When you work with one or multiple Microsoft Sentinel workspaces you may find it necessary to not only deploy Analytics rules and other configuration artifacts using a version controlled source control (CI/CD) to limit human error and enforce consistency. But you might also want to independently verify your deployment on a regular basis.
I certainly did and set out to write a test driven solution.
Since I love to use PowerShell and there is already a superb test framework, the tool to use for the task at hand was an easy choice: Pester.
Updated information Microsoft announced in August 2024 that “[…]as part of ongoing security hardening[…]” they will remove “[…]removed unused permissions from the privileged “Directory Synchronization Accounts” role[…]”.
Announcement in the Entra ID What's new section The full announcement reads as follows:
As part of ongoing security hardening, we have removed unused permissions from the privileged “Directory Synchronization Accounts” role. This role is exclusively used by Connect Sync and Cloud Sync to synchronize Active Directory objects with Entra ID.
If you have worked with Microsoft Sentinel you will, at one point, stumbled over two different file formats for Analytics Rules: YAML and ARM.
The YAML format is mostly used to distribute Analytics Rules between people. All Analytics Rules you will find in the official Sentinel GitHub repo and others out there are offered in this format.
The ARM format is what you need to deploy the Analytics Rules when using a pipeline or even if you want to import them using the UI in Microsoft Sentinel.
Business email compromise and phishing are just two of the threats sent to hundreds and thousands of email inboxes around the world every day. As defenders, we use various tools and methods to limit the delivery of these emails to the intended target.
In most cases, the attackers start by registering a domain that closely resembles the target company’s own domain name, or simply include the company name in the domain (e.
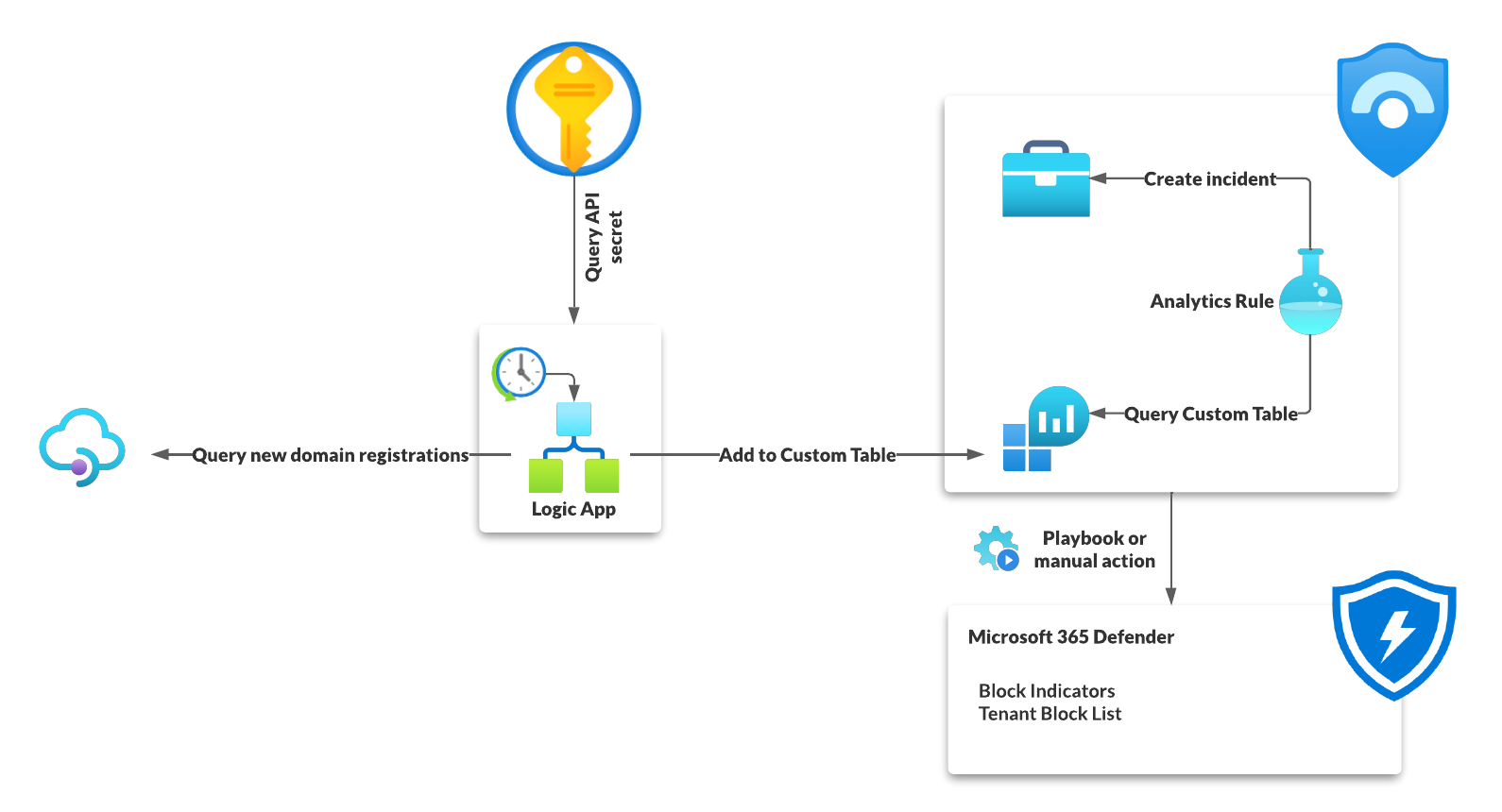
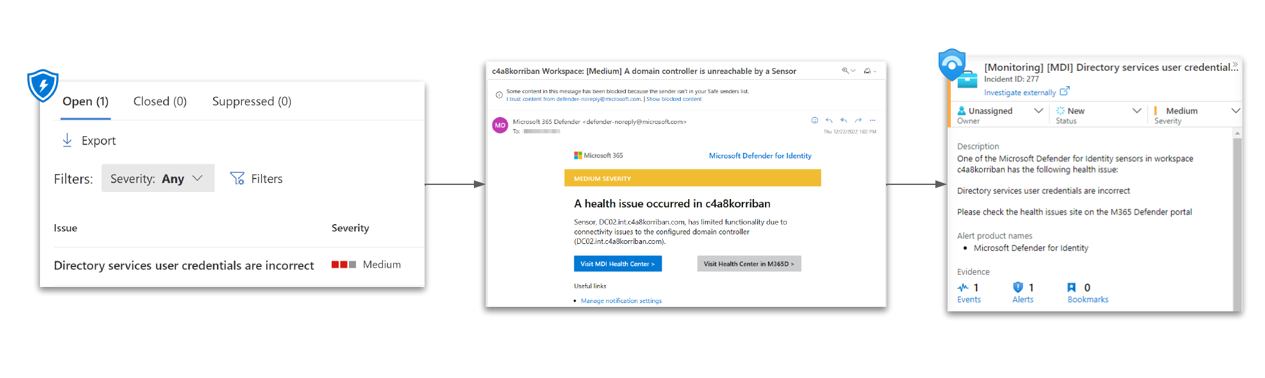
Integrate MDI health alerts in Microsoft Sentinel or how to turn every e-mail notification in a custom alert in Sentinel and customize alert details for your benefit.
Over the weekend I finished a really fun project I had in mind for a couple of weeks.
My newest website: AnalyticsRules.Exchange
In this post I will explain the reason why I created this new website, as well on how I did it. At the moment I will not publish the code, not because I don’t want to share it, but because it’s super ugly and not something I want to be a source for other people to start with.