Journey To Passwordless: Enable passwordless
Blog series
- Passwordless: But why?
- Enable passwordless
- Temporary Access Pass
- FIDO2 Security keys
- Windows 10 device onboarding and Windows Hello for Business
- PowerShell administration without a password
- Microsoft Authenticator app
- Restrict FIDO2 key usage & conclusion
Enable passwordless
Before things can get started and the first admin is able to work without a password, a few functions have to be enabled in Entra ID (Azure AD). Optionally, sign-ins in the browser are additionally secured by a conditional access policy.
Licenses
All features used for Passwordless do not require additional licenses.
However, to make things complete, I use Conditional Access Policies and these require the Entra ID (Azure AD) Premium P1 licenses. This is included in many Microsoft 365 Suite license packages, but can also be purchased separately.
Conditional Access Policy
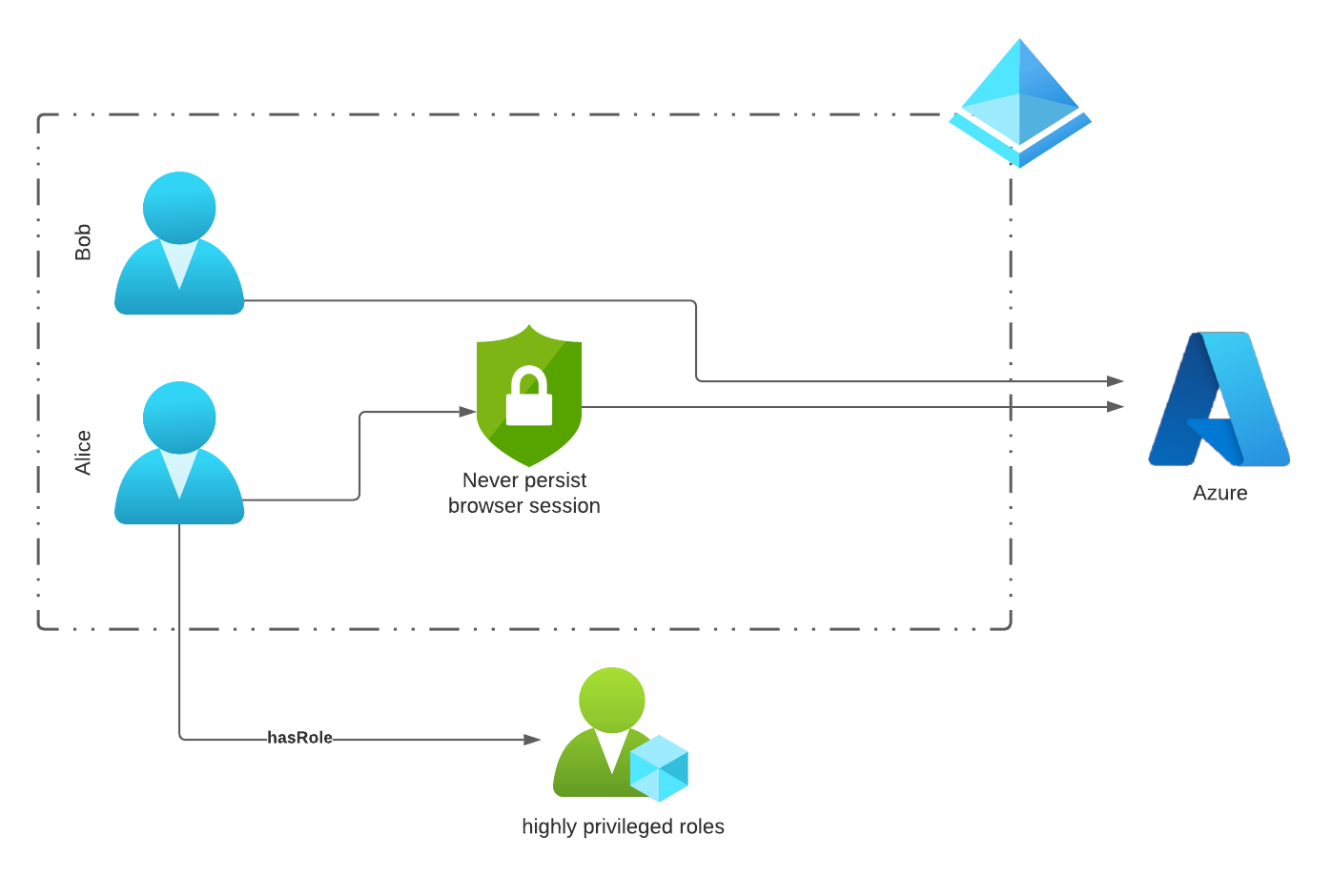
For users who are members of a highly privileged role, the sign-in in the browser should never be persistently stored. This is to prevent the credentials of an administrative account from being stored in the browser and thus possibly falling into the wrong hands.
The passwordless sign-in still allows for convenient sign-in, making the barrier for the administrator very low.
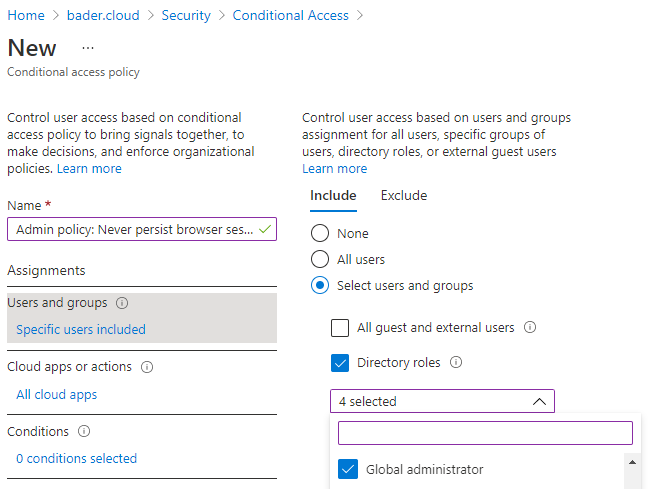
I define the following Entra ID (Azure AD) roles as highly privileged roles in my example.
- Global administrator
- Privileged role administrator
- Exchange administrator
- SharePoint administrator
How it works
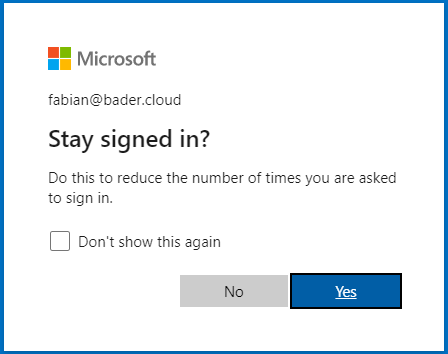
In the default setting, the user can select whether his login data should be stored in the form of a browser cookie when signing-in to the Azure portal, for example. The following prompt is displayed for this purpose.
The newly created CA policy takes the decision out of the user’s hands and prevents the cookie from being saved after the end of the browser session.
All users who are not members of one of the chosen administrative roles are not affected by this policy.
In the following example, Bob will still be able to perform a “persistent” sign-in, whereas Alice will have to sign-in with her account each time.
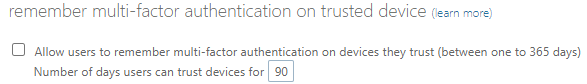
Legacy MFA portal
The following setting in the legacy MFA configuration must be disabled in order to use the Conditional Access method.
Admin policy: Never persist browser sessions
In the Azure Portal, select “Conditional Access” under Security and create a new policy.
- Use the Entra ID (Azure AD) Portal -> Security -> Conditional Access to create a new policy with the name “Admin policy: Never persist browser sessions”
- Select Assignments -> “Users and groups”
- Include: “Directory roles” -> Alle hochprivilegierte Rollen auswählen

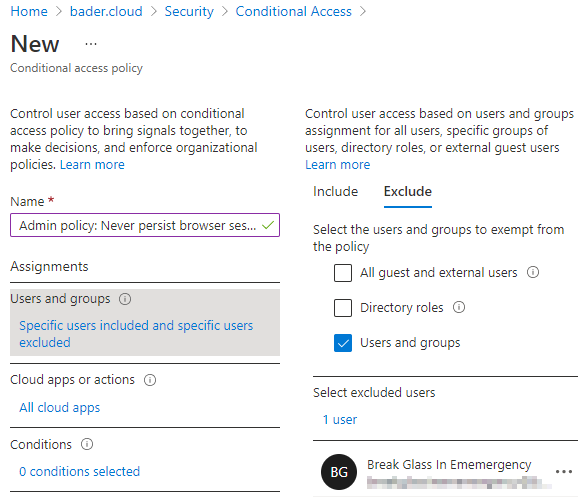
- Exclude: Break Glass Account

- Include: “Directory roles” -> Alle hochprivilegierte Rollen auswählen
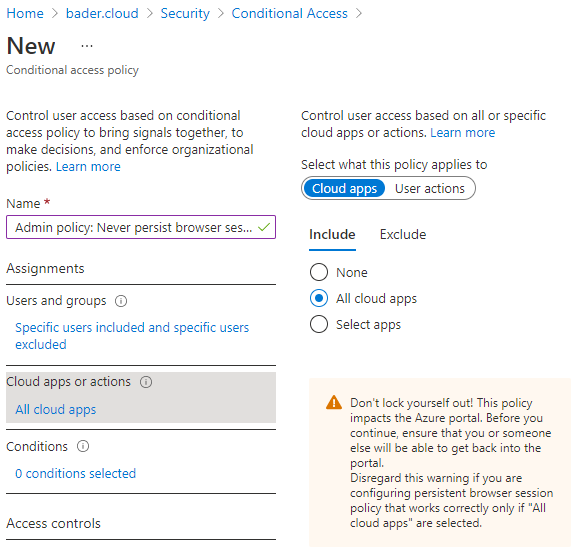
- Select Assignments -> “Cloud apps or actions” -> “All cloud apps”

- Do not change “Conditions” and “Access controls”
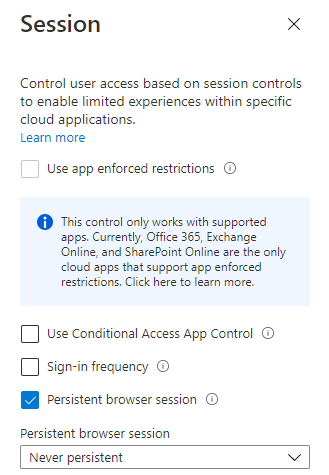
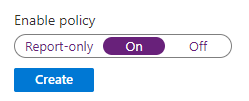
- Select Session and change “Persistent browser session” to “Never persistent”

- Finally, enable the policy and create it.

Enable combined security information registration
For the use of the new authentication methods one setting is mandatory. Enabling the combined registration of security information. Why enabling it is generally a very good idea and also really helps your users I described in this blogpost.
For those who already know the benefits or would like to make the adjustment easily, proceed as follows:
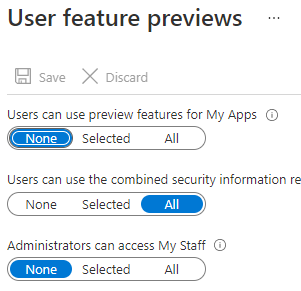
- On the Entra ID (Azure AD) portal select User settings
- Click on “Manage user feature preview settings”

- Enable “Users can use the combined security information registration experience” for all users and save the changes

Enable Authentication Methods
To enable passwordless sign-in at all, the following authentication methods must be enabled.
- FIDO2 Security Key
- Microsoft Authenticator
- Temporary Access Pass (preview)
The method “Text message (preview)” is not discussed in this blog series, because I think that for administrative accounts the sign-in via text message is not appropriate.
To enable these methods, you need to go to the Security section in the Entra ID (Azure AD) Portal.
Select Authentication methods and enable each of the mentioned methods.
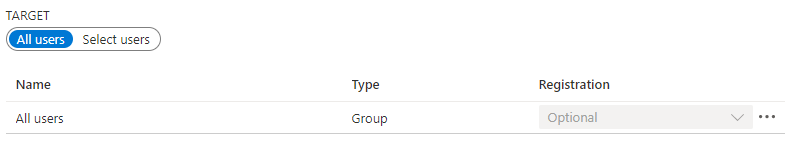
If desired, use can be restricted to individual user groups.
In the end, the overview should look like this:

Next steps
Now all the prerequisites are in place in the Tenant to be able to perform a passwordless sign-in. In the next blog we will take a look at the initial login without password.