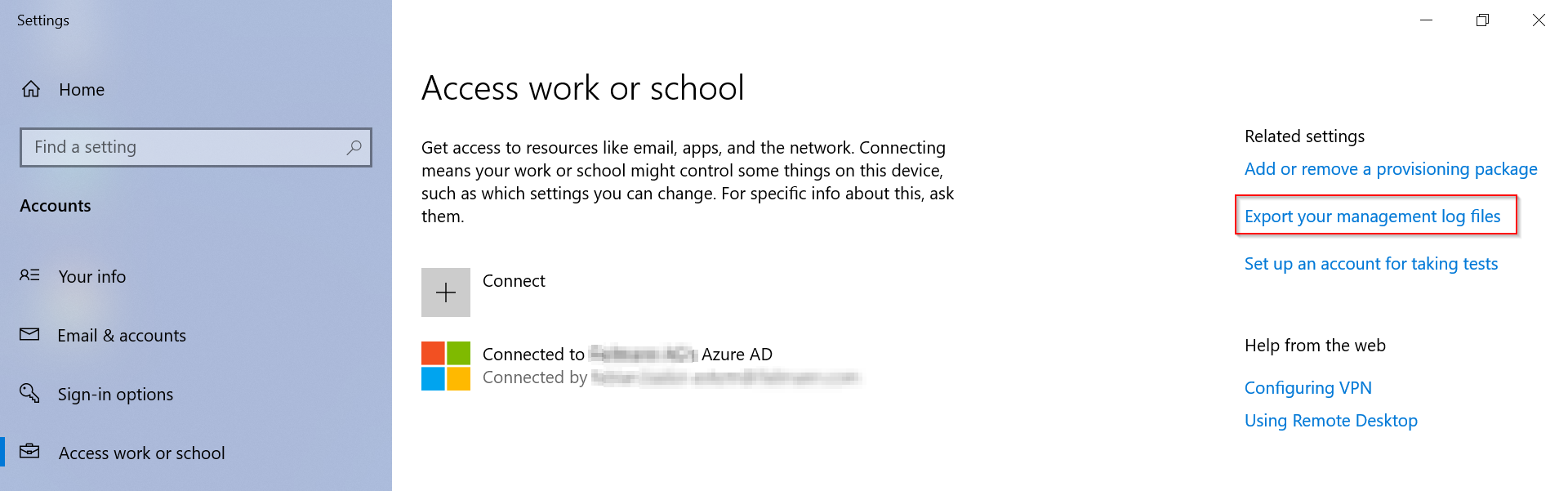
This log file can be created, along with other log information, in the Windows 10 settings.
“Settings” -> “Accounts” -> “Access work or school account” and click “Exports your management log files.” in the right pane. Confirm the following dialog with “Export”.
Translated with www.DeepL.com/Translator (free version)
Afterwards the file MDMDiagReport.cab is located in the folder C:\Users\Public\Documents\MDMDiagnostics and MDMDiagHtmlReport.html must be extracted from it. In the log file a search for the configuration service provider name ClientCertificateInstall is sufficient. If this cannot be found, the SCEP profile was not distributed.
IIS server
The second place to look would be the server running the NDES role. The next step would be to check whether incoming connections for the SCEP service are logged in the IIS log under C:\inetpub\logs\LogFiles\W3SVC1. These can be identified by the fact that the URI /certsrv/mscep/mscep.dll is requested.
Almost certainly, the corresponding client will not log here. However, it is good point for further analysis if the first hurdle has been cleared but problems still occur.
The root cause
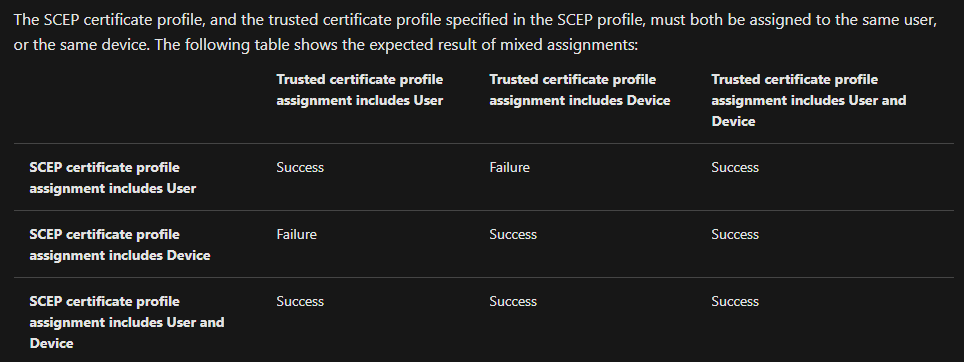
The cause of the behavior was, in this case, the incorrect distribution of the Trusted Certificate Profile via Intune.
The SCEP profile was assigned to a device group, but the Trusted Certificate Profile was assigned to a user group. The result of this constellation is that nothing happens.
It is not enough that the user who uses the device trusts the CA, but in order to distribute the SCEP profile, the device must also receive this profile.
Supportmatrix
| Trusted certificate profiles assigned | to user | to device | both |
|---|---|---|---|
| SCEP Profile assigned to user | Yes | No | Yes |
| SCEP Profile assigned to device | No | Yes | No |
The solution
All you have to do is assign the appropriate Trusted Certificate profile to the user or device group and the next time the client is synchronized, the SCEP certificate will be applied correctly.
MDMDiagHtmlReport.html
Eventlog