TIL; Today I Learned TIL is a blog series in which I document (for me) interesting insights.
This knowledge is possibly already documented a hundred times on the Internet. But so i can find it again i wrote it down here.
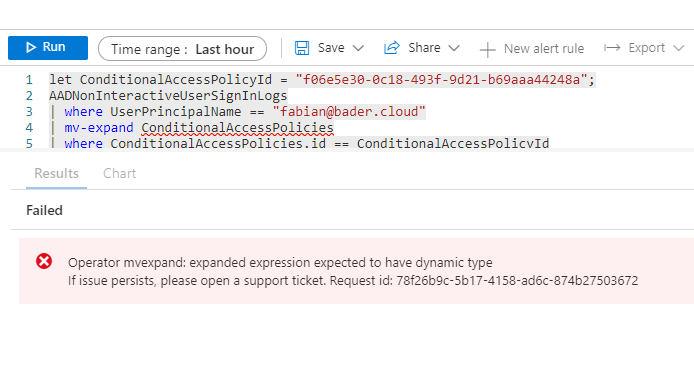
Microsoft has been preparing a fundamental change to the way sign-in logs are being displayed and stored for some time. This helps in the analysis of sign-in processes, as it distinguishes, for example, whether the user signs-in interactively or with a stored credential (non-interactive).
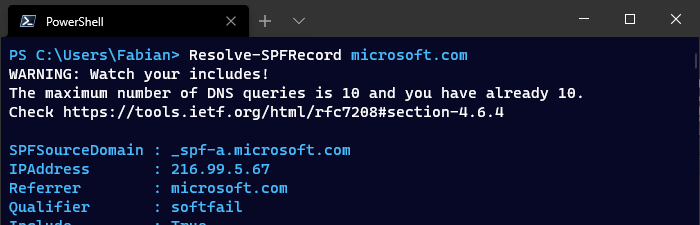
The increasingly widespread use of SaaS email service providers such as Exchange Online, G-Suite, Amazon SES, SendGrid and others is a challenge for email administrators. To prevent emails to customers from ending up in the spam filter or not being accepted at all, a proper configuration of DMARC, DKIM and SPF is mandatory.
Especially with SPF, it is easy to simply add all the ‘include’ entries of the third-party providers. However, this can also backfire if, for example, the maximum number of DNS lookups (10) or the maximum length of a TXT DNS record (255) is exceeded.
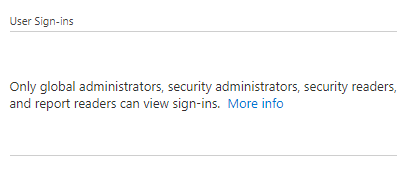
If you receive the following error message when accessing a user object in Entra ID (Azure AD), this can have several causes.
Failure Only global administrators, security administrators, security readers, and report readers can view sign-ins. The most obvious cause is: The necessary permissions are missing.
But what if the corresponding Entra ID (Azure AD) role groups have been assigned and are active?
Then it may be due to a issue with group-based role assignment (preview).
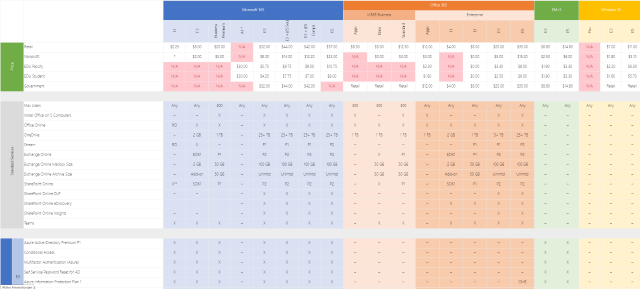
Microsoft 365 E3, Office 365 E3, Business Basic or F3? Which license package includes which features and how do the add-ons differ?
Microsoft’s license bundles are numerous and can quickly become confusing. Very few customers are likely to know all the features that their license package includes.
And even as a consultant, the question “Can I use feature x in plan y?” is not always answered ad hoc.
Dan Chemistruck of Infused Innovations has created a wonderful overview of the current Microsoft 365 plans and shares that information in this blog post or also as a (non-downloadable) Excel file.
On Tuesday, April 13th, I will be speaking at the Cloud Management User Group London virtual meetup. The topic of my talk is “Phase out Legacy Authentication”.
It is the first Meetup of the User Group and this is organized by Dean Ellerby, Andy Jones and Simon Lee. You can find the User Group on Twitter and Meetup.
Agenda Uhrzeit* 19:30 Welcome and introduction 19:45 Phasing out Legacy Authentication - Fabian Bader of Cloudbrothers.
The case of the... In this category I publish blog post explaining a problem and the solution but more important the analysis that lead to the root cause.
The name is a homage to “The Case of the Unexplained” from Mark Russinovich.
The error You are using the sign-in feature on a Windows virtual machine in Azure with Azure Active Directory authentication, and users receive the following error message when they sign-in.