Journey To Passwordless: PowerShell administration without a password
Blog series
- Passwordless: But why?
- Enable passwordless
- Temporary Access Pass
- FIDO2 Security keys
- Windows 10 device onboarding and Windows Hello for Business
- PowerShell administration without a password
- Microsoft Authenticator app
- Restrict FIDO2 key usage & conclusion
Recap
By now, the admin can sign-in to a Windows 10 computer without a password and, as long as a supported browser is used, to the web portals. Even a 100% passwordless Intune deployment has been possible with a few tricks.
But how does this setup perform in everyday life. And by everyday life, in this case I don’t mean using the countless portals …
PowerShell administration without a password
but using PowerShell modules.
In my test I checked if a sign-in with an Entra ID (Azure AD) Joined Device (AADJ), but also from a non Entra ID (Azure AD) Joined Device (NJ) is possible.
| Module | Version | AADJ-PwSh5 | AADJ-PwSh7 | NJ-PwSh5 | NJ-PwSh7 | Device Login |
|---|---|---|---|---|---|---|
| MSOnline | 1.1.183.57 | ⛔ | ⛔ | ⛔ | ⛔ | ⛔ |
| AzureADPreview | 2.0.2.136 | ⛔ | ⛔ | ⛔ | ⛔ | ⛔ |
| ExchangeOnlineManagement | 2.0.5 | 👍 | Browser-Login | ⛔ | Browser-Login | ⛔ |
| Az.Accounts | 2.3.0 | 👍 | Browser-Login | ⛔ | Browser-Login | 👍 |
| Microsoft.Graph | 1.6.0 | 👍 | Browser-Login | ⛔ | Browser-Login | 👍 |
The test results are very mixed. In any case, it can be said that working with an AADJ device is much more convenient. However, it is also possible to work without a Entra ID (Azure AD) joined device, sometimes via a device login flow or using PowerShell v7.
When signing-in to an AADJ, the connected Windows user is recognized directly in most cases and can be used without further login. For the unsupported modules, no option for a sign-in via security key is presented.
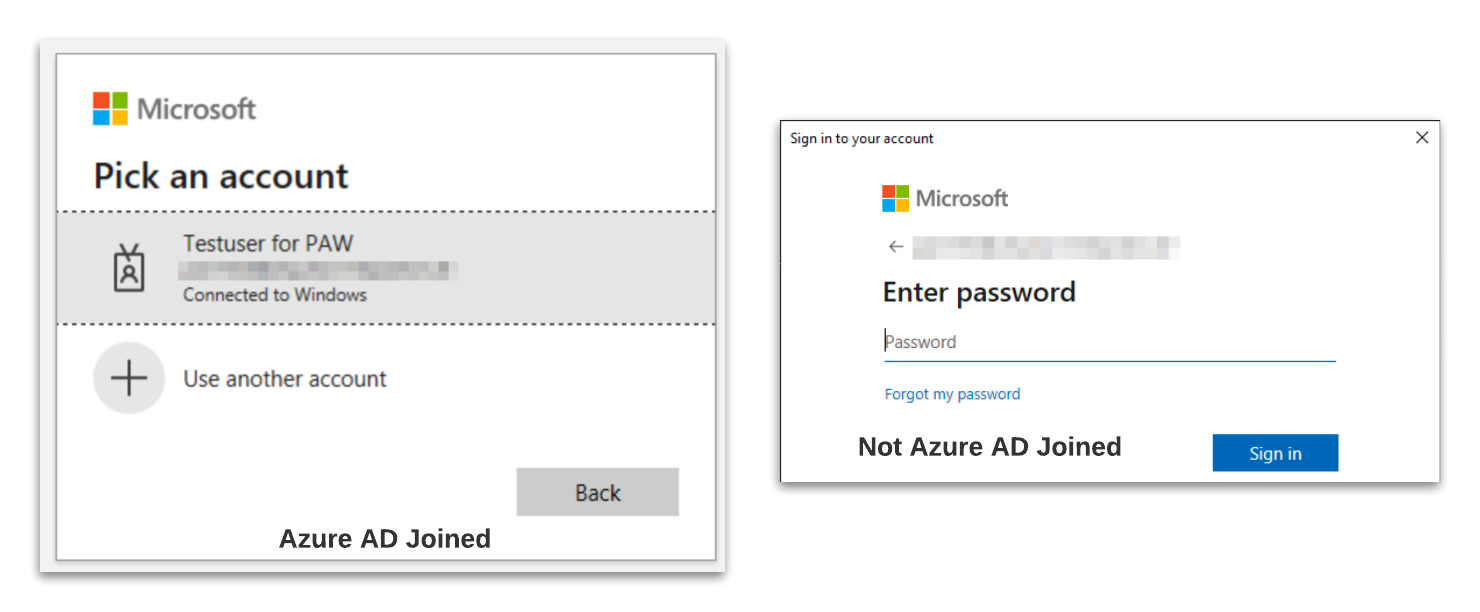
A very good alternative is the use of PowerShell 7, here the browser is always used for the sign-in by default. Since the Internet Explorer engine is not available here, the module developers have directly used an alternative.
If this is not possible, the Device Login Flow is another convenient alternative.
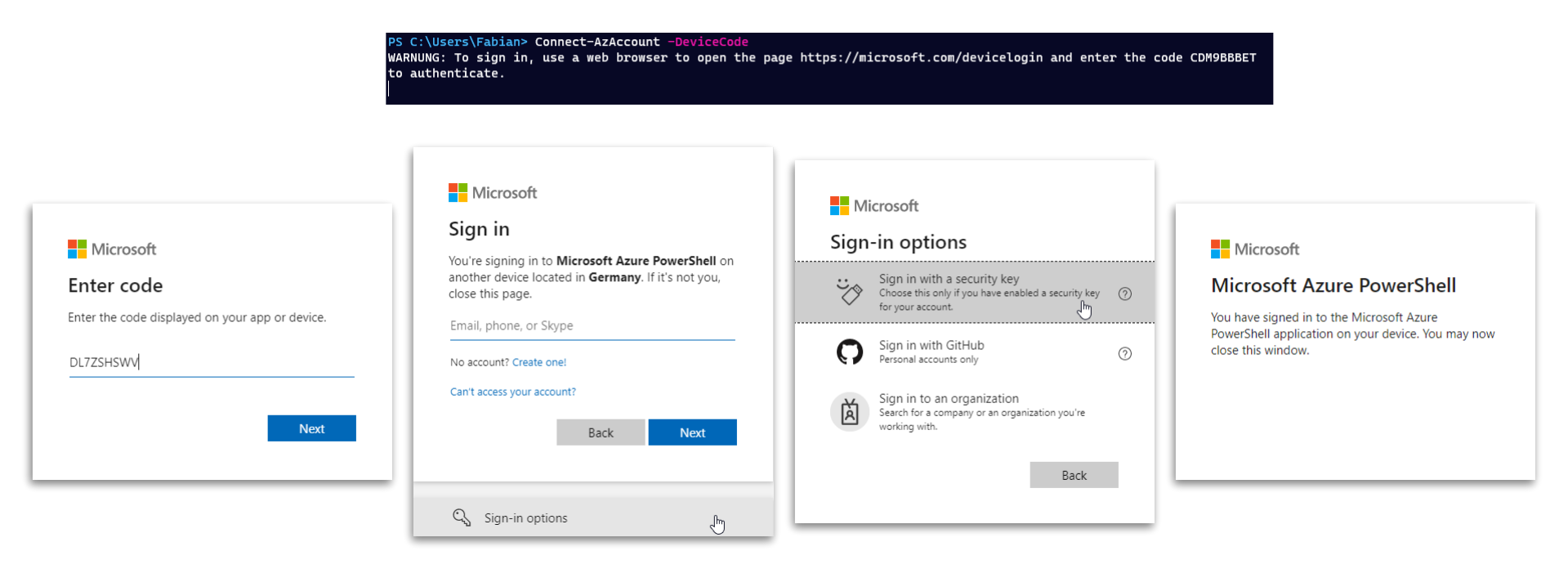
What is Device Login Flow?
Device Login Flow means sign-in via browser but with manual input. A URL and a device code are displayed, both can be used on the same or another computer for the sign-in. This is e.g. also very helpful on computers which do not use a GUI.
- the sign-in is initiated
- the admin opens https://microsoft.com/devicelogin and enters the device code shown
- after that a sign-in is possible using a security key
After successful sign-in, the browser window can be closed and the PowerShell module is connected.
Tom Aafloen has written a good article on how to initiate a device login yourself and use the created access token along for the modules that are not actually supported.
Feedback to MSFT
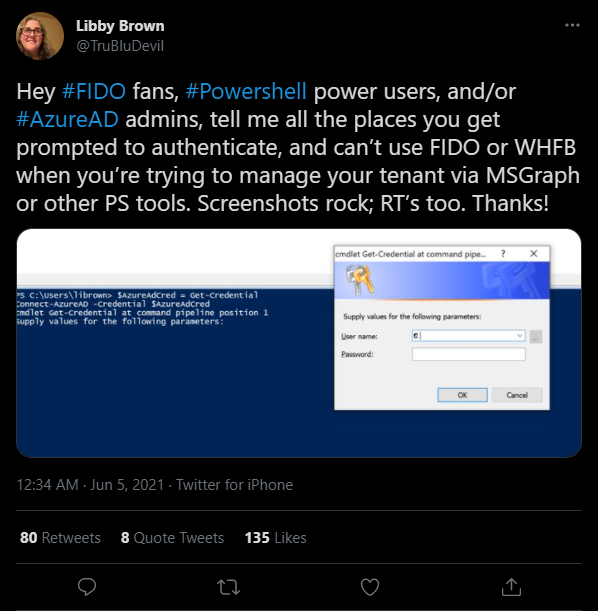
Libby Brown (@TruBluDevil) is currently collecting all modules and features where you would like to see FIDO support. So if you think of anything else, feel free to reply directly on Twitter.