In an Azure AD environment, legacy authentication is the Achilles heel of security.
While modern clients take into account conditional access policies and multifactor authentication, the use of legacy clients and associated protocols such as SMTP, IMAP or Exchange ActiveSync creates an often overlooked gap in this protection.
Since these protocols are not compatible with Conditional Access, they “bypass” the protection unless explicitly defined. This is not a security hole on Microsofts part, but a design decision and the impact on your own environment should therefore be well understood.
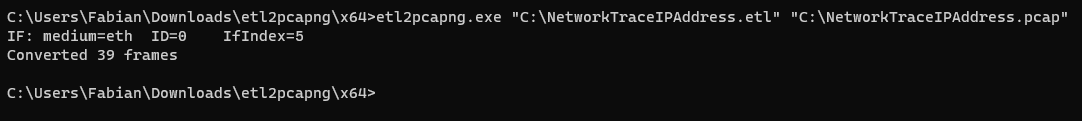
Wireshark is a powerful tool to analyze network data. However, it is another tool that needs to be regularly updated and that relies on additional software (Npcap) to capture network data.
But Windows has a built-in tool to create a network trace. And with a small additional tool the created etl file becomes a pcap file which can be analyzed without any problems. An installation of Wireshark and Npcap is therefore not necessary to capture the data.
When analyzing network problems, a simple ICMP ping is never sufficient to verify if the connection between two devices works. Normally a TCP connection to a server is needed and PowerShell comes with an appropriate cmdlet Test-NetConnection.
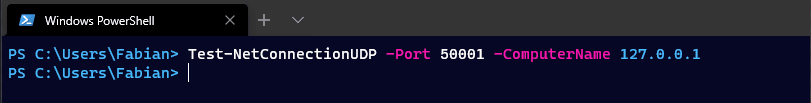
However, by default Test-NetConnection only supports TCP connections and also tests an ICMP ping each time.
So, what’s up with UDP? There is no built-in tool for analyzing stateless UDP packets, so I wrote the following two functions.
At times like these, when everybody is working from home and the whole family uses the internet as well, the traffic requirements can be tough on your internet connection. When you are using real-time collaboration tools, such as Microsoft Teams, that rely on a good and stable internet connection for voice, video and screen sharing, parallel Netflix/Disney+/Hulu/Amazon Prime traffic can make the experience subpar for everybody involved.
Thankfully it’s possible to optimize your outgoing traffic based on what services are used.
The Let’s Encrypt project has had a lasting impact on the Internet landscape. Free SSL certificates for everyone can be created automatically and signed by Let’s Encrypt. Due to the broad acceptance by browser manufacturers and cross-signing, the certificates are valid almost everywhere.
However, an automated solution is absolutely necessary due to the short validity period of 90 days. Using PowerShell in Azure Automation, a workflow can be created that takes care of certificate renewal and secure central storage.
The analysis of firewall logs in Office 365 projects repeatedly raises the question: Is this blocked IP address part of the Office 365 address range?
Thanks to PowerShell and the information published by Microsoft, the answer is only a few lines of code away.
My script “Test-IsO365IpAddress.ps1” simply needs the IP address in question and optionally the TCP/UDP port. It retrieves the current list of address ranges from Microsoft and checks if the IP address is part of one of the IP networks.