Phase out Legacy Authentication - Endgame
Blog series
This is the last part of the series on “Phase out Legacy Authentication”.
- Preface
- Enable Modern Authentication
- Create prerequisites
- Gain insights
- The first 90%
- The next 9%
- Endgame
A lot of work lies behind you when you arrive here. Starting with the necessary preliminary work, the required changes, through reporting and maintaining exception lists.
But the biggest hurdle for the next step was definitely the last 9%. Finding and removing every exception is time-consuming and tedious. Depending on the environment, this last step can take anywhere from a few days to half a year.
Now it is time to close the last loopholes and remove resources that are no longer needed after one final check.
Final check
Exception group
The group “CAPolicy-Exclude-Block-Legacy-Authentication” should no longer have any members. Only those who were in this group could still bypass the block after the last article.

Workbook
In the Entra ID (Azure AD) Workbook “Sign-ins using Legacy Auth” no successful logins must be logged.
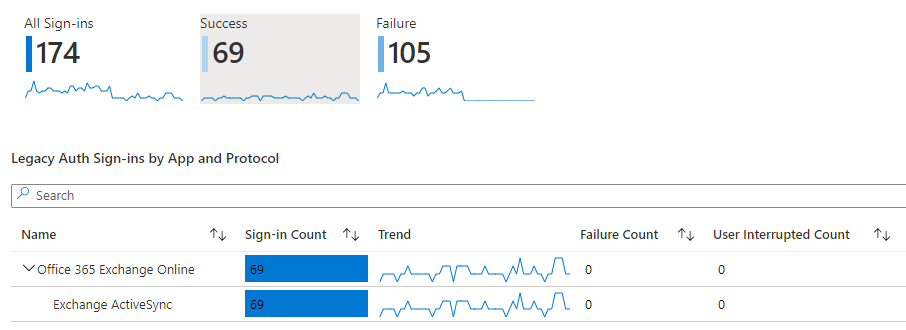
The observant reader may now ask why I write “No successful Sign-ins”, although the workbook clearly shows 69 successful Sign-ins.
Here again the Exchange ActiveSync phenomenon applies. All successful sign-ins have taken place with this protocol and if all steps have been completed properly, all users appearing here will have only one email in their inbox. And this email has the subject “Your email access has been blocked”.
What exactly happens here is explained in more detail in part four in the chapter Role Play.
The user will probably not have manually removed the ActiveSync account after switching to Outlook for iOS or Android. If this bothers you, you have to contact these users. However, no one can sign-in with this protocol anymore.
And a picture like this, but probably the fewest will see.
If you have made friends with Kusto in the meantime, you can also use this customized query.
|
|
SharePoint Online and B2B guest user
To completely disable Legacy Authentication for B2B guest users, the protocol must be disabled in SharePoint.
# Install SharePoint PowerShell module
Install-Module -Name Microsoft.Online.SharePoint.PowerShell -Scope CurrentUser
# Connect to your tenant
Connect-SPOService -Url https://YOURTENANT-admin.sharepoint.com
# Disable legacy authentication
Set-SPOTenant -LegacyAuthProtocolsEnabled $false

Exchange Online
Update 08.03.2022
On Twitter David Caddick hit me up with a suggestion and on the same day Nate Hut released a nice blog post on why to disable legacy authentication even if you blocked it using conditional access policies.
For Exchange Online this is quite easy.
# Install Exchange Online Module
Install-Module -Name ExchangeOnlineManagement -Scope CurrentUser
# Connect to your tenant
Connect-ExchangeOnline
# Create a authentication policy, defaults to blocking all legacy protocols
New-AuthenticationPolicy -Name "Block Legacy Auth"
# Activate the authentication policy for the Exchange organization
Set-OrganizationConfig -DefaultAuthenticationPolicy "Block Legacy Auth"
The biggest upside to this method is, that you won’t see any failed logins in the Sign-In Logs anymore.
Clients that support OAuth as an alternative, like the iOS Mail App will automatically switch to this method. So you still might see some errors in the logs, as long as the user does not perform multi-factor authentication.
Conditional Access Policies
Common Policy: Block legacy authentication
It is time to stop allowing exceptions and enable the policy that has been running in report-only mode.
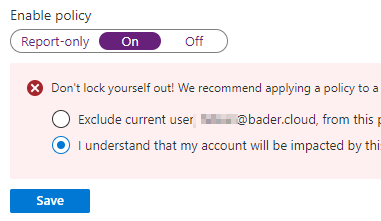
Again, it is important when saving not to exclude your own user from the policy.
Delete temporary policies
Depending on which way you chose to deactivate Exchange ActiveSync, there are now one or two policies that are no longer needed.
- Temporary Policy: Block legacy authentication Rollout
- Temporary Policy: Block ActiveSync clients
Both can be deleted after activating the global “Block legacy authentication” policy. The first policy reliably ensures that only Modern Authentication can be used.
Delete groups
If necessary, the two exception groups are no longer needed and can be deleted.
- CAPolicy-Include-Block-Legacy-Authentication
- CAPolicy-Exclude-Block-Legacy-Authentication
Endgame
You’ve done it. No users in your environment are using legacy authentication anymore.
This is a big win for security and allows you to use many new features like Conditional Access authentication context in the future.
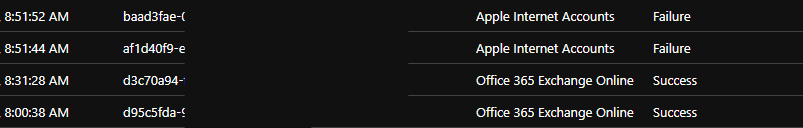
And if a user, like Alice here, tries again, it will be rejected.
Questions, suggestions, corrections?
If you enjoyed this blog series, follow me on Twitter and subscribe to this blog. Or maybe even buy me a beer 🍺.
You have discovered a mistake or have questions? Then write me on Twitter or by e-mail.