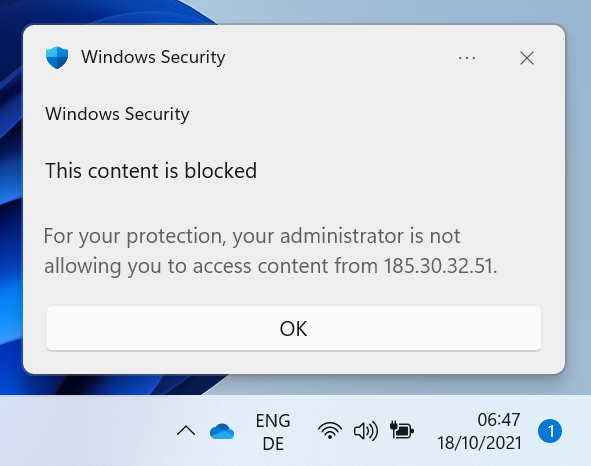
The Feodo Tracker from abuse.ch provides a list of active ip addresses that are used for C2 servers. With MDE and a bit automation you can easily block your clients connecting to those servers and get an alert if they do.
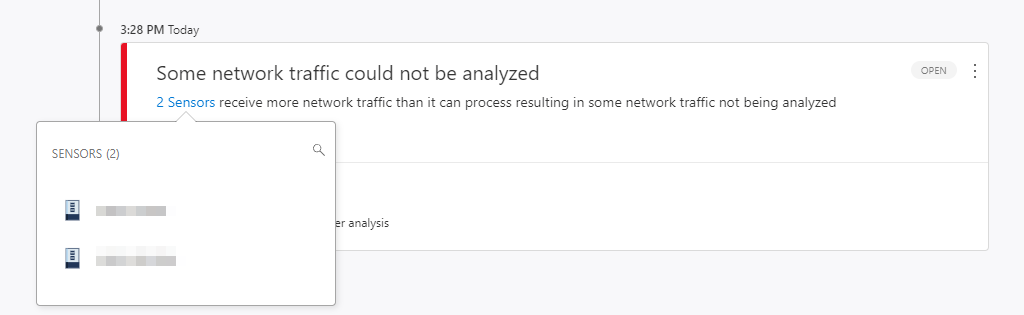
Microsoft Defender for Identity is a very useful tool for gaining deep insight into an Active Directory environment. The agents installed on each domain controller collect information directly from the server’s network traffic and forward it to Microsoft Defender.
For this analysis, the agent uses the WinPcap driver by default. This leads to the following error message on a Windows Server 2022 even under moderate load:
However, the CPU, RAM and network load of the affected domain controller is not particularly high.
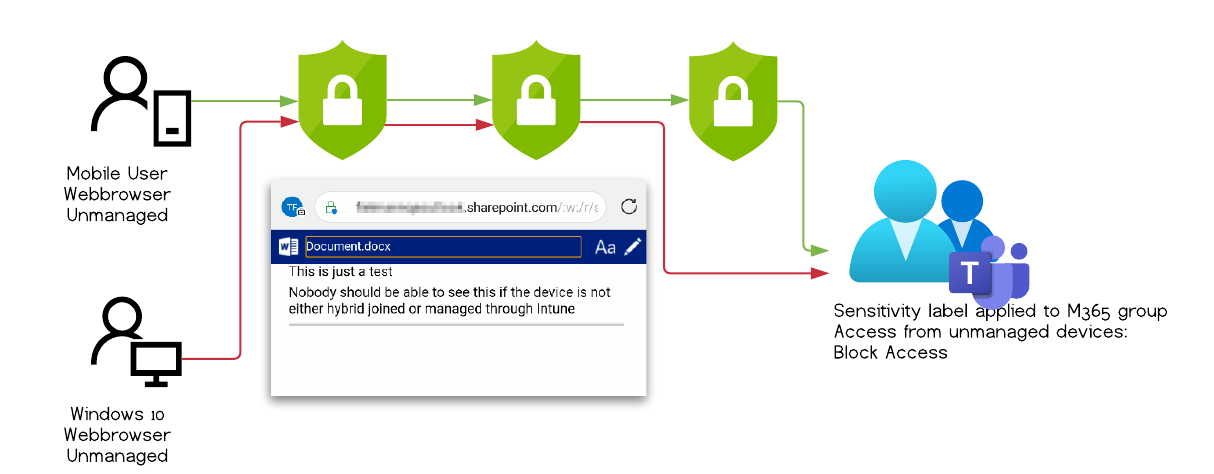
Vulnerability assesment by MSRC Severity Important Security Impact Security Feature Bypass Scope of the security vulnerability This article describes a security vulnerability that allowed an authenticated Microsoft 365 user to bypass additional protective measures based on sensitivity labels to download content to an unmanaged device. The user could not access files that she otherwise would not have access to.
Fixed The issue has now been fixed by Microsoft and it is no longer possible to reproduce this behavior.
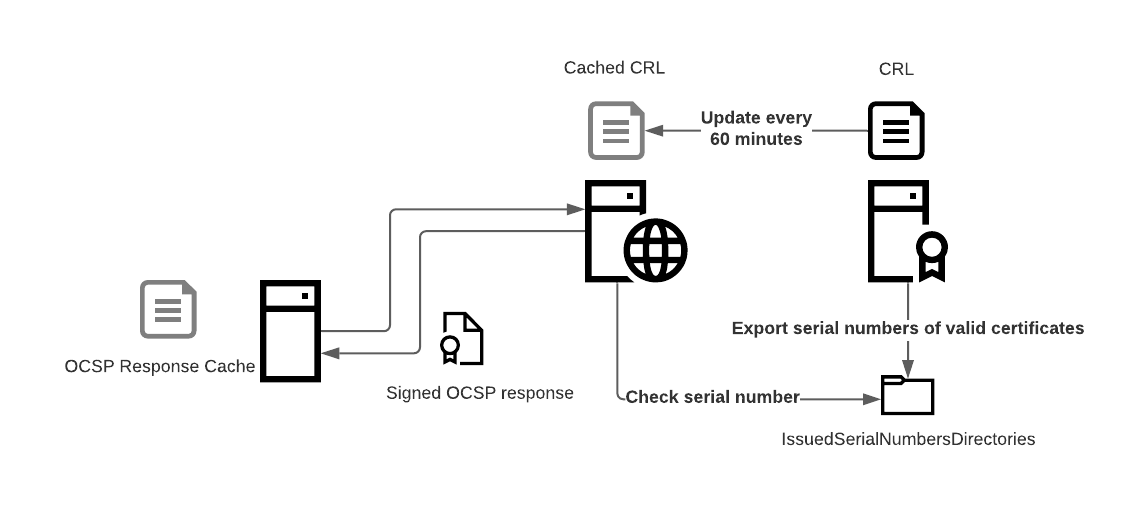
In this blog, I want to discuss one mitigation technique for the attack DPERSIST1 better known as “golden certificate”.
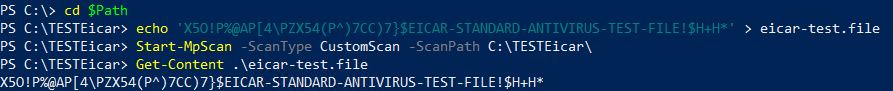
A user with administrative permissions is able to create Defender AV exclusions without using the Add-MPPrefence cmdlet. Because of the way the exclusion is created, most public guidelines and hunting queries on detecting this kind of change won’t detect it.
Even more troubling is the fact that Microsoft Defender for Endpoint will not log any of those changes made. Therefore it’s not easy to detect and could go undetected for security personnel which relies on those queries and products.
Officially Pulse Secure does not yet support Windows 11, but that doesn’t mean it won’t work.
However, it is not as easy as expected. The connection keeps getting disconnected after a few seconds. The manual solution which is described in the forum was a bit too “manual” for me.
Open the settings of the “Juniper Networks Virtual Adapter” Enable the “Juniper Network Service” network binding Since the virtual network card is automatically removed if the connection is not successful and then loses the setting, I have automated the steps via PowerShell.