TIL BitLocker + YubiKey = ❤️
TIL is a blog series in which I document (for me) interesting insights.
This knowledge is possibly already documented a hundred times on the Internet. But so i can find it again i wrote it down here.
BitLocker provides a convenient way to encrypt the hard drive on computers running Windows 10 Professional.
A YubiKey is my choice for passwordless sign-in to Entra ID (Azure AD).
The two together make my computer even more secure.
Technical background
Under normal circumstances, a computer encrypted with BitLocker is safe until an attacker gains access to the data with a cold boot attack.
In the default configuration, BitLocker reads the key stored in the TPM without user interaction and decrypts the data. As soon as the device is turned on, the data is no longer safe from technically skilled attackers.
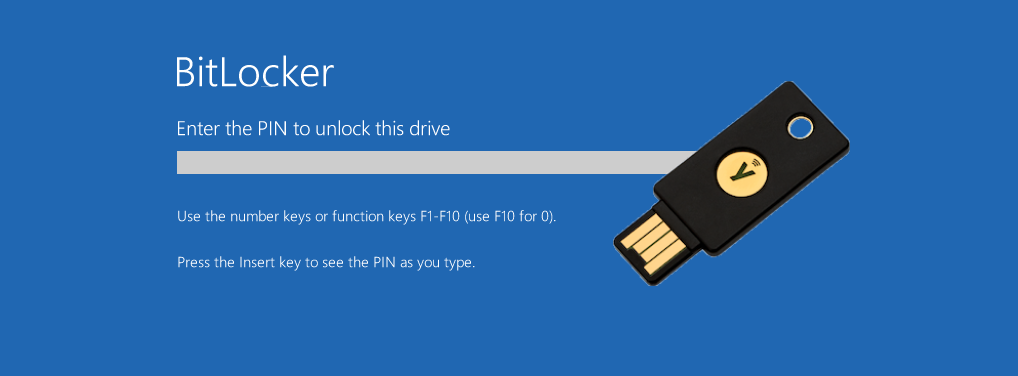
Therefore, BitLocker offers the option to require a second factor, a PIN, a USB stick, or both in combination, to unlock the data from the TPM.
However, since I don’t want to carry around another security key in the form of a USB stick, I can simply use the YubiKey.
YubiKey ≠ FIDO2
Even if I use the YubiKey in most cases for FIDO2 logins, this is not the only standard the key supports. For example, it is also possible to store a static password or a PIN. Depending on the configuration, this number sequence is transmitted via the virtual USB keyboard after holding down the key for a longer period of time.
This makes the YubiKey the perfect place to store my BitLocker PIN. And in addition, I can also store the PIN in my password safe and enter it manually in the event of an emergency.
TPM + PIN is not the same as simply a BitLocker password. The password is far from the same security standard because the data can be copied and decrypted in another hardware via brute force.
With TPM + PIN, the error message “Too many PIN entry attempts” is displayed after too many incorrect entries and decryption is only possible with the BitLocker Recovery Key or after the Unlock Period has expired.
If the hard disk is copied and inserted into another hardware, the TPM data is missing and decryption is only possible with the BitLocker Recovery Key.
This blogpost by Oleg Afonin explains the different variants and attack scenarios in detail.
Configure YubiKey
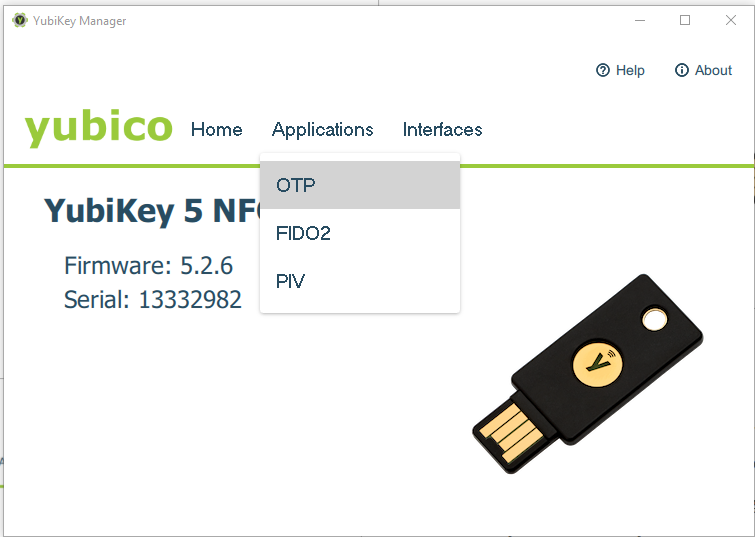
To enable the additional functions on the YubiKey, the YubiKey Manager must be installed. The software is available on Windows, Linux and MacOS.
In the app, select “Applications” -> “OTP”.
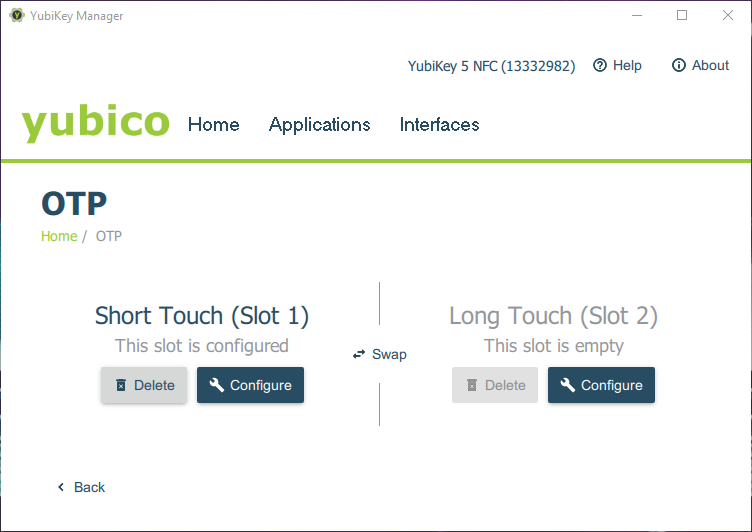
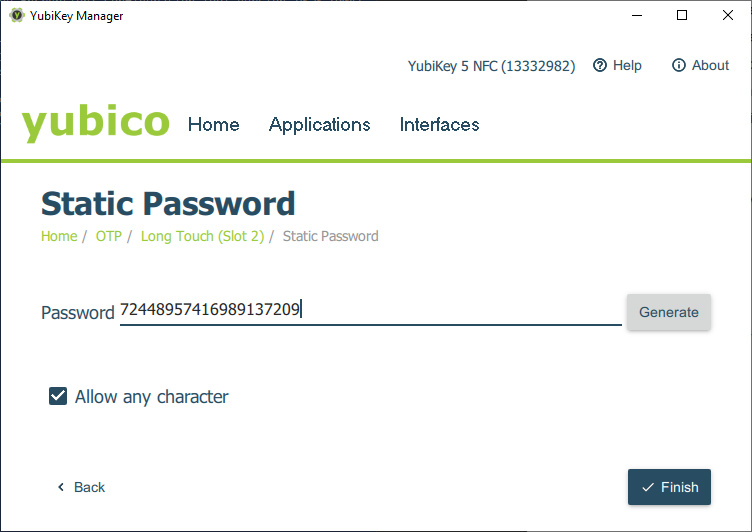
Slot 2 (Long Touch) should not be in use. Select “Configure” and choose “Static password” in the next dialog.
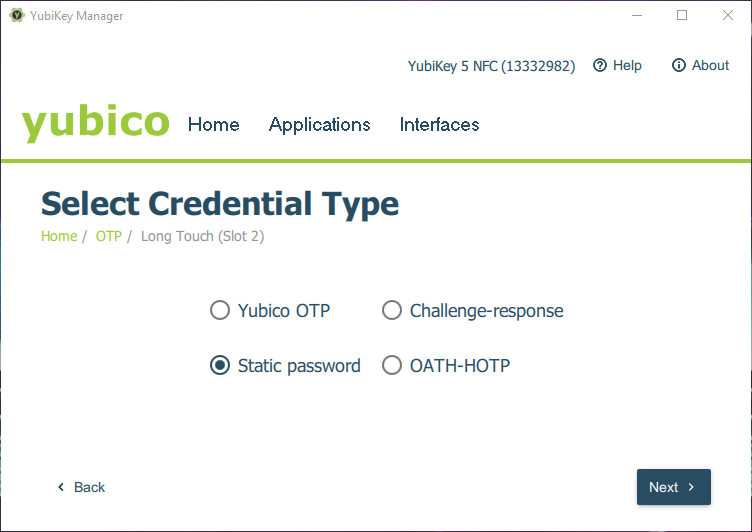
To be able to use digits the option “Allow any character” must be activated.
PIN verification
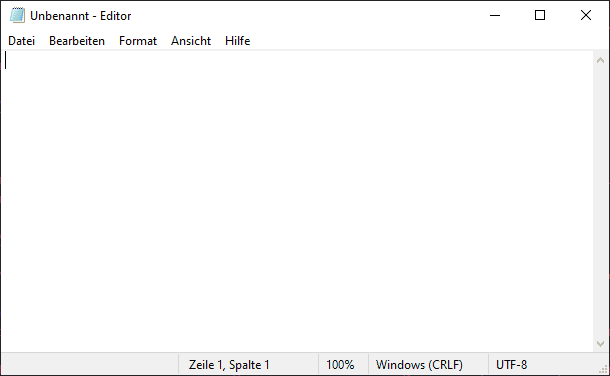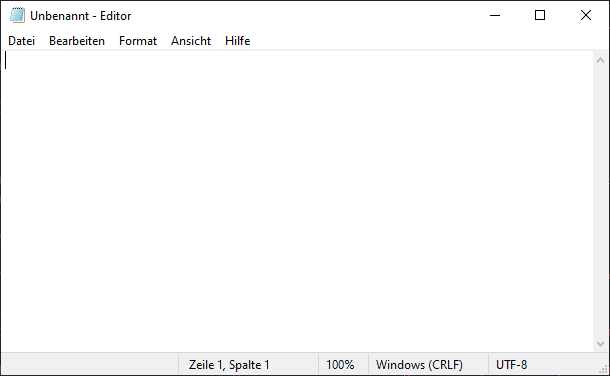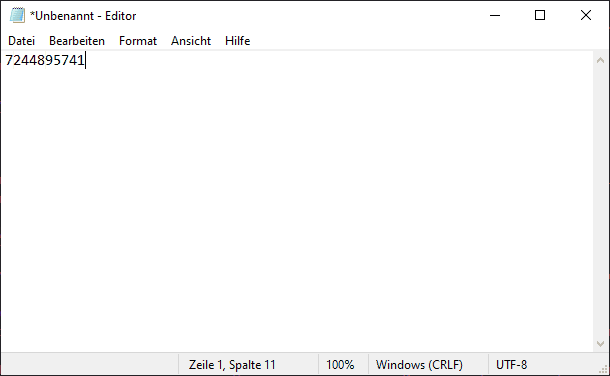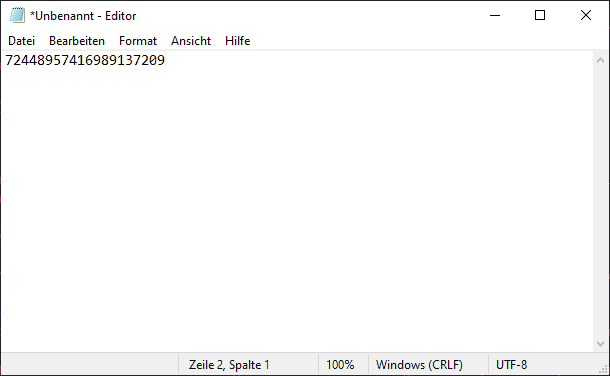
To ensure that the stored value corresponds to the expected value, it is sufficient to open a text editor and hold down the YubiKey for a longer time. After about 3 seconds, the PIN is typed in and confirmed with a return.
Configure BitLocker
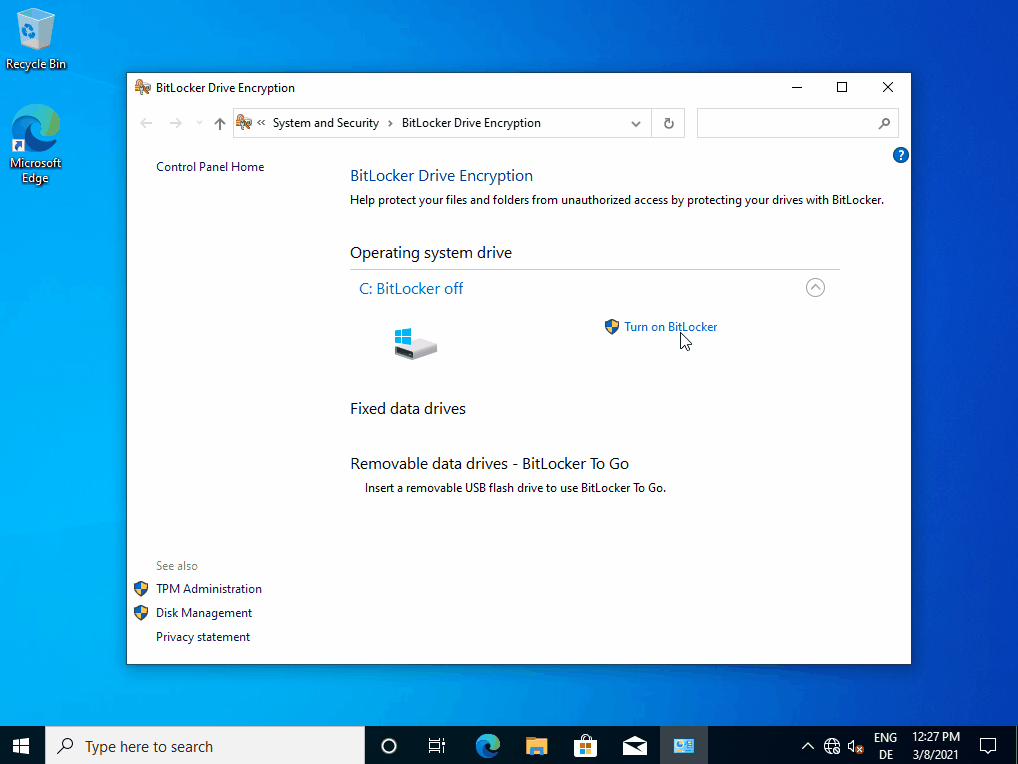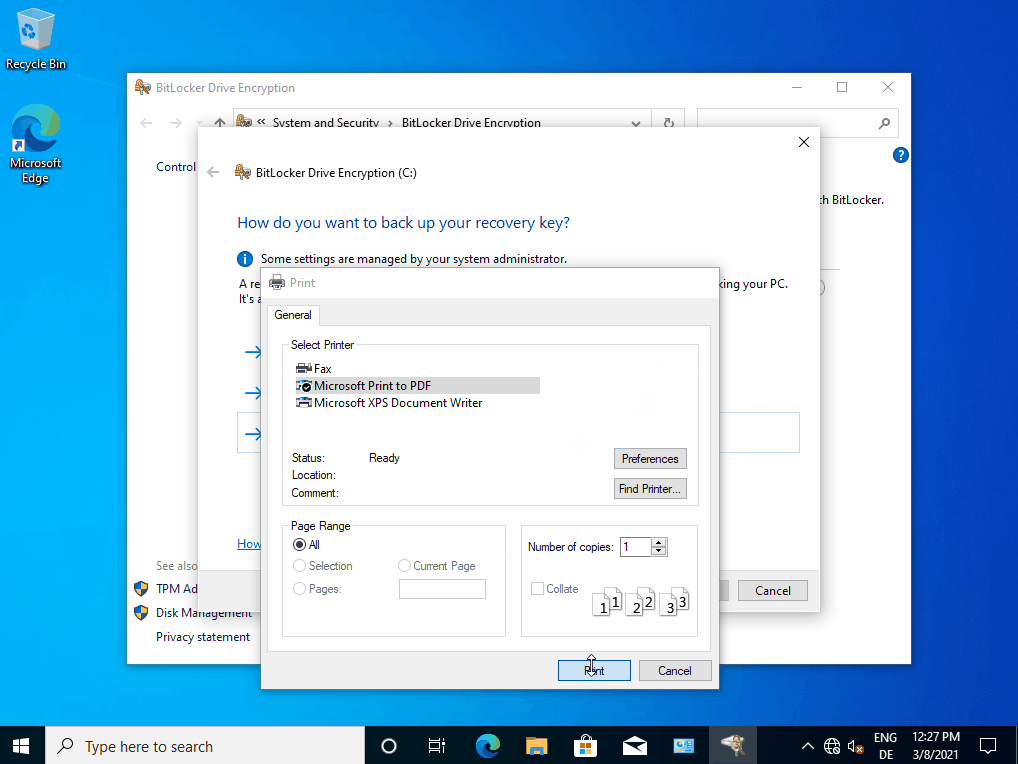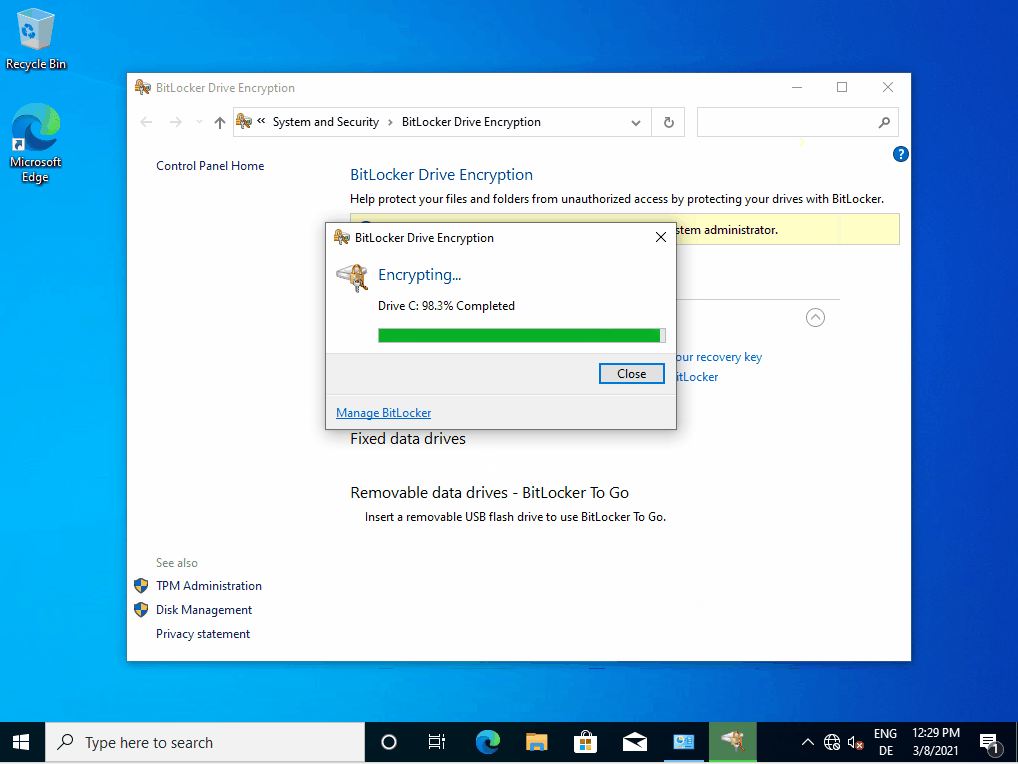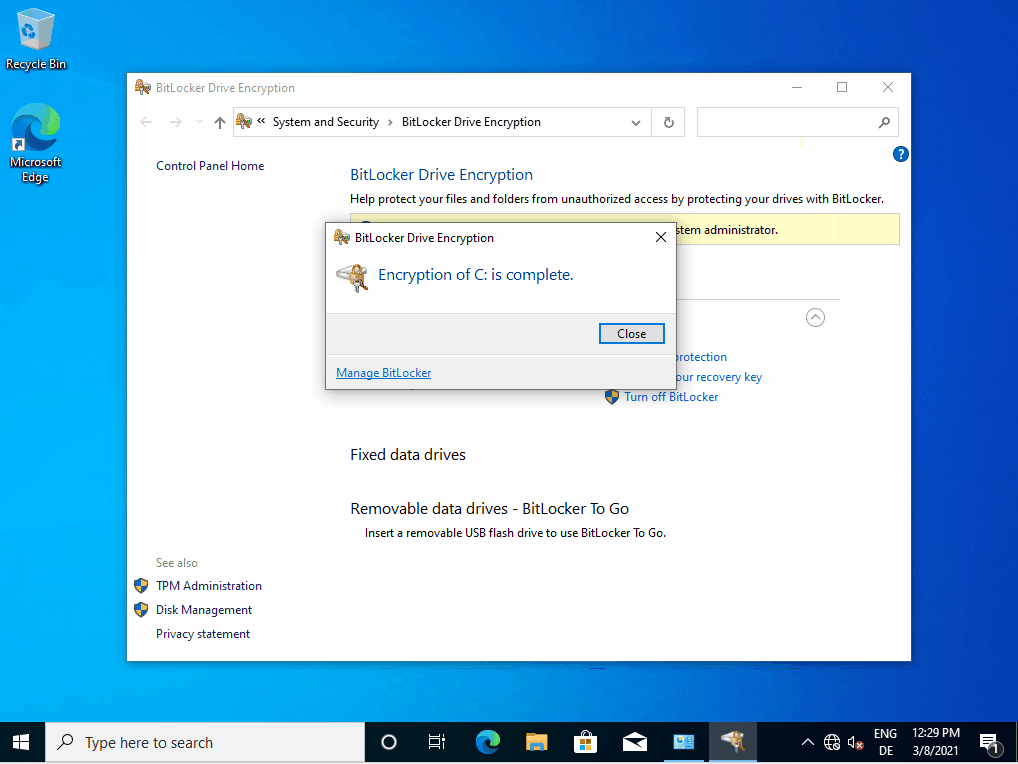
If BitLocker is not yet activated, start the BitLocker administration and turn on BitLocker with “Turn on BitLocker”.
The recovery key should be saved on a secure unencrypted medium or printed out.
Now all that remains is to set up the PIN.
To do this, the first step is to modify the local group policy.
In Computer Configuration \ Administrative Templates \ Windows Components \ BitLocker Drive Encryption \ Operating System Drives enable the policy “Require additional authentication at startup”.
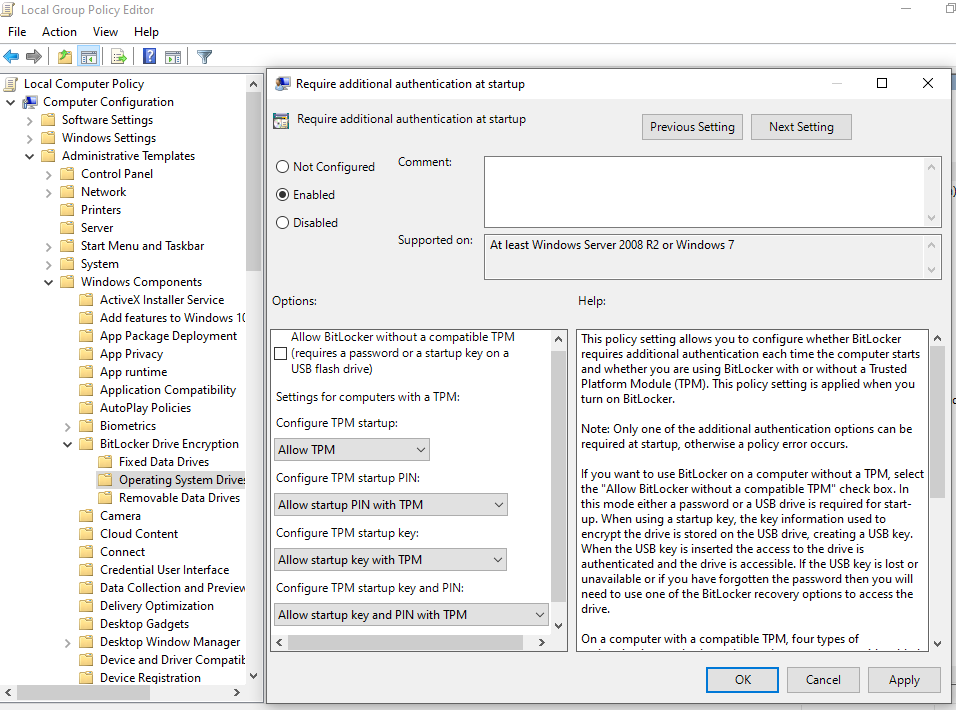
The checkbox “Allow BitLocker without a compatible TPM” should not be selected if the computer has a TPM chip available.
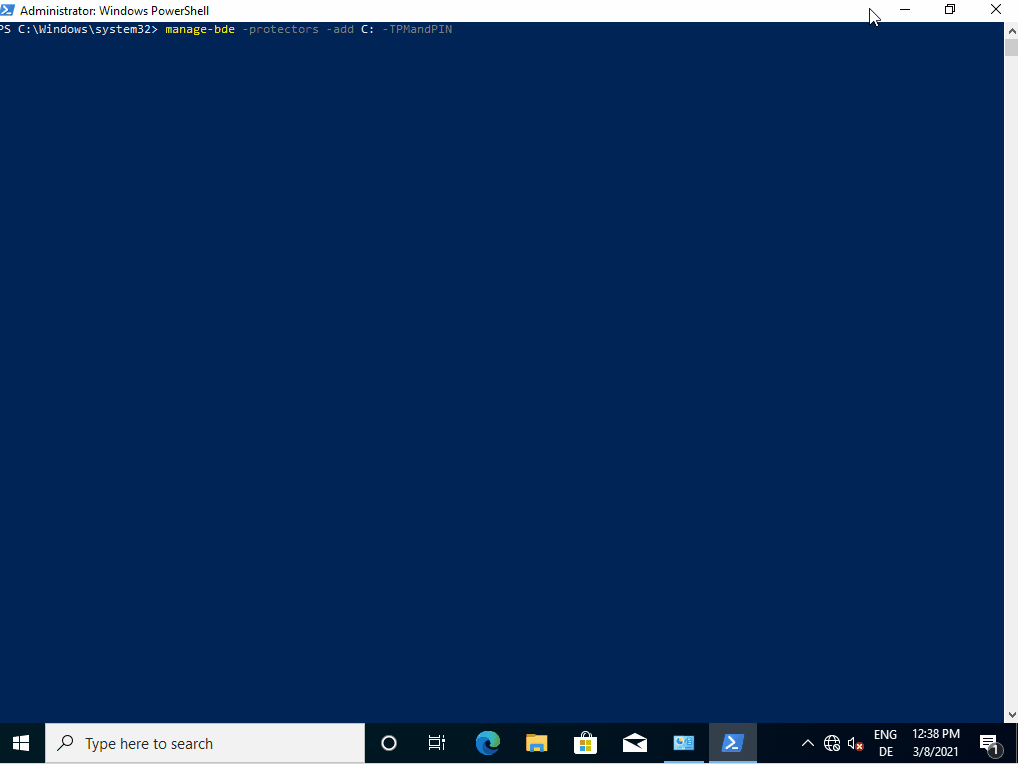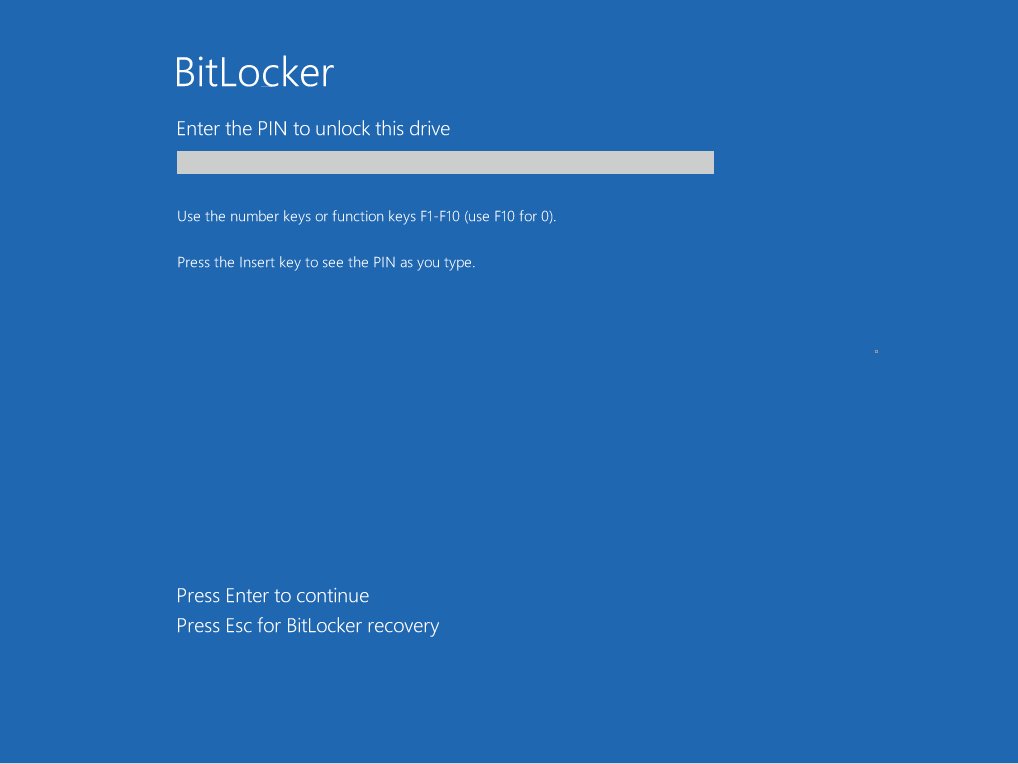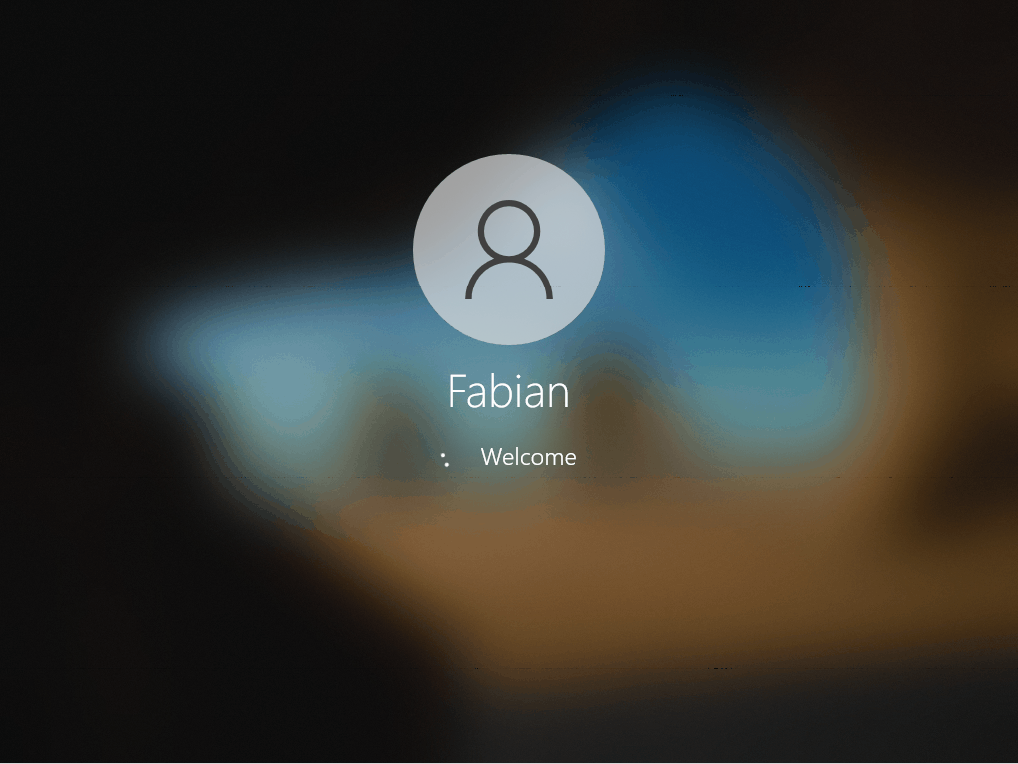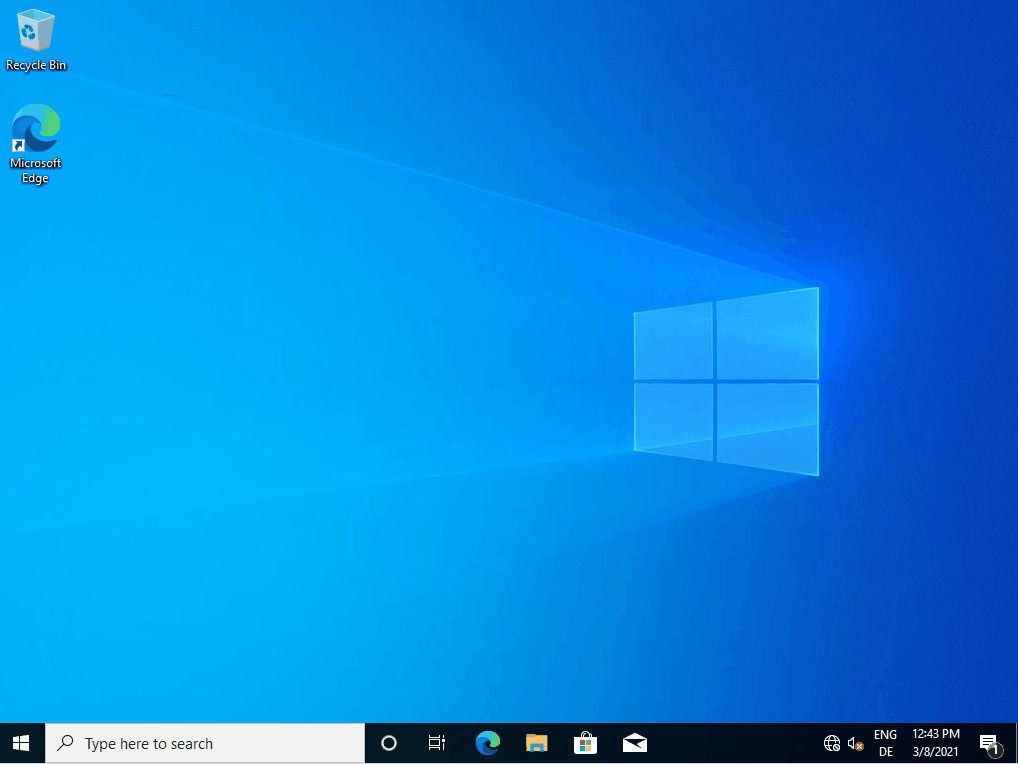
Now the PIN protection can be activated with the command manage-bde.
manage-bde -protectors -add C: -TPMandPIN
The YubiKey can be used directly to enter the PIN. Simply press and hold until the next prompt appears and then press and hold again.
The computer must then be restarted.
After the reboot, the BitLocker PIN is now requested. Thanks to the YubiKey, even entering a 20-digit PIN is only a matter of seconds.

Optimization for increased safety
Since the output of the PIN is not protected any further, one factor is still sufficient for successful decryption: the YubiKey.
However, the security can easily be increased. For example, you can enter the first four digits of the PIN manually and the remaining 16 through the YubiKey. When setting up the PIN, you only have to make sure that the manual part of the PIN is before the part stored in the YubiKey. This is due to the fact that the YubiKey always ends the entry with a return and thus completes the PIN entry.