TIL; Today I Learned TIL is a blog series in which I document (for me) interesting insights.
This knowledge is possibly already documented a hundred times on the Internet. But so i can find it again i wrote it down here.
BitLocker provides a convenient way to encrypt the hard drive on computers running Windows 10 Professional.
A YubiKey is my choice for passwordless sign-in to Entra ID (Azure AD).
Blog series This is the last part of the series on “Phase out Legacy Authentication”.
Preface Enable Modern Authentication Create prerequisites Gain insights The first 90% The next 9% Endgame A lot of work lies behind you when you arrive here. Starting with the necessary preliminary work, the required changes, through reporting and maintaining exception lists.
But the biggest hurdle for the next step was definitely the last 9%. Finding and removing every exception is time-consuming and tedious.
Blog series This is part three of the six-part series on “Phase out Legacy Authentication”.
Preface Enable Modern Authentication Create prerequisites Gain insights The first 90% The next 9% Endgame Recap Having disabled the majority of users who do not use Legacy Authentication in the last article, it is now time to use the methods outlined in part three to identify the user groups that are still affected.
This data will be used to create an action plan for the deactivation of Legacy Authentication for these user groups.
The case of the... In this category I publish blog post explaining a problem and the solution but more important the analysis that lead to the root cause.
The name is a homage to “The Case of the Unexplained” from Mark Russinovich.
The error Quote Trust of the root CA is best established by deploying a trusted certificate profile to the same group that receives the SCEP certificate profile. […] To use a SCEP certificate profile, a device must have also received the trusted certificate profile that provisions it with your Trusted Root CA certificate.
Blog series This is part three of the six-part series on “Phase out Legacy Authentication”.
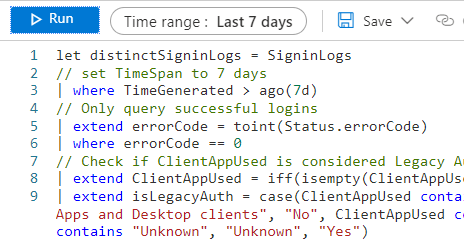
Preface Enable Modern Authentication Create prerequisites Gain insights The first 90% The next 9% Endgame Recap The first three parts of the series set the stage (1/2) for the deactivation and used Entra ID (Azure AD) workbooks and Kusto queries to identify the first usergroup.
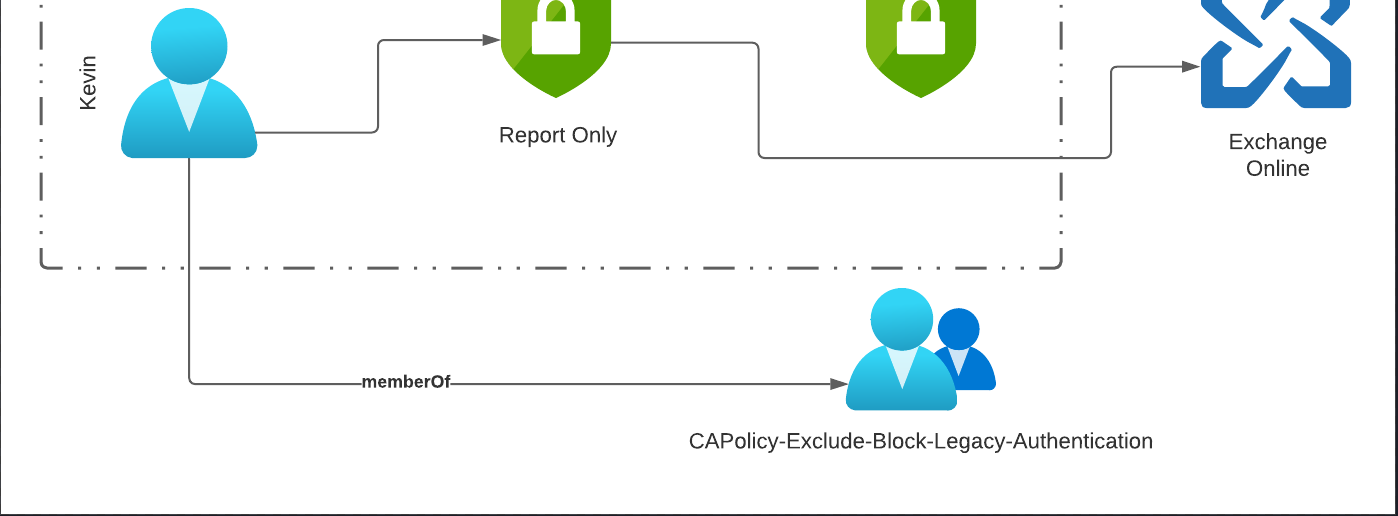
Add AAD group members To go straight ahead, the Entra ID (Azure AD) group CAPolicy-Include-Block-Legacy-Authentication must be populated with the users from the last query.
Blog series This is part three of the six-part series on “Phase out Legacy Authentication”.
Preface Enable Modern Authentication Create prerequisites Gain insights The first 90% The next 9% Endgame Recap In the first part, Modern Authentication was enabled and in the second part, the prerequisites were created to create detailed reports and to disable Legacy Authentication for individual users.
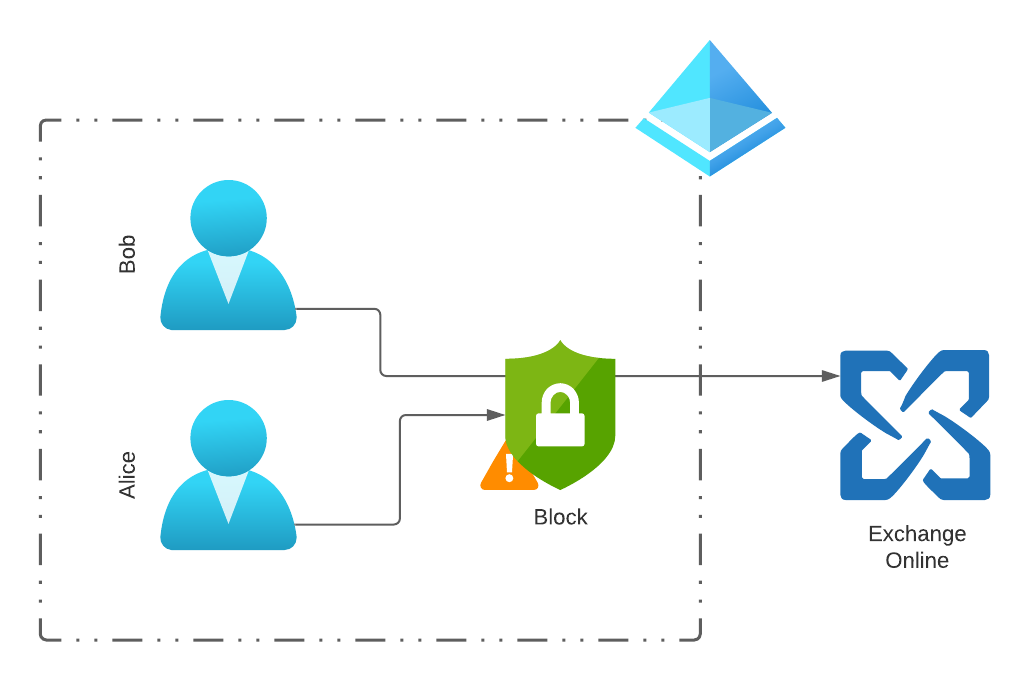
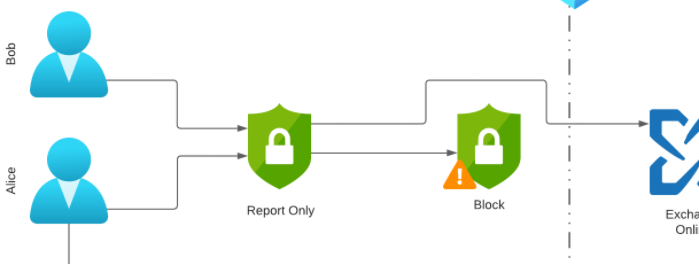
Conditional Access policy logic To better understand how it is possible to block individual users, let’s take a look at the Conditional Access Policies created and the login associated with them.