Journey To Passwordless: But why?
Preface
There is currently a lot of talk and writing about passwordless authentication in the Microsoft community.
But what does it mean in everyday life to use your own account without a password?
Which requirements have to be fulfilled and which restrictions come along with it?
In this blog series, I will provide you with an overview of the current state of the existing technologies and explore them step by step.
Blog series
- Passwordless: But why?
- Enable passwordless
- Temporary Access Pass
- FIDO2 Security keys
- Windows 10 device onboarding and Windows Hello for Business
- PowerShell administration without a password
- Microsoft Authenticator app
- Restrict FIDO2 key usage & conclusion
Why passwordless?
The first question that comes to mind: Why should I give up the password?
Passwords have always been the biggest security hole in any authentication. They are sent over the Internet every time a user signs-in, are reused by users on different services, or are chosen too weak. Blaming the user is a popular reflex, but too short-sighted. The user wants to be able to work, the security requirements are mostly just a hindrance.
Password managers offer a good way to manage the ever-increasing amount of log-ins. In an enterprise IT, however, the solution should be one identity, connected to one central Identity and Access Management (IAM) solution. Entra ID (Azure AD) offers a really good solution with the available interfaces and the long list of directly supported apps.
Attacks on identities and “weak” passwords must be minimized and made more difficult by conditional access and multifactor authentication (MFA).
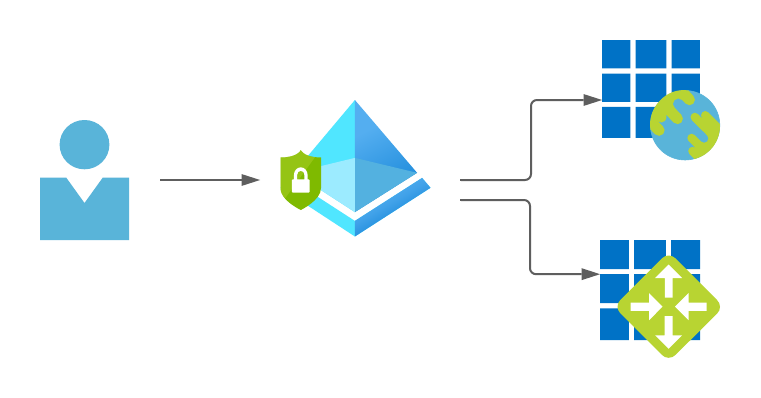
However, the current technologies for MFA do not solve the basic problem of passwords. App notifications, tokens or FIDO2 security keys increase security enormously, but do not simplify the user’s sign-in and the password is still transmitted via the network.
The only solution to stop transmitting the password is to not use passwords in the first place.
How does a passwordless authentication work?
In contrast to password-based authentication, passwordless authentication relies on techniques that have been used in a similar way for certificate-based authentication for a long time. The “key” to success lies in the use of asymmetric cryptography and the greatly simplified issuance of the key pairs required for the user.
Entra ID (Azure AD) currently supports three variants of passwordless authentication:
- Windows Hello for Business
- Microsoft Authenticator app
- FIDO2 security keys
In all three scenarios, the user must connect the corresponding device or software to their own user in Entra ID (Azure AD). A private and public key is generated, whereby only the public key is stored in Entra ID (Azure AD). The private key is stored in the TPM chip of the computer (Windows Hello), on the smartphone or in the “secure enclave” of the FIDO2 key.
During the actual sign-in to Entra ID (Azure AD), and this explanation is highly simplified, the following pattern is used:
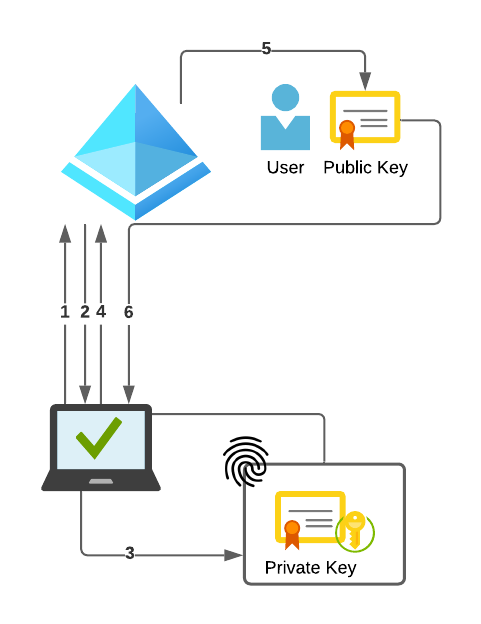
- The authentication provider on the client sends a request to Entra ID (Azure AD) during the login process.
- The Entra ID (Azure AD) responds to this request with a random and arbitrary number, the nonce.
- The client signs this nonce with the private key. It is important to note that the private key must first be unlocked using a PIN or biometric method (facial recognition or fingerprint).
- After the nonce is signed, it is sent back to Entra ID (Azure AD).
- The Entra ID (Azure AD) verifies the signature with the public part of the key and compares the nonce.
- If the nonce is valid and not older than 5 minutes, the Entra ID (Azure AD) responds with a primary refresh token (PRT).
- With this PRT the user can now access services like mail or Teams.
This illustration is, as mentioned earlier, very simplified. Depending on the variant used, even more steps are necessary and the PRT is also not used directly for accessing Outlook.
But this representation shows one thing very well. At no time a password was transmitted.
The nonce changes with every sign-in and the private key is stored protected only on the user’s device.
If you want a deeper insight into how Entra ID (Azure AD) authentication works, I recommend the really very good videos by Stuart Kwan on the topic Entra ID (Azure AD) Authentication Fundamentals.
But isn’t a PIN also a password?
No, not in the sense of authentication by username and password. It never leaves the user’s device and for a better user experience it can be replaced by a biometric method.
But of course for the end user, if no fingerprint can be used, it still feels like a password.
Next steps and the goal
The aim of this blog series is to work 100% passwordless as an administrator in a Microsoft environment. To achieve this goal, technologies that are currently still in preview are used.
Therefore, this blog series, in my current knowledge, is only suitable for experienced users or even better the administrator accounts.
In the next blog, I will make the necessary settings in Entra ID (Azure AD) to be able to use passwordless authentication at all and additionally secure the sign-ins of administrators with Conditional Access Policies.