Journey To Passwordless: Windows 10 Device Onboarding and Windows Hello for Business
Blog series
- Passwordless: But why?
- Enable passwordless
- Temporary Access Pass
- FIDO2 Security keys
- Windows 10 device onboarding and Windows Hello for Business
- PowerShell administration without a password
- Microsoft Authenticator app
- Restrict FIDO2 key usage & conclusion
Recap
The administrator account we use for passwordless sign-in has now performed its initial sign-in and registered a FIDO2 security key for permanent log-in. This initial sign-in had to be performed on an already set up device due to restrictions during Windows 10 enrollment. Unfortunately, the use of the Temporary Access Pass is not possible* during the initial setup of Windows using the out-of-box experience or Autopilot.
Now the setup of the Privileged Admin Workstation (PAW) can be performed.
*At the end of this blog I present a method with which a deployment is also possible via TAP using preview features of Autopilot and Intune.
Out-of-Box-Experience
When setting up Windows using the out-of-box experience, select “Setup for an Organization” and then the option “Sign-in with Security Key” is directly available in the Windows 10 20H2 version used here. After the successful sign-in, the computer is connected to the Entra ID (Azure AD) (Entra ID (Azure AD) Join) and enrolled in Intune if configured.
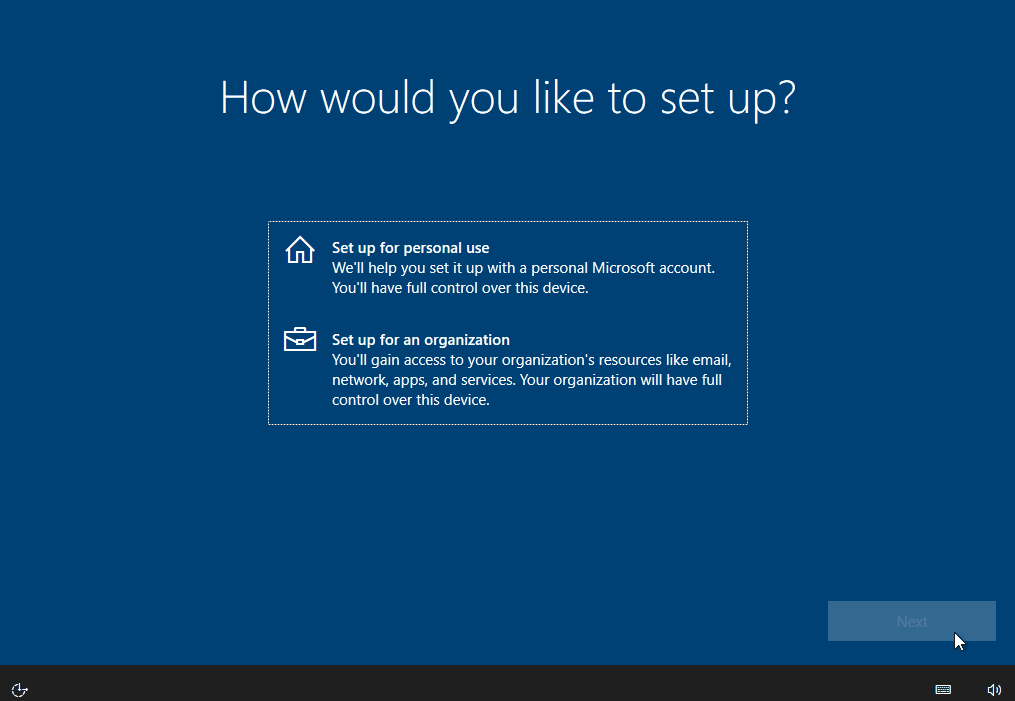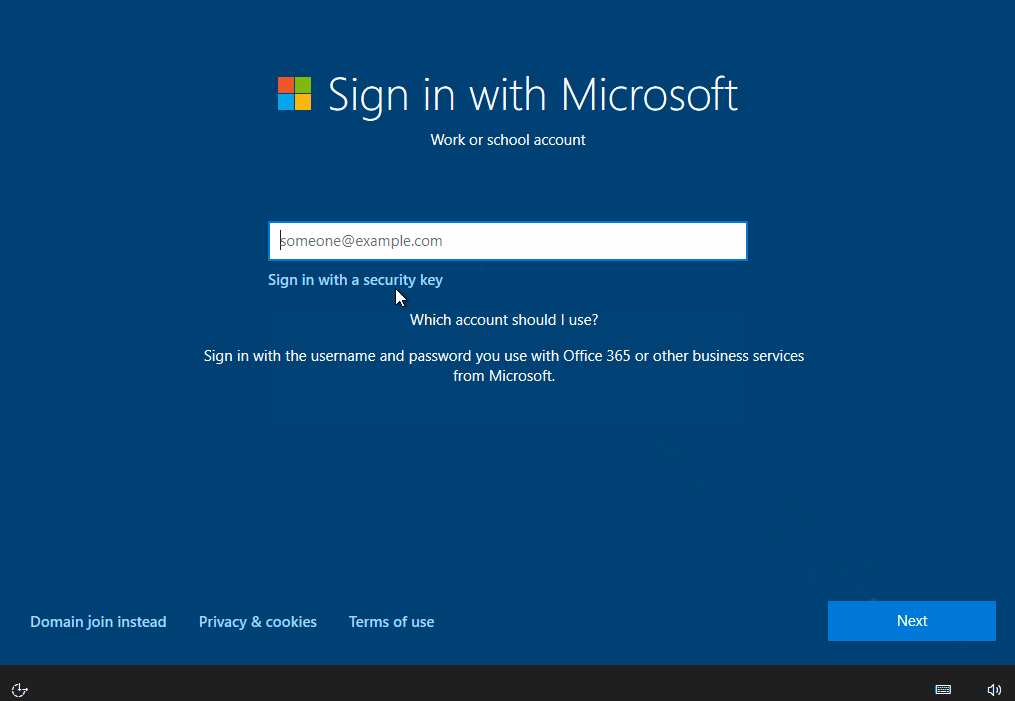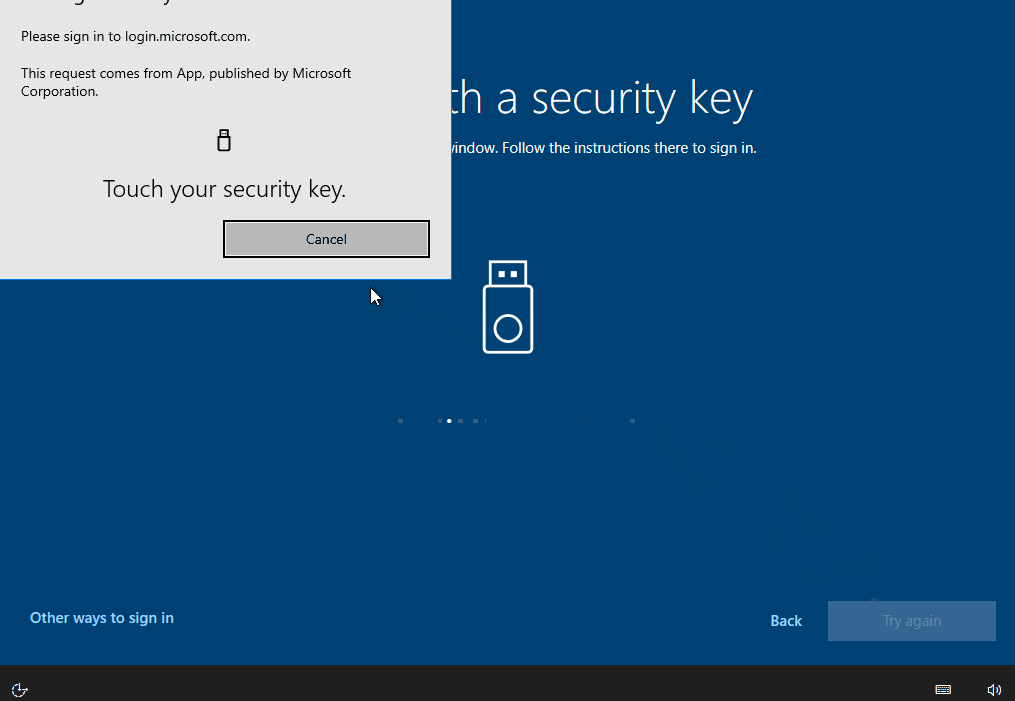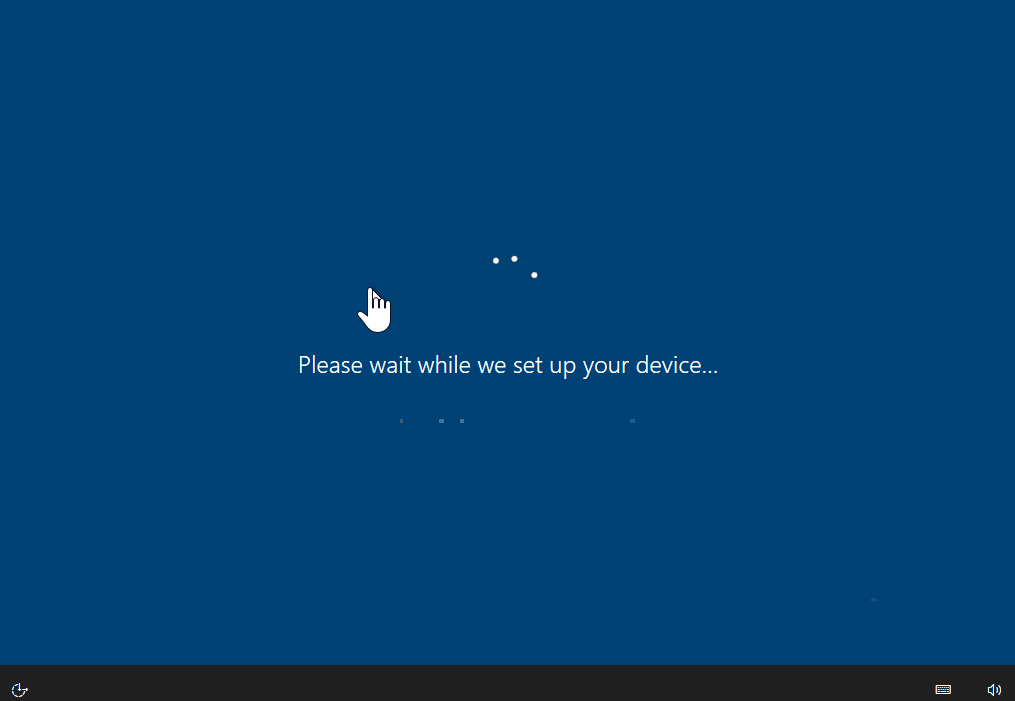
First sign in
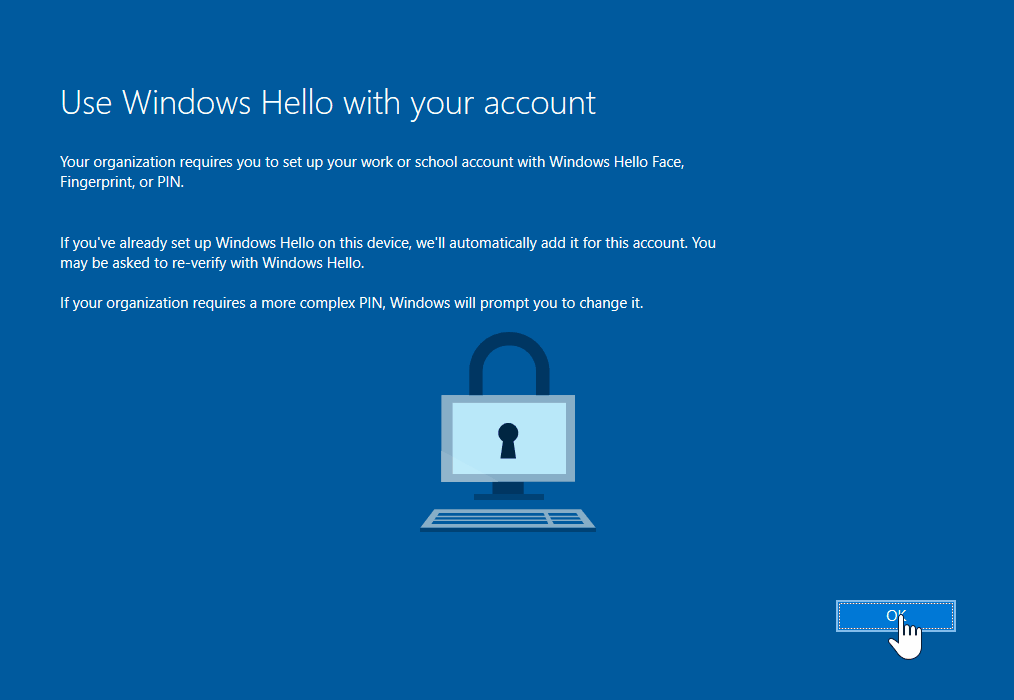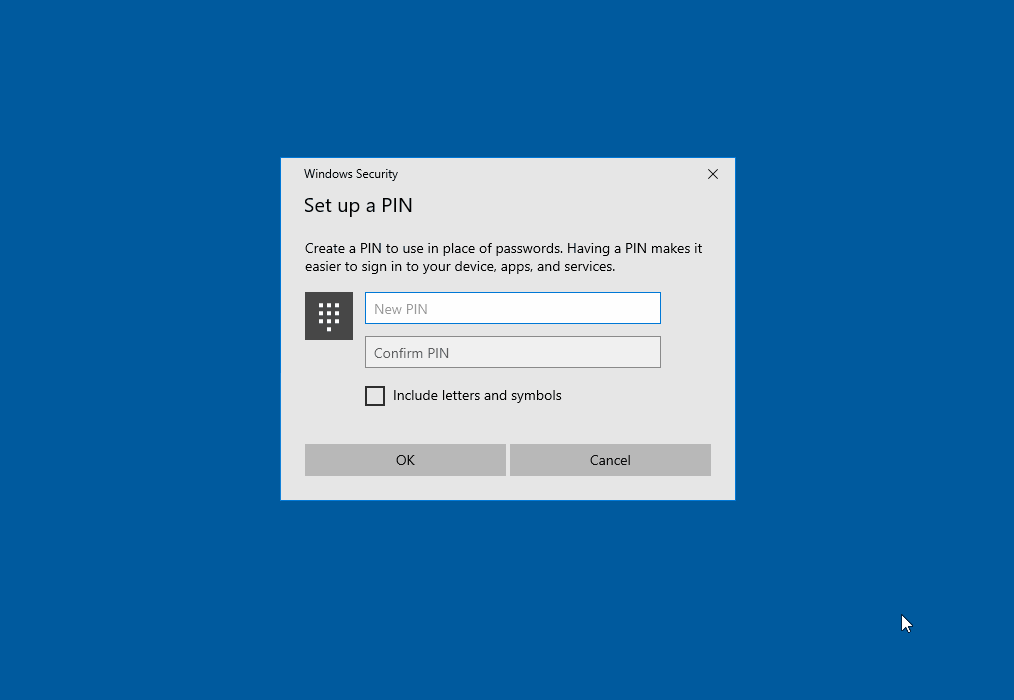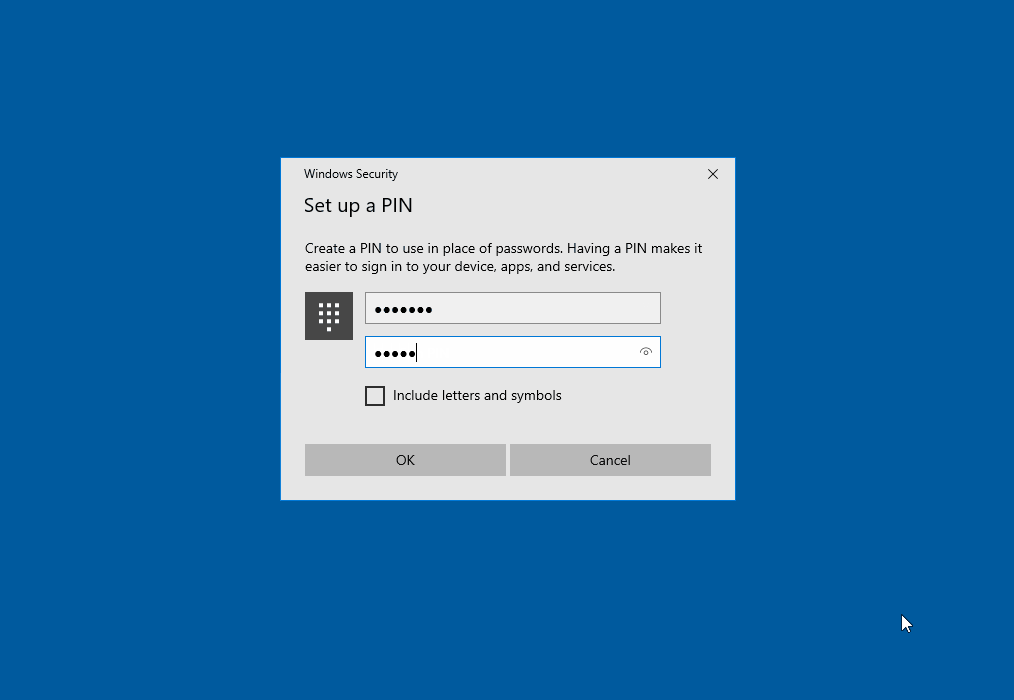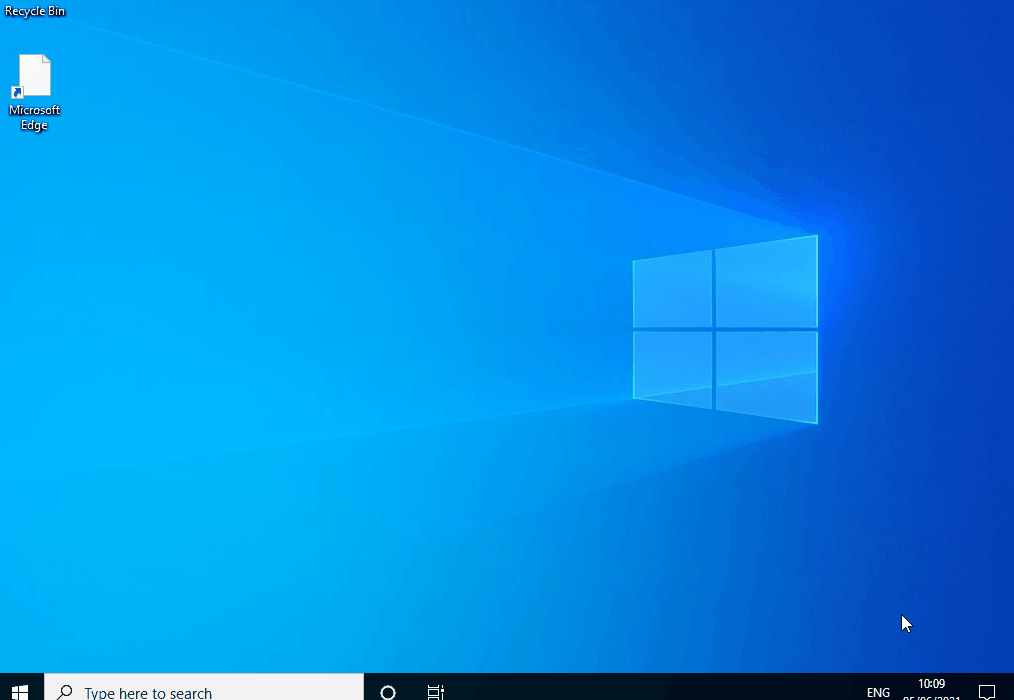
If no other settings are supplied by Intune, Windows 10 will directly enable Windows Hello for Business for the sign-in after the successful installation.
The user must assign a PIN that is only valid on this device. With this PIN, the private key for the sign-in can be unlocked in the TPM chip of the laptop. Windows thus directly promotes another method for password-free sign-in.
Configuration
In order that the sign-in to Windows can also be carried out using a security key, this must first be enabled.
Intune
If Intune is used for client management, the necessary key SecurityKey/UseSecurityKeyForSignin of the PassportForWork configuration service provider can be distributed starting from Windows 1903.
This setting can be enabled in the “Windows enrollment area using the Windows Hello for Business menu item. This setting applies to all supported Windows 10 devices in the company.
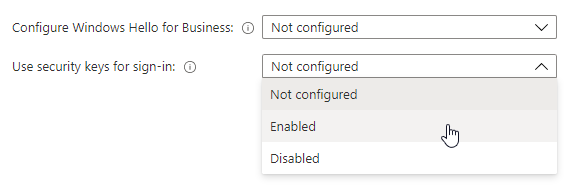
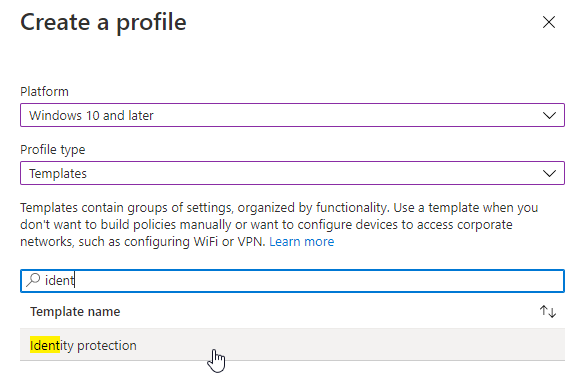
If a more targeted rollout is desired, a “Configuration Profile” of the type “Identity protection” must be created and assigned to the corresponding devices.
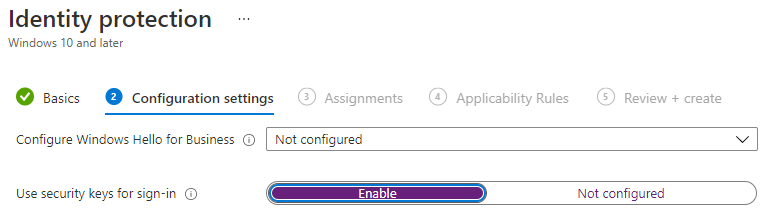
Registry
For a quick test, the necessary configuration can also be enabled via registry value.
HKLM\SOFTWARE\Microsoft\Policies\PassportForWork\SecurityKey
UseSecurityKeyForSignIn = 1
Type: DWORD
The easiest way to do it is using this PowerShell snippet.
New-Item -Path "HKLM:\SOFTWARE\Microsoft\Policies\PassportForWork\SecurityKey" -Force
New-ItemProperty -Path "HKLM:\SOFTWARE\Microsoft\Policies\PassportForWork\SecurityKey" -Name UseSecurityKeyForSignIn -Value 1 -PropertyType DWord -Force
Login using FIDO2 Security Key
FIDO2 USB-C
It is enough to connect the FIDO2 security key to the device and unlock it with a touch. If a security key is used that requires a PIN for use, this must also be entered. In the case demonstrated here, the fingerprint directly unlocks the security key, which makes the login experience similar to unlocking a smartphone.

FIDO2 Bluetooth
If a Bluetooth-capable FIDO2 Security Key is used, it must be connected to Windows once.
The detailed instructions can be found here
Automatically lock computer
Unfortunately, there is currently no way to automatically lock the computer when the FIDO2 security key is removed. In the case of a Bluetooth key, this feature would also not be useful, because the key is not active all the time to save battery power, but only when it is needed.
If you want to play a little bit, be aware that the security key registers as a HID-compliant fido device. This knowledge can be used to check if the key is still in the computer.
Here is an example that should only be seen as a POC and in no case as a usable implementation.
# Check if the FIDO2 key is still present
while ( (Get-CimInstance -Class Win32_PnpEntity | ? Caption -match "HID-compliant fido") ) {
Write-Verbose "FIDO2 Key present..."
Start-Sleep -Seconds 1
}
# Lock workstation when removed
Invoke-Command -ScriptBlock { rundll32.exe user32.dll,LockWorkStation }
Windows Hello for Business
With Windows Hello for Business, Microsoft offers a passwordless way to sign-in to Windows 10. The sign-in is not limited to the use of the PIN, but also supports biometric features such as the use of a camera or a built-in fingerprint reader.
Unlike Windows Hello, Windows Hello for Business only uses key- or certificate-based authentication.
The implementation of Windows Hello for Business in an enterprise environment including PKI is beyond the scope of this blog series and will therefore not be discussed in detail.
PAW Deployment with Autopilot and Intune
Even though there is no official support for the use of TAP in the deployment of Windows 10, two preview features can be used to enable a scenario where this is possible.
Prerequisites are the use of the deployment mode “Self-Deploying” and the setting “EnableWebSignIn” for the Authentication CSP.
Device configuration profile
Two profiles are necessary to deploy the configuration properly. Both profiles must be assigned to the device group, in my case the group “Self deploying admin workstation”.
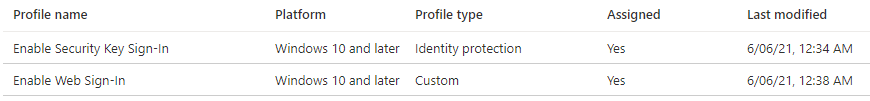

Enable Security Key Sign-In
| Profile type: | Identity protection |
| Use security keys for sign-in | Enabled |

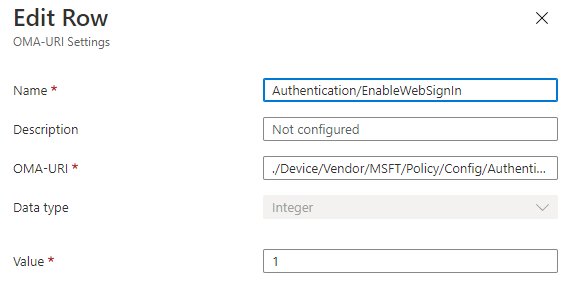
Enable Web Sign-In
| Profile type: | Identity protection |
| Name | Authentication/EnableWebSignIn |
| OMA-URI | ./Device/Vendor/MSFT/Policy/Config/Authentication/EnableWebSignIn |
| Data type | Integer |
| Value | 1 |
Auto Pilot profile
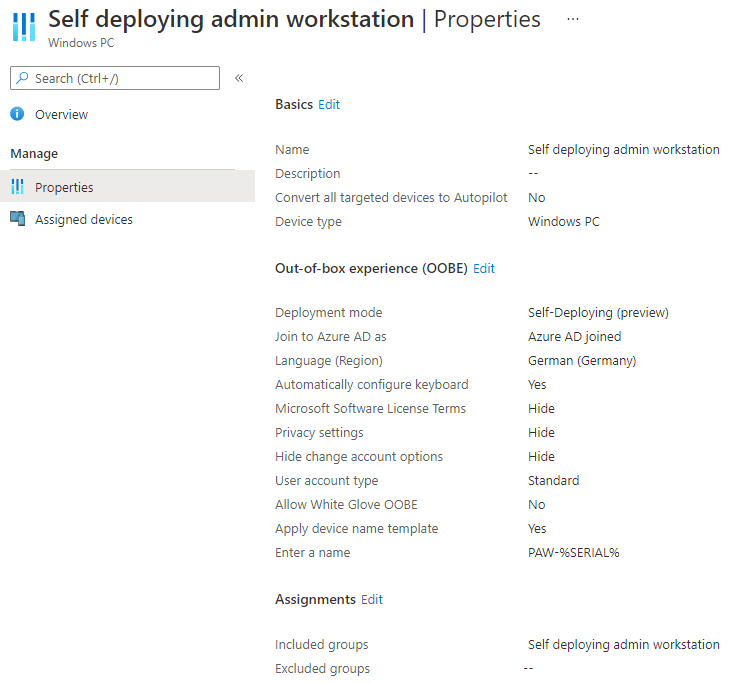
In addition, a Deployment Profile is set up for Autopilot. It is important to select the deployment mode “Self-Deploying (preview)” and assign this profile to the Entra ID (Azure AD) group.
Autopilot
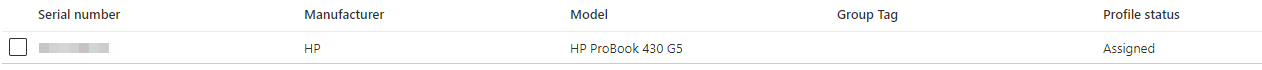
In the section Windows Autopilot devices the device must have been added and the Profile status must be set to “Assigned”. It is important that only devices that use a TPM 2.0 chip that supports TPM attestation are supported.
The computer can then be started, preferably directly via Ethernet connection, and the device performs the complete deployment without user intervention.
Virtual machines
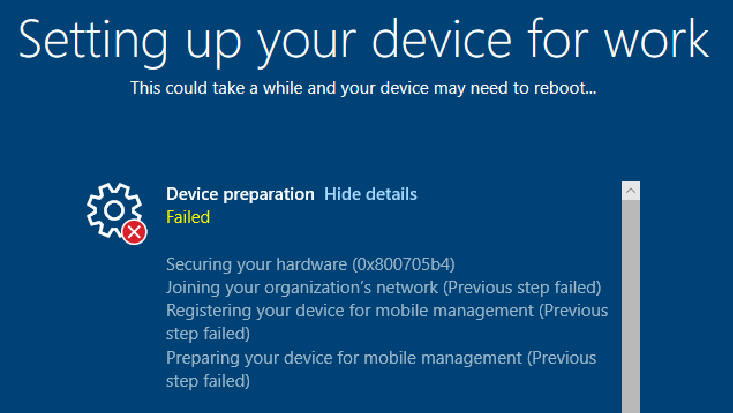
I did not manage to deploy a virtual machine (VMware) in this mode in my test. The official documentation states that Hyper-V virtual TPMs are not supported, which seems to be the case for virtual TPMs in general.
The installation aborts with error 0x800705b4 in the step “Securing your hardware”.
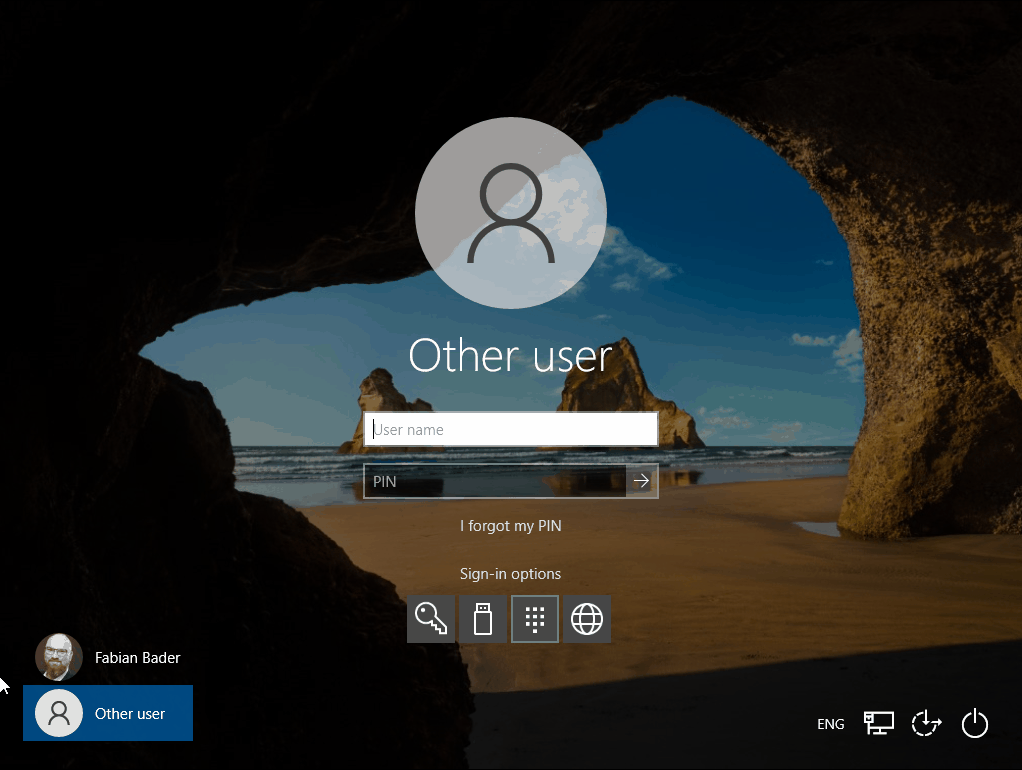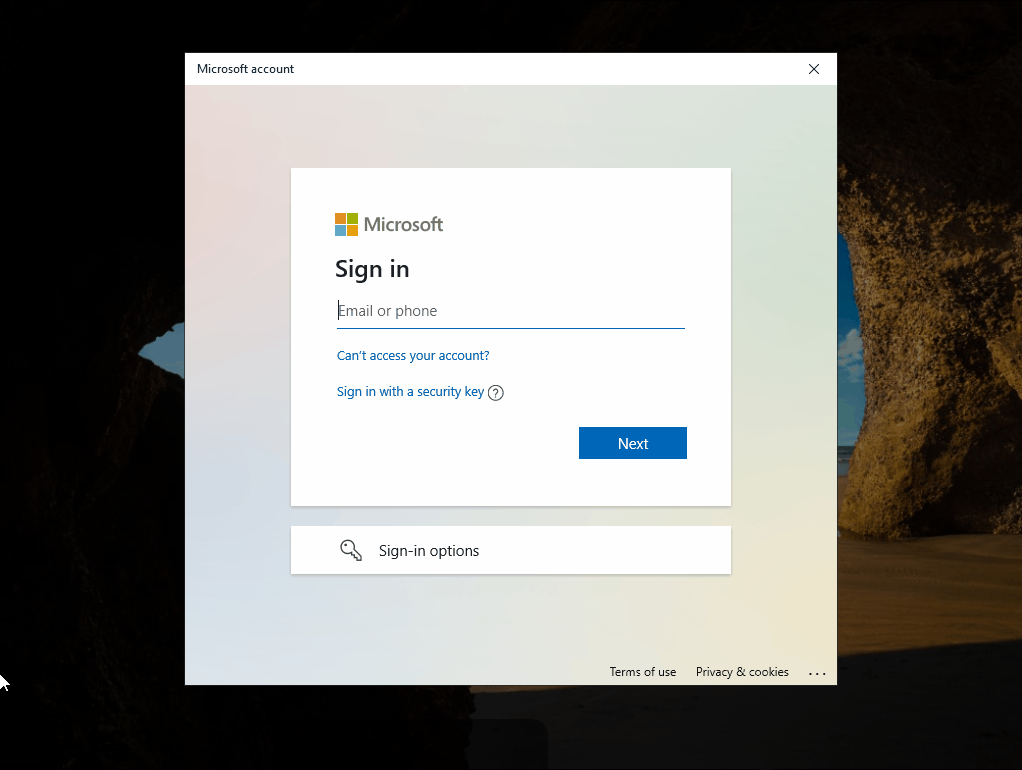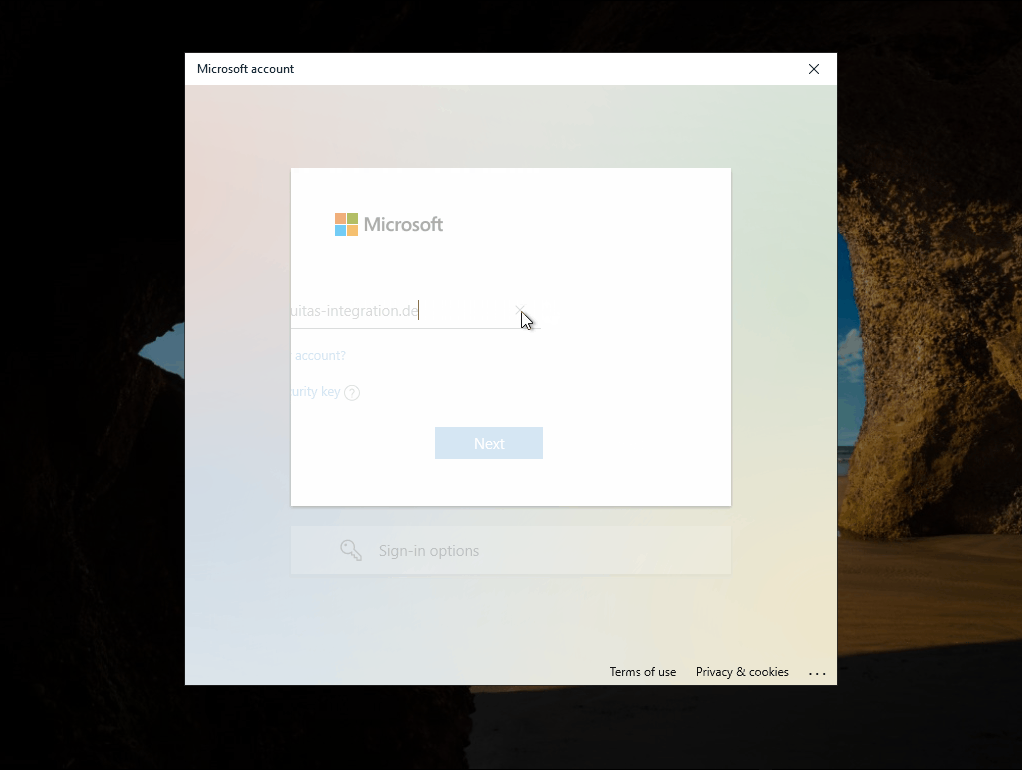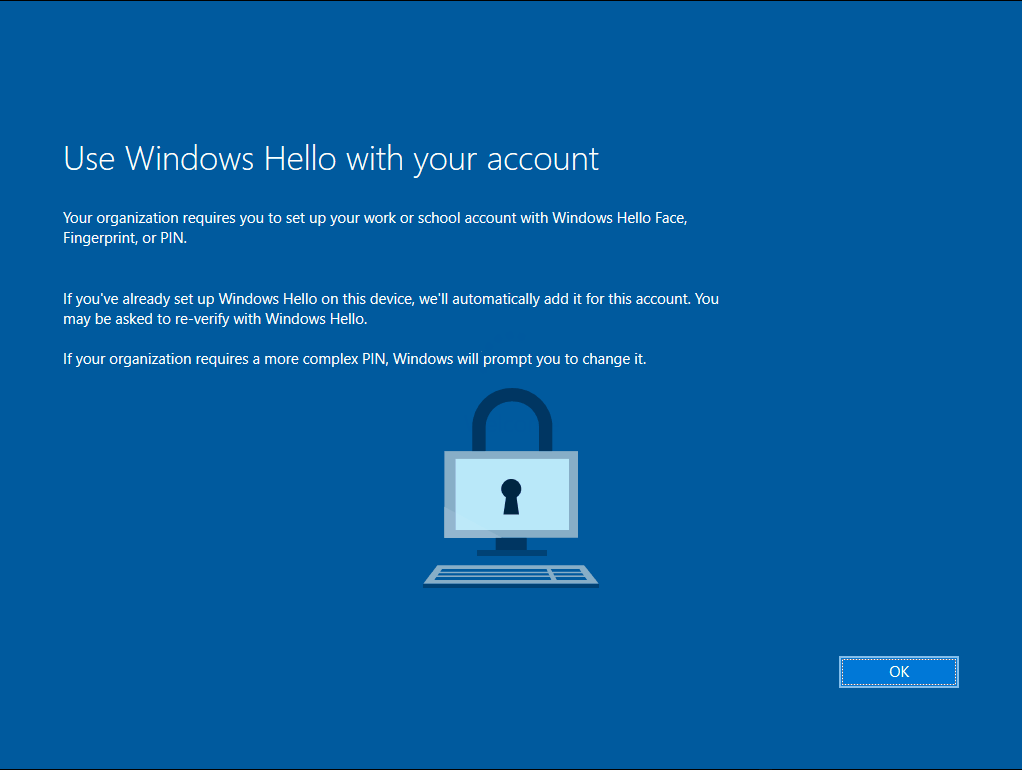
Sign-in via web sign-in
During sign-in, the user is presented with four different sign-in options under “Sign-in options”.
| Sign-in using username and password | |
| Sign-in using FIDO2 security key | |
| Sign-in using Windows Hello for Business PIN | |
| Sign-in using Web Sign-In |
Web Sign-In utilizes the browser of the operating system for the sign-in, which is what makes the use of a Temporary Access Pass possible in the first place. Thus, no special TAP mode is used, but all login methods available in the browser.
After the successful sign-in, a WHFB PIN must be assigned and then of course the FIDO2 Security Key registered.
Self-deploying Mode with Web Sign-In
Intune’s self-deploying mode and Web Sign-In therefore offer a solution for the initial deployment of an admin workstation in a passwordless environment.
However, it is important to consider that
- The device is not assigned to the user in Intune
- The user does not have access to BitLocker recovery keys for the device.
- The user cannot install personally assigned apps from the Company Portal.
- In environments with ADFS the value
Authentication/ConfigureWebSignInAllowedUrlmust be set to prevent CVE-2021-27092 - Windows 10 is supported from version 1903 onwards
- Web sign-in and self-deploying is only supported on Entra ID (Azure AD) joined computers.
- (Conditional Access seems to be partially not supported**)
Especially the fact that not every user can access the BitLocker recovery key is not necessarily a disadvantage. As Stephen Shkardoon describes in his Blog article “All my Intune users could become Local Administrators and it’s a Feature?” this feature is also a potential entry point for attackers to get elevated privileges on their own device.
As far as conditional access is concerned, this probably only affects the initial onboarding. After the successful installation, it is possible to check whether the device is compliant / managed during the user login.
If you have further information about restrictions, please contact me.
Next steps
In the next blog, I’ll take a closer look at the limitations in the day-to-day use of FIDO2-based sign-in and provide workarounds for known issues.