Phase out Legacy Authentication - Create prerequisites
Blog series
This is part three of the six-part series on “Phase out Legacy Authentication”.
- Preface
- Enable Modern Authentication
- Create prerequisites
- Gain insights
- The first 90%
- The next 9%
- Endgame
Recap
In the first part of the series, Modern Authentication was enabled for all Microsoft 365 services and can now be used.
This part is about creating the prerequisites to gain a detailed insight into the usage of the different authentication methods and to make it possible to disable legacy authentication per user.
Centrally store SignIn logs
Entra ID (Azure AD) credentials are only stored for 7 days (Free) or 30 days (Premium) and can only be evaluated in a cumbersome way.
For a more detailed and flexible analysis, a Log Analytics workspace is therefore necessary. According to experience, the costs are about 0.02 € / user / month if a storage period of 60 days is targeted. The first 5 GB of log data are free of charge. For storage beyond the 31st day, further costs are incurred.
Even if you only keep the data for the first 31 days, the Log Analytics workspace is worth it. This type of data storage allows not only the use of Entra ID (Azure AD) Workbooks but also the detailed analysis of the data using Kusto.
Create a Resource Group and Log Analytics workspace
In the Azure portal, select the appropriate subscription and create a new resource group.
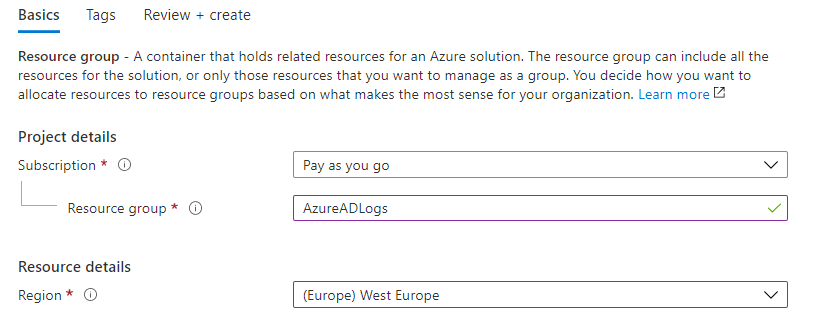
Create a new resource of type “Log Analytics workspace” in the newly created resource group.
The name of the workspace must be unique in the selected region and may only contain letters, numbers and -.
Pay-as-you-go (Per GB 2018) must be selected as the pricing tier.
Azure AD Data Forwarding to Log Analytics workspace
A 30-day trial is available for 25 users.
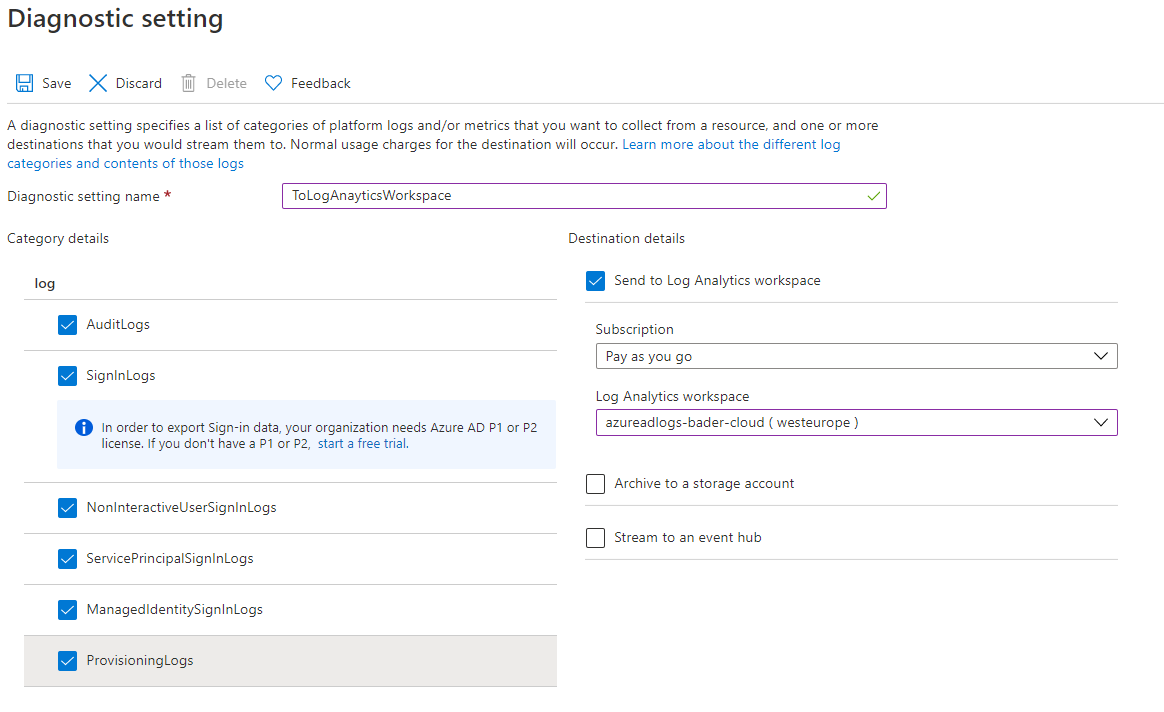
In the Diagnostic Settings of Entra ID (Azure AD), the forwarding of data to the LA workspace can now be set up.
- Add diagnostic setting

- Choose a descriptive name for this configuration
- Select the desired log categories for forwarding.
At a minimum, the following log data must be recorded.SignInLogsNonInteractiveUserSignInLogsServicePrincipalSignInLogsManagedIdentitySignInLogs
- Optional, but recommended, are
AuditLogsandProvisioningLogs. - Select “Send to Log Anaytics workspace” and you Log Analytics workspace as the destination.
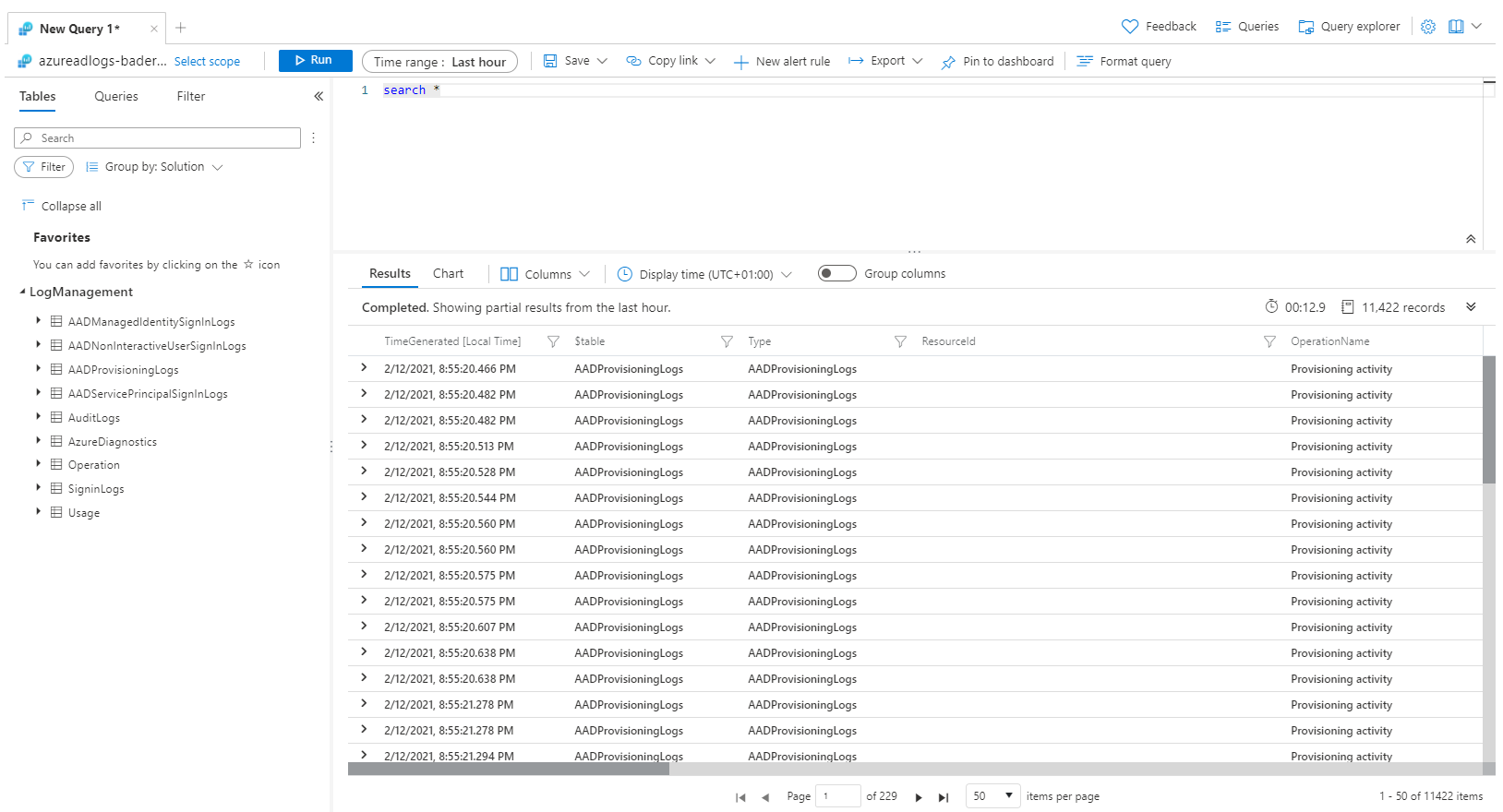
If the connection has been established successfuly, the Log Analytics workspace is now accessible via the Logs option in the Entra ID (Azure AD) portal. It may take some time until the first data arrives. For each selected log, a corresponding “table” is displayed under LogManagement.
Create AAD groups
Two groups must be created to control who can use Legacy Authentication.
| Groupname | Description |
|---|---|
| CAPolicy-Include-Block-Legacy-Authentication | Users in this group are directly affected by the CA Policy to Block legacy authentication |
| CAPolicy-Exclude-Block-Legacy-Authentication | Users in this group are not affected by the CA Policy to Block legacy authentication |
The exact function and use of the groups will be explained later.
Create Conditional Access policies
Two conditional access policies are required for the gradual shutdown.
| Policy Name | State |
|---|---|
| Common Policy: Block legacy authentication | Report Only |
| Temporary Policy: Block legacy authentication Rollout | On |
Common Policy: Block legacy authentication
This policy is based directly on the Microsoft recommendation.
It is operated in “Report Only” mode and is used to evaluate usage until Legacy Authentication is finally disabled.
- Use the Entra ID (Azure AD) portal -> Security -> Conditional Access to create a new policy with the name “Common Policy: Block legacy authentication”
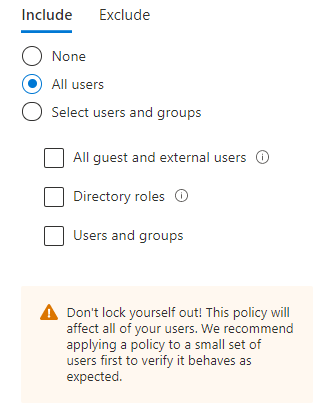
- Select Assignments -> “Users and groups”
- Include: “All users”

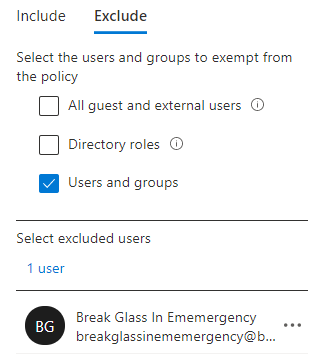
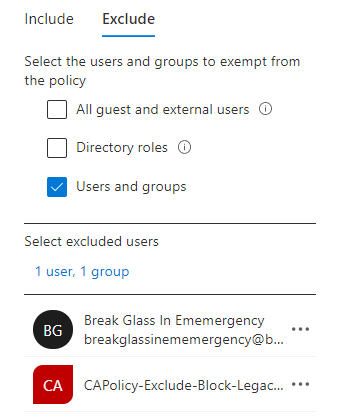
- Exclude: Break Glass Account

- Include: “All users”
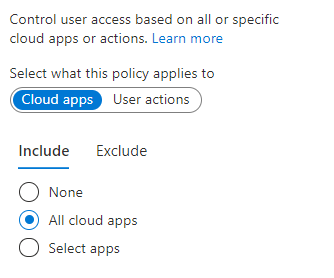
- Select Assignments -> “Cloud apps or actions” -> “All cloud apps”

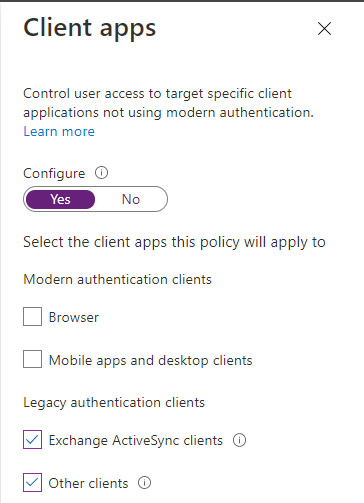
- For “Conditions” -> “Client apps” chose only the Legacy authentication clients “Exchange ActiveSync Clients” and “Other Clients”

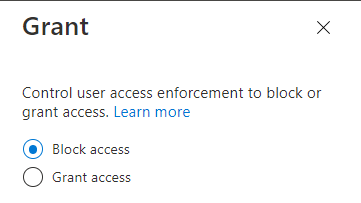
- “Access controls” -> “Grant” must be “Block access”

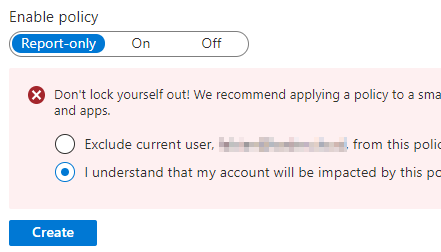
- Finally, set the policy to “Report-Only” and create it.
Do not exclude the current user from the policy. This is what the Break Glass account is for and the policy is additionally in the state Report Only.

Temporary Policy: Block legacy authentication Rollout
This policy is used in the first phase of the rollout to explicitly prohibit legacy authentication for a defined user group.
In the second phase, it will be used to allow individual users to use legacy authentication.
- Use the Entra ID (Azure AD) portal -> Security -> Conditional Access to create a new policy with the name “Common Policy: Block legacy authentication”
- Select Assignments -> “Users and groups”
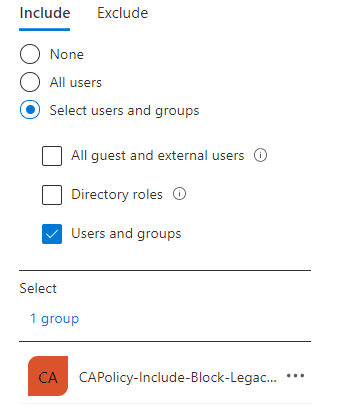
- Include: “Select users and groups” -> “CAPolicy-Include-Block-Legacy-Authentication”

- Exclude: Break Glass Account + CAPolicy-Exclude-Block-Legacy-Authentication

- Include: “Select users and groups” -> “CAPolicy-Include-Block-Legacy-Authentication”
- Select Assignments -> “Cloud apps or actions” -> “All cloud apps”

- For “Conditions” -> “Client apps” chose only the Legacy authentication clients “Exchange ActiveSync Clients” and “Other Clients”

- “Access controls” -> “Grant” must be “Block access”

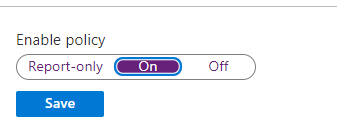
- Set the policy to “On” and create it.

Why use two conditional access policies
The conditional access policy “Common Policy: Block legacy authentication” is used exclusively for reporting accesses via legacy authentication until the final deactivation.
It is necessary because the policy “Temporary Policy: Block legacy authentication Rollout” is only valid for a defined group of users during the rollout. (CAPolicy-Include-Block-Legacy-Authentication).
Without the Report Only policy, any query based on the temporary policy would only return a subset of the users, thus skewing the results.
Effects on users
The two policies, in their current configuration, have no effect on users, as they are either for reporting purposes only or no user is yet part of the affected group.
Next step
In the next article of the series, the collected data will be used to identify the first user group for which legacy authentication can be disabled without impact.