Journey To Passwordless: Microsoft Authenticator App
Blog series
- Passwordless: But why?
- Enable passwordless
- Temporary Access Pass
- FIDO2 Security keys
- Windows 10 device onboarding and Windows Hello for Business
- PowerShell administration without a password
- Microsoft Authenticator app
- Restrict FIDO2 key usage & conclusion
Recap
So far, we have only used FIDO2 security keys and Windows Hello for Business for sign-in. Unfortunately, there is still a gap in order to get along completely without a password. Microsoft does not currently support FIDO2 sign-in on Android or iOS, so a password would be required for sign-in on the smartphone. But there is a solution for this as well:
The Microsoft Authenticator app.
Authenticator app
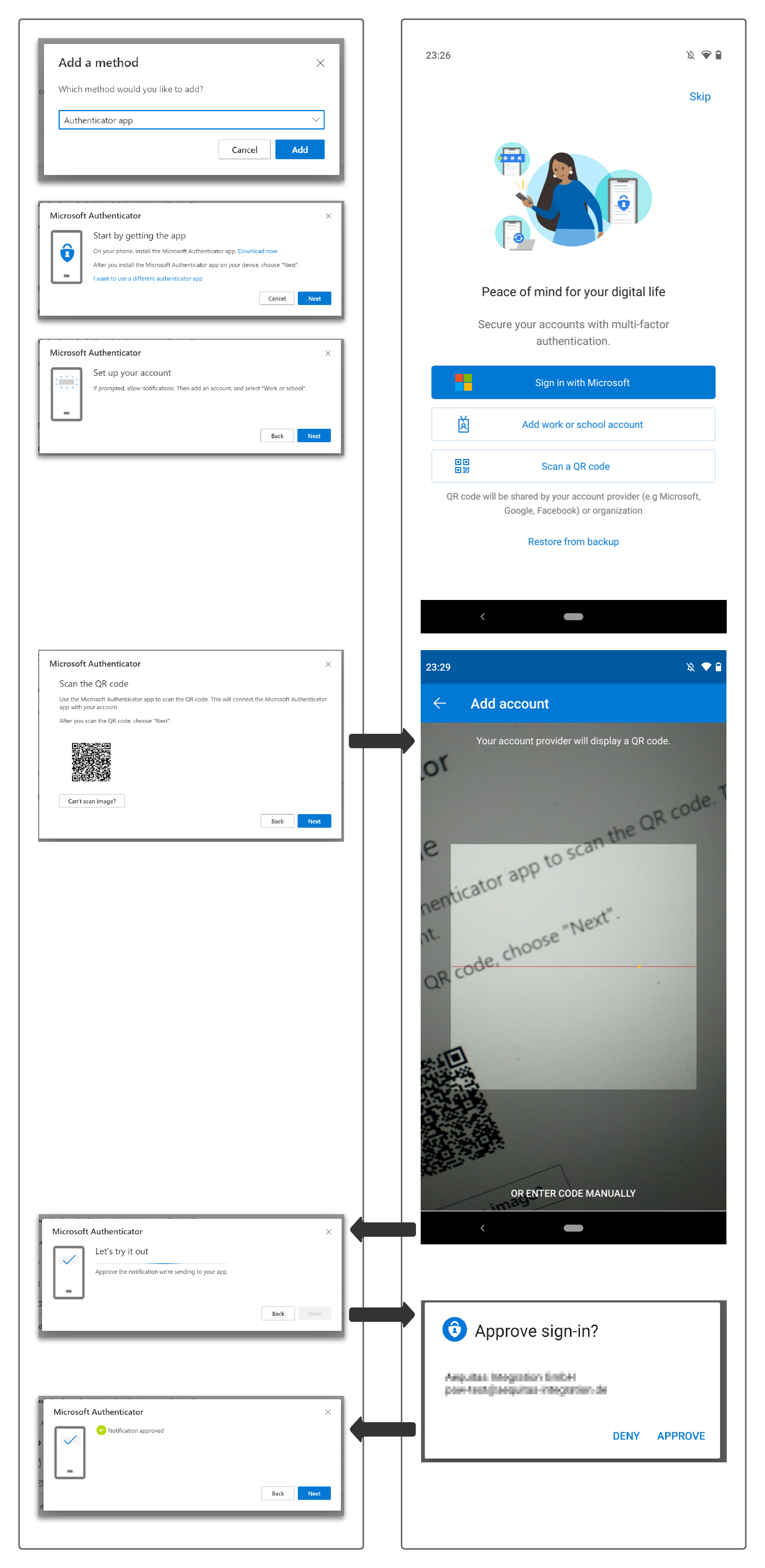
To be able to use the passwordless sign-in via Authenticator app, it must first be added as a second factor in My Security Portal. It is best to install the app on your smartphone in advance and then start the process.
The setup is done quickly:
- Select
Add Work or School Account - Scant the QR code
- Approve the notification
Enable phone sign-in
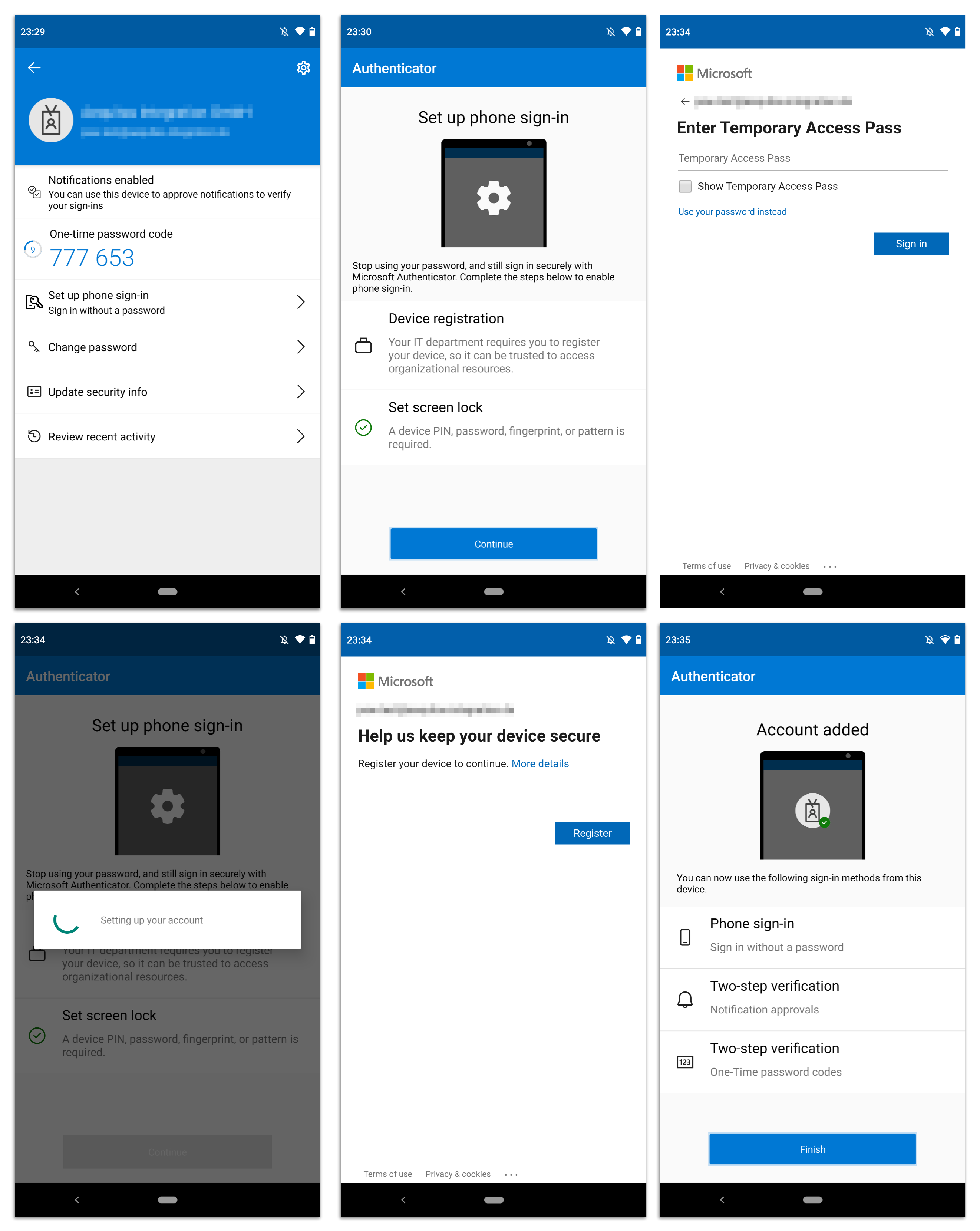
The steps described above are only half the job. Now the phone Sign-In feature must be enabled on the smartphone. The following requirements must be met in order to use the feature:
- The smartphone must be protected by a screen lock.
- The smartphone must be registered with Entra ID (Azure AD).
It is therefore a good idea to perform this setup directly during onboarding.
In the authenticator app, the account must be selected and the registration started via “Set up phone sign-in”.
For the verification, you have to sign-in again with the TAP and then register the phone with the Entra ID (Azure AD). This requirement is at the same time a problem for people with many accounts in multiple tenants. A device can only be registered in one Entra ID (Azure AD) at a time, so this feature is effectively limited to one account.
Sign-in to Windows 10
After the successful setup, this type of sign-in can be used on any supported device. This includes not only the smartphone itself, but also the Windows 10 device.
For this to be possible, the Web Sign-in login option must be enabled on the device.
Now it is possible to select it during sign-in and after entering the user name, a number is displayed that you must select on your smartphone. A corresponding notification is now displayed on the smartphone. By default, it is necessary to unlock the Authenticator app. This increases security and should not be disabled. After unlocking, the displayed number can now be selected and confirmed.
And voilà, a short time later you are signed-in to your Windows 10 device.
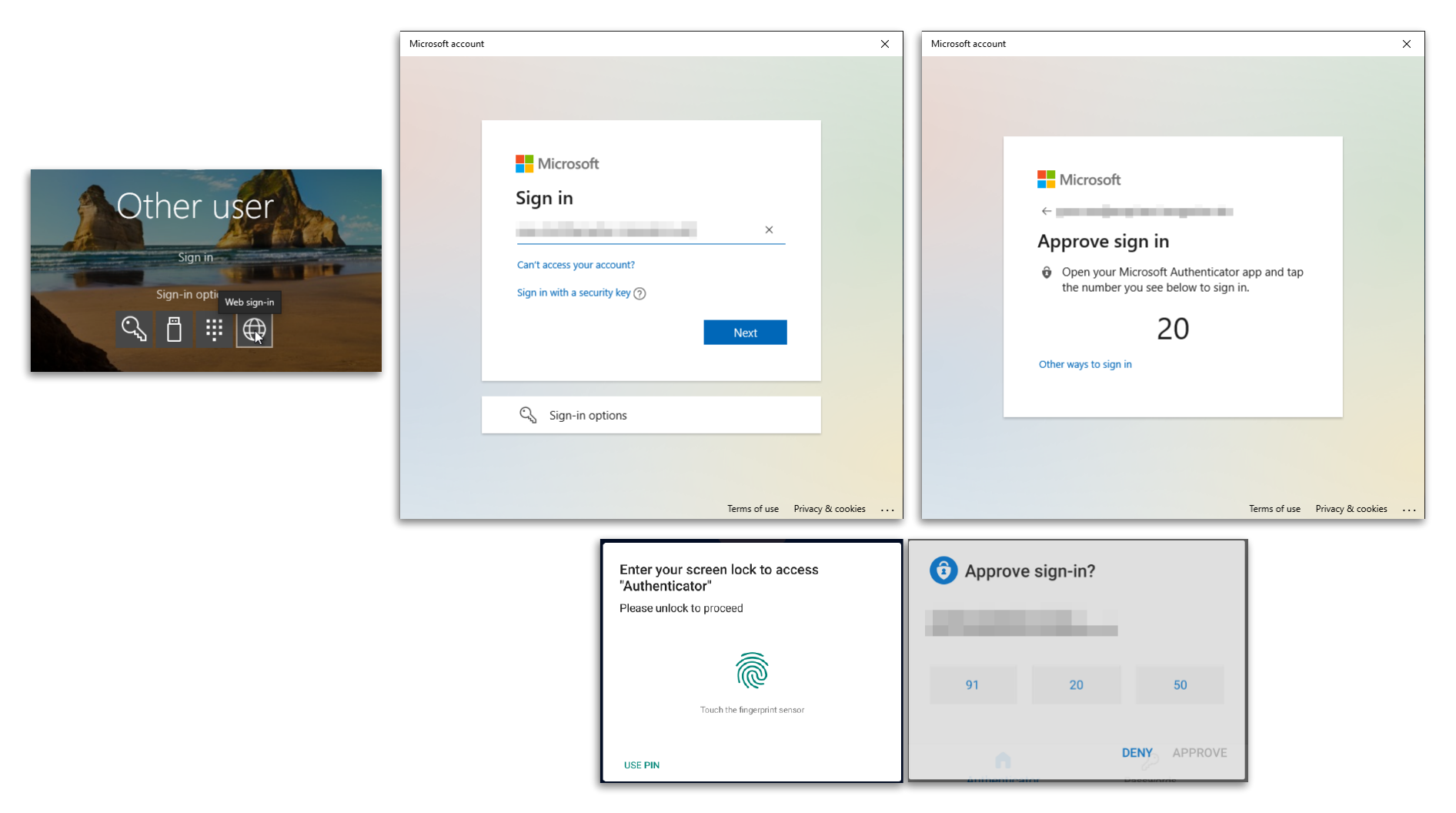
If the sign-in via authenticator app is not displayed directly, you have to select this option manually via “Other ways to sign-in”.
A look behind the scenes
Enduser
The security info portal will show the user the different sign-in options.
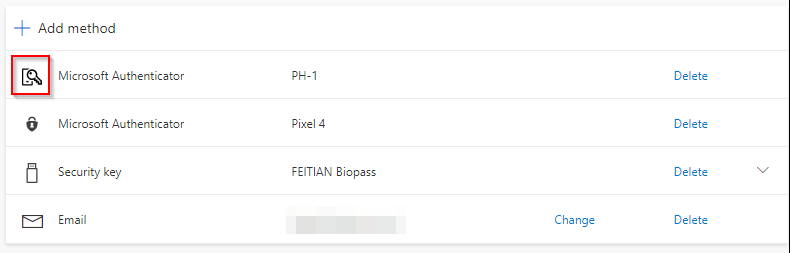
The respective icons distinguish which functions are active.
| Icon | Description |
|---|---|
| Microsoft Authenticator App used as second factor | |
| Microsoft Authenticator App with enabled Phone sign-in | |
| FIDO2 security key |
Administrator
There are several ways for the admin to detect whether a user has enabled the passwordless feature of the Authenticator app or not.
Azure AD portal
In the Entra ID (Azure AD) Portal, all registered authentication methods are displayed, but at first glance there is no difference.
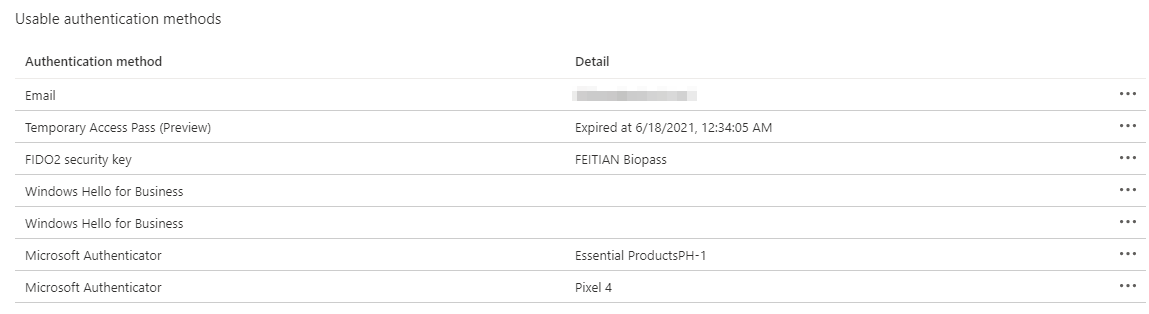
Only when you look at the “View details” submenu does it become clear whether a Microsoft Authenticator uses phone sign-in or not. On the left, the Authenticator app is used purely as a second factor, while the Phone Sign-In option is enabled on the right. The Entra ID (Azure AD) registered device is also displayed here.

Under the “Devices” menu item, the registered device is also displayed and thus directly linked to the user.
Graph Explorer
A clearer view is available in the Graph Explorer.
There the required information can be retrieved via the authentication methods endpoint.
https://graph.microsoft.com/beta/users/[userUPN]/authentication/methods
Three entries are returned in the dataset.
The data type #microsoft.graph.microsoftAuthenticatorAuthenticationMethod is returned twice and #microsoft.graph.passwordlessMicrosoftAuthenticatorAuthenticationMethod once.
The device with the additional passwordlessMicrosoftAuthenticatorAuthenticationMethod data type is the device enabled for Phone Sign-In. The property deviceTag is also different here, instead of SoftwareTokenActivated the value Android is returned.
{
"@odata.type": "#microsoft.graph.passwordlessMicrosoftAuthenticatorAuthenticationMethod",
"id": "h7Jk7MyU0Mtb7bWh_C1codHgLa7awTGx9gp8YkVD_TA1",
"displayName": "Essential ProductsPH-1",
"creationDateTime": "2021-06-17T21:35:07Z",
"createdDateTime": "2021-06-17T21:35:07Z"
},
{
"@odata.type": "#microsoft.graph.microsoftAuthenticatorAuthenticationMethod",
"id": "00ca7d21-cc09-4e3c-84e7-be2acf86d4cd",
"displayName": "Essential ProductsPH-1",
"deviceTag": "Android",
"phoneAppVersion": "6.2105.3263",
"createdDateTime": "2021-06-17T21:35:07Z",
"clientAppName": "microsoftAuthenticator"
},
{
"@odata.type": "#microsoft.graph.microsoftAuthenticatorAuthenticationMethod",
"id": "c38dac1e-9061-46ec-bcb6-8039e33a0044",
"displayName": "Pixel 4",
"deviceTag": "SoftwareTokenActivated",
"phoneAppVersion": "6.2105.3263",
"createdDateTime": null,
"clientAppName": "microsoftAuthenticator"
}
Limitations
As already mentioned, the biggest constraint is the restriction to one account per smartphone. Technically, this makes sense, of course, since the device has to be registered in Entra ID (Azure AD).
Unfortunately, it is also not possible to connect multiple accounts to one smartphone from one Entra ID (Azure AD). In my tests, this was reported with the not very informative error message

Next steps
In the next blog post, I’ll look at how to restrict what kind of FIDO2 security keys can be used and draw a conclusion.