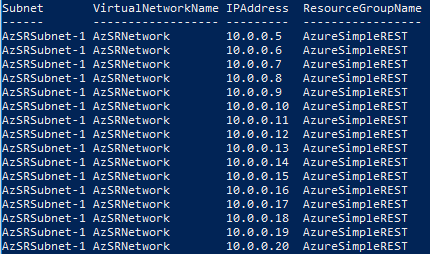
Whether with automated deployment or when creating a load balancer in Azure. Finding a free IP address is unfortunately not an easy task with the existing cmdlets.
Test-AzureRmPrivateIPAddressAvailability
A popular way to archive that is to use the cmdlet Test-AzureRmPrivateIPAddressAvailability. It returns the value TRUE or FALSE when specifying the network and an IP address. Some people now loop through every network address in a subnet until a free IP address is confirmed by TRUE.
Although Microsoft does a great job with their AzureRM Modul module, there are always reasons not to use these cmdlets. In most cases because they are slower than direct requests against the Azure REST API. In other cases because certain functionality has not yet been implemented.
The module AzureSimpleREST written by me positions itself in this gap
The module contains e.g. functions like “Get-AzSRVMProtectionStatus” which uses an officially documented REST Call, but I don’t know any AzureRM cmdlet that provides this function.
Pester tests can be used to ensure a level of quality in PowerShell module development that would otherwise be difficult to achieve manually. There are two important factors to consider. Module and Function Integrity.
Function Integrity I will explore this point in more detail in a later blog entry. In short, the actual function of the module must be ensured.
A popular example is a function that adds up two numbers.
To guarantee high availability of a service on Azure, Availability Sets are a very popular way. But what are the requirements of this configuration for the underlying virtual network?
In most design documents you will find an image that looks similar to the following.
Two virtual machines in an Availability Set on the same subnet of a virtual network.
But what if I want to install the two virtual machines in different subnets or even different virtual networks?
…who annoys the most in the land.
Proxy servers are still a popular tool in many enterprise environments to channel outbound web traffic, scan and prevent threats. Unfortunately, very few companies use transparent proxy solutions and force you to configure the proxy server in the respective application.
Since the configuration of the proxy is different for each application, I collect some examples here.
Windows You can do a lot of things right with a system-wide proxy.
The Azure REST API is well documented and thanks to the REST API browser you can quickly try something out. However, there are moments in the Azure portal that lead to puzzled faces and in these cases the “Developer tools” of your favorite browser help to shed light into the dark.
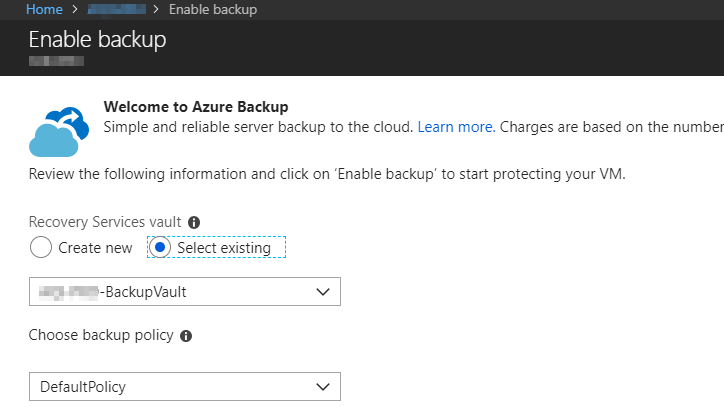
The scenario A user with “Read Only” rights on the subscription should be able to see if and where a virtual machine is backed up.